Abstract
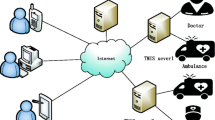
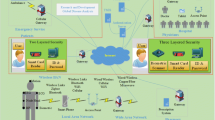
In 2009, Xu et al. presented an improved smartcard based authentication scheme while using a security model previously applied by Bellare et al. to prove the security of their authentication methods. Later on, in 2012, Wu et al. pointed out number of authentication attacks in Xu et al. scheme. To address these issues, Wu et al. presented a Smartcard based Two-Factor Authentication (2FA) scheme for Telecare Medical Information System (TMIS) facility. In this study, we prove that authentication scheme of Wu et al. is still vulnerable to impersonation attack, offline password guessing attack, forgery attack and many other attacks. Moreover, number of performance and verification issues are also outlined in the authentication scheme of Wu et al. To overcome these issues, an improved and enhanced 3FA Smartphone based authentication method is proposed on a Cloud Computing environment. The proposed scheme is further corroborated using Burrows-Abadi-Needham logic (BAN logic) nonce verification. The detailed BAN logic verification and further security analysis shows that the proposed authentication protocol is highly reliable and secure in terms of message verifications, message freshness and trustworthiness of its origin. Moreover, the comparative security, performance and feature analysis shows that the proposed work yields an even more improved and enhanced authentication framework as compared to Wu et al. authentication scheme.


Similar content being viewed by others
References
Alghamdi AS, Siddiqui Z, Quadri, SSA (2010) A common information exchange model for multiple C4I architectures. Computer Modelling and Simulation (UKSim), 2010 12th International Conference on. 24–26 March 2010 538–542
Alghamdi AS (2010) Common Information Framework b/w/ Defense Architectures, A Wen Semantics Approach
Siddiqui Z, Abdullah AH, Khan MK (2011) Qualified Analysis b/w ESB(s) Using Analytical Hierarchy Process (AHP) Method. Intelligent Systems, Modelling and Simulation (ISMS), 2011 Second International Conference on. 25–27 Jan 2011 100–104
Siddiqui Z, Khan MK, Alghamdi AS (2010) Node level information security in Common Information Exchange Model (CIEM). Sci Int 21:221–230
Siddiqui Z, Khan MK, Alghathbar K (2011) Analysis of enterprise service buses on information security, interoperability and high-availability using Analytical Hierarchy Process (AHP). J Phys Sci 6:35–42
Chen H-M, Lo J-W, Yeh C-K (2012) An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. J Med Syst 36(6):3907–3915
Jiang Q, Ma J, Ma Z, Li G (2013) A privacy enhanced authentication scheme for telecare medical information systems. J Med Syst 37(1):1–8
Siddiqui Z, Abdullah A, Khan M, Alghamdi AS (2013) Smart environment as a service: three factor cloud based user authentication for telecare medical information system. J Med Syst 38(1):1–14
Wei J, Hu X, Liu W (2012) An improved authentication scheme for telecare medicine information systems. J Med Syst 36(6):3597–3604
Eldefrawy MH, Khan MK, Alghathbar K, Kim T-H, Elkamchouchi H (2012) Mobile one-time passwords: two-factor authentication using mobile phones. Secur Commun Netw 5(5):508–516
Incorporation A (2013) Medical Application Built for iPhone Users
Jucheng Y, Naixue X, Vasilakos AV, Zhijun F, Dongsun P, Xianghua X, Sook Y, Shanjuan X, Yong Y (2011) A fingerprint recognition scheme based on assembling invariant moments for cloud computing communications. Syst J IEEE 5(4):574–583
Smith A (2013) Smartphone ownership–2013 update. Pew Research Center, Washington
Siddiqui Z, Alghamdi AS (2014) SOA based C4I common-view interoperability model. J Sci Int 26(1):175–180
Siddiqui Z, Alghamdi AS (2014) A universal view SOA interoperability framework for multiple C4I applications. J Sci Int 26(1):97–100
Hao X, Wang J, Yang Q, Yan X, Li P (2013) A chaotic map-based authentication scheme for telecare medicine information systems. J Med Syst 37(2):1–7
Yan X, Li W, Li P, Wang J, Hao X, Gong P (2013) A secure biometrics-based authentication scheme for telecare medicine information systems. J Med Syst 37(5):1–6
Xu J, Zhu W-T, Feng D-G (2009) An improved smart card based password authentication scheme with provable security. Comput Stand Interfaces 31(4):723–728
Bellare M, Pointcheval D, Rogaway P (2000) Authenticated key exchange secure against dictionary attacks. Advances in Cryptology—Eurocrypt 2000. Springer 139–155
Wu Z-Y, Lee Y-C, Lai F, Lee H-C, Chung Y (2012) A secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1529–1535
Burrows M, Abadi M, Needham RM (1871) A logic of authentication. Proc R Soc Lond A Math Phys Sci 1989(426):233–271
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. Advances in Cryptology—CRYPTO’99. Springer 388–397
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. Comp IEEE Trans 51(5):541–552
Acknowledgments
The authors acknowledge the support provided by the Research Center (RC), College of Computer & Information Sciences, King Saud University.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Siddiqui, Z., Abdullah, A.H., Khan, M.K. et al. Cryptanalysis and improvement of ‘a secure authentication scheme for telecare medical information system’ with nonce verification. Peer-to-Peer Netw. Appl. 9, 841–853 (2016). https://doi.org/10.1007/s12083-015-0364-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-015-0364-9