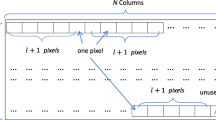
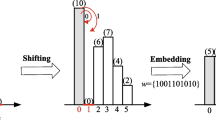
Abstract
The main purpose of this presented work is to develop a data embedding method based on a new digital image histogram modification approach. The proposed scheme fundamentally is concerned about the frequency of occurrence of the image brightness values of the cover image for the data embedding procedures. The proposed scheme effectively realizes both perceptual invisibility and statistical invisibility so that obtained covered images are highly robust against common perceptual and statistical steganalysis techniques. The scheme provides reasonably higher payload values than its counterparts, as well as providing comparatively improved PSNR results.












Similar content being viewed by others
References
Akar F and Varol H S 2004 A new RGB weighted encoding technique for efficient information hiding in images. J. Naval Sci. Eng. 2: 21–36
Bensghir T K and Altinsoy S O 2008 A corporate restructuring proposal for the management of cyber security in Turkey, 3rd International Conference on Information Security and Cryptology 1:14–20
Bui C N, Lee H Y, Joo J C and Lee H K 2010 Secure bit-plane based steganography for secret communication. IEICE Trans. Inf. Syst. E93.D(1): 79–86
Cetin O and Ozcerit A T 2009 A new steganography algorithm based on color histograms for data embedding into raw video streams. Comput. Secur. 28: 670–682
Chang C C, Lin C C and Chen Y H 2003 Reversible data-embedding scheme using differences between original and predicted pixel values. IET Inf. Secur. 2: 35–46
Chang C C and Lin C C 2006 Reversible steganography for VQ-compressed images using side matching and relocation. IEEE Trans. Inf. Forensic Secur. 1: 493–501
Chang C C, Tai W L and Chen K N 2008 Data hiding based on histogram modification for image authentication, IEEE/IFIP Int. Conf. Embed. Ubiquit. Comput. 1: 506–511
Chen C C and Chang C C 2008 LSB-based steganography using reflected gray code. IEICE Trans. Inf. Syst. E91.D(4): 1110–1116
Chrysochos E, Fotopoulos V, Skodras A and Xenos M 2007 Reversible image watermarking based on histogram modification, 11 th Panhellenic Conf. on Informatics with International Participation 1: 93–104
Cox I J and Miller M L 2008 The first 50 years of electronic watermarking. J. Appl. Signal Process. 16: 126–132
Fridrich J, Du R and Long M 2000 Steganalysis of LSB encoding in color images, IEEE Int. Conf. Multimed. Expo. (ICME) 3: 1279–1282
Hernandez-Castro J C, Blasco-Lopez I, Estevez-Tapiador and Ribagorda-Garnacho J M 2006 A Steganography in games: A general methodology and its application to the game of go. Comput. Secur. 25: 64–71
Huang H C and Fang W C 2008 Intelligent multimedia data hiding techniques and applications, IEEE Int. Conf. Inf. Secur. Assur. 1: 477–482
Khrisna S L V, Rahim B A, Shaik F and Rajan K S 2010 Lossless embedding using pixel differences and histogram shifting technique. IEEE Recent Adv. Space Technol. Serv. Clim. Chang. (RSTSCC) 1: 213–216
Lee C C, Wu H C, Tsai C S and Chu Y P 2008 Adaptive lossless steganographic scheme with centralized difference expansion. Pattern Recog. 41: 2097–2106
Lin C N and Chang C C 2007 A best-pair-first capacity-distortion control for data hiding on vq compression domain, IEEE International Conference on 3 rd Intelligent Information Hiding and Multimedia Signal Processing 1: 509–514
Lin C Y, Chang C C and Wang Y Z 2008 Reversible steganographic method with high payload for jpeg images. IEICE Trans. Inf. Syst. E91.D(3): 836–845
Netravali A N and Haskell B G 1995 Digital pictures: representation, compression and standards. Plenum Press, New York
Ni Z, Shi Y Q, Ansari N, SuW, Sun Q and LinW 2004 Robust lossless image data hiding. IEEE Int. Conf. Multimed. Expo. (ICME) 1: 2199–2202
Ni Z, Shi Y Q, Ansari N, Su W, Sun Q and Lin X 2008 Robust lossless image data hiding designed for semi-fragile image authentication. IEEE Trans. Circ. Syst. Video Technol. 18: 497–509
Petitcolas F A, Anderson R J and Kuhn M G 1999 Information hiding-A Survey. IEEE Spec. Issue Prot. Multimed. Content 87: 1061–1078
Provos N and Honeyman P 2003 Hide and Seek: An introduction to steganography. IEEE Secur. & Priv. Mag. 32–44
Rabbani M and Jones P W 1991 Digital image compression techniques. SPIE Optical Engineering Press, Washington
Sahin A, Bulus E, Sakalli M T and Bulus H N 2007 The grasp of the hidden information on images with the RQP steganalysis method, IX th Akademik Bilisim Conferences: 83–877 (In Turkish)
Sencar H T, Ramkumar M and Akansu A N 2004 Data hiding fundamentals and applications. Elsevier Academic Press, New York
Sevgi L 2001 11 September 2001 - Electronic wars, information security and national defense in changing world, Turkey: EMO special issue
Teng C Y, Shiau Y H and Chen C C 2010 A Data hiding algorithm based on histogram re-quantization, IEEE 5 th International Conference on Computer Sciences and Convergence Information Technology (ICCIT) 1: 1088–1091
Thanuja T C, Nagaraj R and Kumari M U 2008 Data hiding using increased peak histogram, IEEE Int. Workshop Data Min. Artif. Intell. (DMAI’08) 1: 44–47
Vleeschouwer C D, Delaigle J F and Macq B 2003 Circular interpretation of bijective transformations in lossless watermarking for media asset management. IEEE Trans. Multimedia 5: 97–105
Wang Z and Bovik A C 2002 A universal image quality index. IEEE Signal Proc. Lett. 9: 81–84
Wang Z, Bovik A C, Sheikh H D and Simoncelli E P 2004 Image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13: 600–612
Watters P A, Martin F and Stripf H S 2005 Visual steganalysis of LSB-encoded natural images, IEEE 3rd International Conference on Information Technology and Applications 1: 746–751
Yalman Y and Erturk I 2009 A new histogram modification based robust image data hiding technique, IEEE 24 th International Symposium on Computer and Information Sciences (ISCIS’09) 1: 39–43
Yalman Y 2010 Design and implementation of a steganography method based on histogram modification for digital images, Ph.D. Thesis, Kocaeli University, Institute of Natural Science, Kocaeli (In Turkish)
Yalman Y, Akar F and Erturk I 2012 Recent advances in steganography (Chapter 4: contemporary approaches to the histogram modification based data hiding techniques), InTech Open Access Publisher
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
YALMAN, Y., ERTURK, I. Secret data embedding scheme modifying the frequency of occurrence of image brightness values. Sadhana 39, 939–956 (2014). https://doi.org/10.1007/s12046-014-0239-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12046-014-0239-4