Abstract
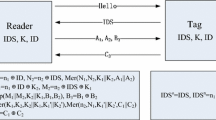
Recently, Wang et al. analyzed the security of two EPC C1–G2 compliant RFID authentication protocols, called RAPLT and \(\textit{SRP}^+\), and proved that these protocols are vulnerable against de-synchronization and secret disclosure attacks. The time complexity of their attacks were \(O(2^{16})\). In addition, they proposed an improved version of \(\textit{SRP}^+\) entitled \(\textit{SRP}^{++}\), for which they claim the security would be \(O(2^{32})\). However, in this letter, we analyze the security of \(\textit{SRP}^{++}\) and show that the complexity of retrieving all secret parameters of a given tag is \(O(2^{16})\), similar to its predecessor protocol.

Similar content being viewed by others
References
Beaulieu, R., Shors, D., Smith, J., Treatman-Clark, S., Weeks, B., & Wingers, L. (2013). The SIMON and SPECK families of lightweight block ciphers. Cryptology ePrint archive, Report 2013/404. http://eprint.iacr.org/
Black, J., Cochran, M., & Shrimpton, T. (2005). On the impossibility of highly-efficient blockcipher-based hash functions. In Cramer, R. (Ed.) Advances in cryptology—EUROCRYPT 2005, proceedings, volume 3494 of Lecture notes in computer science (pp 526–541). Springer
Gao, L., Ma, M., Shu, Y., Lin, F., Zhang, L., & Wei, Y. (2014). A low-cost RFID authentication protocol against desynchronization with a random tuple. Wireless Personal Communications, 79(3), 1941–1958.
Jeon, I.-S., & Yoon, E.-J. (2013). A new ultra-lightweight RFID authentication protocol using merge and separation operations. International Journal of Mathematical Analysis, 7(52), 2583–2593.
Liao, Y.-P., & Hsiao, C.-M. (2014). A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Networks, 18, 133–146.
Lin, I.-C., Hsu, H.-H., & Cheng, C.-Y. (2015). A cloud-based authentication protocol for RFID supply chain systems. Journal of Network and Systems Management, 23(4), 978–997.
Pang, L., He, L., Pei, Q., & Wang, Y. (2013). Secure and efficient mutual authentication protocol for RFID conforming to the EPC C-1 G-2 standard. In Wireless communications and networking conference (WCNC), 2013 IEEE (pp. 1870–1875) April 2013.
Peris-Lopez, P., Castro, J. C. H., Estévez-Tapiador, J. M., & Ribagorda, A. (2009). LAMED—a PRNG for EPC class-1 generation-2 RFID specification. Computer Standards & Interfaces, 31(1), 88–97.
Rogaway, P., & Steinberger, J. (2008). Security/efficiency tradeoffs for permutation-based hashing. In Smart, N. (Ed.) Advances in cryptology—EUROCRYPT 2008, proceedings, volume 4965 of Lecture notes in computer science (pp. 220–236). Springer
Safkhani, M., Bagheri, N., & Naderi, M. (2013). Strengthening the security of EPC C-1 G-2 RFID standard. Wireless Personal Communications, 72(2), 1295–1308.
Safkhani, M., Bagheri, N., & Naderi, M. (2014). A note on the security of IS-RFID, an inpatient medication safety. International Journal of Medical Informatics, 83(1), 82–85.
Wang, S., Liu, S., & Chen, D. (2015). Security analysis and improvement on two RFID authentication protocols. Wireless Personal Communications, 82(1), 21–33.
Zhuang, X., Zhu, Y., & Chang, C.-C. (2014). A new ultralightweight RFID protocol for low-cost tags: \(R^{2}AP\). Wireless Personal Communications, 79(3), 1787–1802.
Acknowledgments
This work was supported by Shahid Rajaee Teacher Training University under contract number 11541.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Safkhani, M., Hosseinzadeh, M., Namin, M.E. et al. On the (Im)Possibility of Receiving Security Beyond 2l Using an l-Bit PRNG. Wireless Pers Commun 92, 1591–1597 (2017). https://doi.org/10.1007/s11277-016-3623-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3623-z