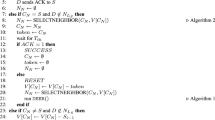Abstract
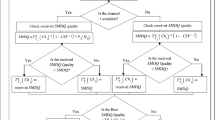
This paper proposes a new routing protocol for IEEE 802.11s wireless mesh network to overcome the problems associated with the conventional proactive and reactive routing approaches. The proposed ‘Selective Greedy’ (SelG) routing protocol operates in two phases. In the first phase it exploits the proactive mode of Hybrid Wireless Mesh Protocol, the standard routing protocol for IEEE 802.11s mesh, and constructs a set of potential forwarders for every mesh point, that can act as the next-hop relay. In the second phase, during the actual data communication, a candidate is selected from the set of potential forwarders based on a local optimization. The optimization procedure considers the statistical effect of local link quality fluctuation and interference over the global routing path selection. This way the SelG protocol reduces the control packet flooding in the network (a major drawback for reactive protocols). At the same time, the optimization procedure captures the network dynamics, and thus avoids the possibility of routing based on stale information (a drawback for proactive protocols). The routing properties and the correctness of the SelG protocol is established theoretically, and the performance of the protocol is analyzed through simulation results. The proposed protocol is implemented in an indoor wireless mesh testbed, and the performance is evaluated and compared with other traditional approaches.
























Similar content being viewed by others
Notes
In the IEEE 802.11 standard, a unit of time (TU) equals to \(1024\) \(\mu\)s
Only \(3\) non-overlapping channels are available for the most commercially used IEEE 802.11b/g physical layer. Though IEEE 802.11a and IEEE 802.11n have more number of non-overlapping channels, different countries apply their own regulations to the allowable channels.
In a mesh network, an end-to-end flow is defined as the communication between a specific (source,destination) pairs that are single or multiple hops away.
The difference between the link metric and the path metric should be noted. The link metric is the airtime link value between two MPs (using a specific interface for communication). The path metric is the aggregate of the link metric values for all the links in the path. The aggregation depends on the properties of the link metric values. Airtime link metric is additive in nature, and therefore the path metric is the sum of the individual link metrics.
Protocol interference model can not handle cumulative interference [23]. Therefore, the set of interfaces that introduce interferences due to cumulative power effect, can not be identified properly through MCCA broadcast messages. As a result, small error is observed in the set of interfering interfaces.
The minimum SINR value observed by a flow, indicates the minimum SINR value at the routers that may act as a forwarder for that flow. Therefore, for HWMP protocol, the minimum SINR value is observed at one of the routers in the routing path. However, for the SelG protocol, the router with the minimum SINR may be one of the candidates from the set of potential forwarders, and not necessarily be the routers in the actual routing path.
References
Open80211s: Open source implementation of IEEE 802.11s for Linux kernel. www.open80211s.org.
RaLink RT3352 series ieee 802.11n routers-on-chip. http://www.mediatek.com/_en/01_products/04_pro.php?sn=1006.
11s-2011 (2011). IEEE standard for information technology-telecommunications and information exchange between systems-local and metropolitan area networks-specific requirements part 11: Wireless LAN medium access control (MAC) and physical layer (PHY) specifications amendment 10: Mesh networking. IEEE Standard.
Abid, M. R., & Biaz, S. (2013). Airtime ping–pong effect characterization in IEEE 802.11s wireless mesh networks. Computing, 1–25. doi:10.1007/s00607-013-0374-5.
Abolhasan, M., Lipman, J. (2006). Self-selection route discovery strategies for reactive routing in ad hoc networks. In Proceedings of the first international conference on integrated internet ad hoc and sensor networks.
Afanasyev, M., Snoeren, A.C. (2009). The importance of being overheard: Throughput gains in wireless mesh networks. In Proceedings of the 9th ACM SIGCOMM conference on internet measurement conference (pp. 384–396).
Alicherry, M., Bhatia, R., & Li, L. E. (2006). Joint channel assignment and routing for throughput optimization in multiradio wireless mesh networks. IEEE Journal on Selected Areas in Communications, 24(11), 1960–1971.
Bahr, M. (2006). Proposed routing for IEEE 802.11s WLAN mesh networks. In: Proceedings of the 2nd international wireless internet conference.
Berg, J.E., Bownds, R., Lotse, F. (1992). Path loss and fading models for microcells at 900 mhz. In Proceedings of the IEEE 42nd vehicular technology conference (pp. 666–671).
Bezzina, A., Ayari, M., Langar, R., Kamoun, F. (2012). An interference-aware routing metric for multi-radio multi-channel wireless mesh networks. In Proceedings of the 2012 IEEE 8th international conference on wireless and mobile computing, networking and communications (pp. 284–291).
Boukerche, A., Zhang, Z. (2008). A hybrid-routing based intra-domain mobility management scheme for wireless mesh networks. In Proceedings of the 11th international Symposium on modeling, analysis and simulation of wireless and mobile systems (pp. 268–275).
Bruno, R., Conti, M., Pinizzotto, A. (2009). Capacity-aware routing in heterogeneous mesh networks: An analytical approach. In Proceedings of the 12th ACM international conference on modeling, analysis and simulation of wireless and mobile systems (pp. 73–81).
Campista, M. E. M., Esposito, P. M., Moraes, I. M., Costa, L., Duarte, O., Passos, D. G., et al. (2008). Routing metrics and protocols for wireless mesh networks. IEEE Network, 22(1), 6–12.
Chakraborty, S., Chakraborty, S., Nandi, S. (2013). Beyond conventional routing protocols: Opportunistic path selection for ieee 802.11s mesh networks. In Proceedings of the 24th annual IEEE international Symposium on personal, indoor and mobile radio communications.
Chakraborty, S., Nandi, S. (2014). Evaluating the effect of path diversity over QoS and QoE in a high speed indoor mesh backbone. In Proceedings of the sixth international conference on communication systems and networks (pp. 1–8).
Dhananjay, A., Zhang, H., Li, J., & Subramanian, L. (2009). Practical, distributed channel assignment and routing in dual-radio mesh networks. ACM SIGCOMM Computer Communication Review, 39(4), 99–110.
Draves, R., Padhye, J., Zill, B. (2004). Routing in multi-radio, multi-hop wireless mesh networks. In Proceedings of the 10th ACM annual international conference on mobile computing and networking (pp. 114–128).
Garroppo, R. G., Giordano, S., & Tavanti, L. (2012). A joint experimental and simulation study of the ieee 802.11s hwmp protocol and airtime link metric. International Journal on Communication Systems, 25(2), 92–110.
Gawedzki, I., & Al Agha, K. (2008). How to avoid packet droppers with proactive routing protocols for ad hoc networks. International Journal of Network Management, 18(2), 195–208.
Ghazisaidi, N., Assi, C. M., & Maier, M. (2012). Intelligent wireless mesh path selection algorithm using fuzzy decision making. Wireless Networks, 18(2), 129–146.
Gupta, P., & Kumar, P. (2000). The capacity of wireless networks. IEEE Transactions on Information Theory, 46(2), 388–404.
Hou, R., Lui, K.S., Chiu, H.S., Yeung, K.L., Baker, F. (2009). Routing in multi-hop wireless mesh networks with bandwidth guarantees. In Proceedings of the tenth ACM international Symposium on Mobile ad hoc networking and computing (pp. 353–354).
Iyer, A., Rosenberg, C., & Karnik, A. (2009). What is the right model for wireless channel interference? IEEE Transactions on Wireless Communications, 8(5), 2662–2671.
Jahanshahi, M., Dehghan, M., & Meybodi, M. R. (2013). Lamr: Learning automata based multicast routing protocol for multi-channel multi-radio wireless mesh networks. Applied Intelligence, 38(1), 58–77.
Jain, R., Chiu, D.M., Hawe, W. (1984). A quantitative measure of fairness and discrimination for resource allocation in shared computer systems. Tech. rep., Digital Equipment Corporation, DEC-TR-301.
Kandah, F., Zhang, W., Wang, C., & Li, J. (2012). Diverse path routing with interference and reusability consideration in wireless mesh networks. Mobile Networks and Applications, 17(1), 100–109.
Khatkar, A., Singh, Y. (2012). Performance evaluation of hybrid routing protocols in mobile ad hoc networks. In Proceedings of second international conference on advanced computing & communication technologies (pp. 542–545).
Khorov, E., Lyakhov, A., Safonov, A. (2011). Flexibility of routing framework architecture in IEEE 802.11s mesh networks. In Proceedings of the eight IEEE international conference on mobile ad-hoc and sensor systems (pp. 777–782).
Kim, W.S., Chung, S.H. (2013). Design of optimized AODV routing protocol for multi-interface multi-channel wireless mesh networks. In Proceedings of the IEEE 27th international conference on advanced information networking and applications (pp. 325–332).
Kodialam, M., Nandagopal, T. (2005). Characterizing the capacity region in multi-radio multi-channel wireless mesh networks. In Proceedings of the 11th ACM ACM annual international conference on mobile computing and networking (pp. 73–87).
Koksal, C. E., & Balakrishnan, H. (2006). Quality-aware routing metrics for time-varying wireless mesh networks. IEEE Journal on Selected Areas in Communications, 24(11), 1984–1994.
Kravitz, S. (1967). Packing cylinders into cylindrical containers. Mathematics Magazine, 40(2), 65–71.
Lee, J., Kim, W., Lee, S.J., Jo, D., Ryu, J., Kwon, T., Choi, Y. (2007). An experimental study on the capture effect in 802.11 a networks. In Proceedings of the second ACM international workshop on wireless network testbeds, experimental evaluation and characterization (pp. 19–26).
Lee, J., Ryu, J., Lee, S. J., & Kwon, T. T. (2010). Improved modeling of ieee 802.11 a phy through fine-grained measurements. Computer Networks, 54(4), 641–657.
Lim, A.O., Kado, Y., Zhang, B., Wang, X. (2007). A study of root driven routing protocol for wireless LAN mesh networks. In Proceedings of the 3rd international conference on wireless internet (pp. 3:1–3:10).
Mhatre, V., Lundgren, H., Baccelli, F., Diot, C. (2007). Joint MAC-aware routing and load balancing in mesh networks. In Proceedings of the ACM international conference on emerging networking experiments and technologies (pp. 19:1–19:12).
Mir, S., Pirzada, A.A., Portmann, M. (2008). HOVER: Hybrid on-demand distance vector routing for wireless mesh networks. In Proceedings of the thirty-first Australasian conference on computer science (pp. 63–71).
Mukherjee, T., Gupta, S.K.S., Varsamopoulos, G. (2007). Analytical model for optimizing periodic route maintenance in proactive routing for manets. In Proceedings of the 10th ACM Symposium on modeling, analysis, and simulation of wireless and mobile systems (pp. 201–208).
Natkaniec, M., Kosek-Szott, K., Szott, S., & Bianchi, G. (2013). A survey of medium access mechanisms for providing qos in ad-hoc networks. IEEE Communications Surveys & Tutorials, 15(2), 592–620.
de Oliveira, C.T., Theoleyre, F., Duda, A. (2012). Channel assignment strategies for optimal network capacity of IEEE 802.11s. In Proceedings of the 9th ACM international Symposium on performance evaluation of wireless ad hoc, sensor, and ubiquitous, networks (pp. 53–60).
Papadimitriou, C. H. (1981). On the complexity of integer programming. Journal of the ACM, 28(4), 765–768.
Paquereau, L., Helvik, B.E. (2010). Opportunistic ant-based path management for wireless mesh networks. In Proceedings of the 7th international conference on swarm intelligence (pp. 480–487).
Passos, D., & Albuquerque, C. V. N. (2012). A joint approach to routing metrics and rate adaptation in wireless mesh networks. IEEE/ACM Transactions on Networking, 20(4), 999–1009.
Pinheiro, M., Sampaio, S., Vasques, F., Souto, P. (2009). A DHT-based approach for path selection and message forwarding in IEEE 802.11s industrial wireless mesh networks. In Proceedings of the 14th IEEE international conference on emerging technologies and factory automation (pp. 1021–1030).
Qi, B., Shen, F., Raza, S. (2012). iBATD: A new routing metric for multi-radio wireless mesh networks. In Proceedings of the 9th international conference on information technology.
Qualnet 5.0.1 network simulator, http://www.scalable-networks.com/products/qualnet/.
Rafique, M.I., Porsch, M., Bauschert, T. (2011). Simple modifications in HWMP for wireless mesh networks with smart antennas. In Proceedings of the 17th EUNICE workshop on advances in communication networking (pp. 21–30).
Ramasubramanian, V., Haas, Z.J., Sirer, E.G. (2003). SHARP: A hybrid adaptive routing protocol for mobile ad hoc networks. In Proceedings of the 4th ACM international Symposium on mobile ad hoc networking & computing (pp. 303–314).
Roy, S., Garcia-Luna-Aceves, J.J. (2002). Node-centric hybrid routing for ad hoc networks. In Proceedings of the international workshop on mobility and wireless access.
Rozner, E., Seshadri, J., Mehta, Y., & Qiu, L. (2009). Soar: Simple opportunistic adaptive routing protocol for wireless mesh networks. IEEE Transactions on Mobile Computing, 8(12), 1622–1635.
Sadiq, U., Kumar, M., Wright, M. (2012). CRISP: Collusion-resistant incentive-compatible routing and forwarding in opportunistic networks. In Proceedings of the 15th ACM international conference on modeling, analysis and simulation of wireless and mobile systems (pp. 69–78).
Samar, P., Pearlman, M. R., & Haas, Z. J. (2004). Independent zone routing: An adaptive hybrid routing framework for ad hoc wireless networks. IEEE/ACM Transactions on Networking, 12(4), 595–608.
Sengul, C., Viana, A. C., & Ziviani, A. (2012). A survey of adaptive services to cope with dynamics in wireless self-organizing networks. ACM Computing Surveys, 44(4), 23:1–23:35.
Shi, Y., Hou, Y.T., Liu, J., Kompella, S. (2009). How to correctly use the protocol interference model for multi-hop wireless networks. In Proceedings of the tenth ACM international Symposium on Mobile ad hoc networking and computing (pp. 239–248).
Sobrinho, Ja L. (2002). Algebra and algorithms for qos path computation and hop-by-hop routing in the internet. IEEE/ACM Transactions on Networking, 10(4), 541–550.
Sobrinho, J.a.L. (2003). Network routing with path vector protocols: Theory and applications. In Proceedings of the 2003 conference on applications, technologies, architectures, and protocols for computer communications (pp. 49–60).
Tang, J., Xue, G., Zhang, W. (2005). Interference-aware topology control and QoS routing in multi-channel wireless mesh networks. In Proceedings of the 6th ACM international Symposium on mobile ad hoc networking and computing (pp. 68–77).
Thompson, M.S., MacKenzie, A.B., DaSilva, L.A. (2011). A method of proactive MANET routing protocol evaluation applied to the OLSR protocol. In Proceedings of the 6th ACM international workshop on Wireless network testbeds, experimental evaluation and characterization (pp. 27–34).
Waharte, S., Boutaba, R., Iraqi, Y., & Ishibashi, B. (2006). Routing protocols in wireless mesh networks: Challenges and design considerations. Multimedia Tools and Applications, 29(3), 285–303.
Wang, P., & Bohacek, S. (2007). An overview of tractable computation of optimal scheduling and routing in mesh networks. SIGMETRICS Performance Evaluation Review, 35(2), 18–20.
Ware, C., Chicharo, J., Wysocki, T. (2001). Simulation of capture behaviour in IEEE 802.11 radio modems. In Proceedings of the IEEE VTS 54th vehicular technology conference (Vol. 3, pp. 1393–1397).
Yang, L., Chung, S.H. (2012). HWMP+: An improved traffic load sheme for wireless mesh networks. In Proceedings of the 14th IEEE international conference on high performance computing and communications (pp. 722–727).
Zhou, N., Wu, H., Abouzeid, A.A. (2003). Reactive routing overhead in networks with unreliable nodes. In Proceedings of the 9th annual international conference on mobile computing and networking (pp. 147–160).
Acknowledgments
The works of Sandip Chakraborty is supported by TATA Consultancy Services, India through TCS Research Fellowship Program. The authors would like to thank Mr. Rajendra Singh, Skiva Technologies for providing necessary hardware and technical supports to implement the testbed.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Proof for theorem 1
The proof extends the concept provided in Lemma 1, given in [7], for protocol interference model in multi-interface mesh network. According to the protocol interference model, two interfaces interfere with each other, if they are at-most \(q \times R_c\) distance apart. Consider the following two cases,
-
Case I.
Assume \(I_i^k\) transmits. In this case, none of the interfaces in \(H(I_i^k)\) can transmit. Therefore,
$$\begin{aligned} Z(I^k_i)&= 1 \\ \sum \limits _{I^m_j \in H(I^k_i)}{Z(I^m_j)}&= 0 \end{aligned}$$This satisfies the inequality given in 2.
-
Case II.
Assume \(I_i^k\) does not transmit. In this case, two interfaces from \(H(I_i^k)\) can transmit, provided that they are at-least \(q \times R_c\) distance apart. Let us assume that there exists \({\mathfrak {S}}\) number of interfaces in \(H(I_i^k)\), who are at least \(q \times R_c\) distance apart. Considering the fact that all interfaces in \(H(I_i^k)\) must be within the disk centered at \(I_i^k\) and with radius \(q \times R_c\) (based of the protocol model consideration, interference range is at-most \(q \times R_c\)), the problem of finding \({\mathfrak {S}}\) can be reduced to the circle packing problem discussed in [32]. Let us consider Fig. 25. If \(MP_i\) does not use interface \(I_i^k\), then the interfaces of \(MP_u\) and \(MP_v\) can transmit simultaneously if they are at-least \(q \times R_c\) distance apart. Without considering the directionality of the interfaces, the problem of “finding maximum number of interfaces that can simultaneously transmit”, is similar to the problem of “finding maximum number of non-overlapping circles of radius \((q \times R_c)/2\) that can be packed within a circle of radius \(1.5 \times q \times R_c\)”. From [32], the value is \(7\). Therefore, for uniform distribution of the directional beams of the interfaces,
$$\begin{aligned} {\mathfrak {S}} \le \left( \frac{\alpha }{2\pi } \times 7 \approx 1.11364 \alpha \right) \end{aligned}$$where \(\alpha\) is the beam-width of the interface \(I_i^k\), expressed in radians. As a result,
$$\begin{aligned} Z(I^k_i)&= 0 \\ \sum \limits _{I^m_j \in H(I^k_i)}{Z(I^m_j)}&\le 1.11364\alpha \end{aligned}$$
This follows the theorem.
Appendix 2: Proof for theorem 2
Let \(\mathcal {Y}_i = \langle MP_j,I_i^k\rangle\) represent the optimal solution of Problem 1 for \(MP_i\). Instead of allowing \(\mathcal {Y}_i\) to take specific (MP, interface) value, let us define \(\mathcal {Y}_i\) to be a vector in \(\{\fancyscript{O}_1,\fancyscript{O}_2,...,\fancyscript{O}_k\}\), where each \(\fancyscript{O}_j\) takes a possible solution, and is represented by an integer value from \([0...k]\). Let this integer is chosen as follows: consider an equilateral simplex \(\Sigma _k\) in \(\mathbb {R}^{k-1}\) with vertices \(b_1,b_2,...,b_k\). Let \(c_k = \frac{b_1+b_2+...+b_k}{k}\) be the centroid of \(\Sigma _k\), and let \(\fancyscript{O}_j = b_j - c_k\) for \(1 \le j \le k\). Then problem 1 is represented as an integer semidefinite program with finite solution bound. From [41], the problem can be solved within \(O(k)\) time complexity by exploring all the elements in the vector \(\{\fancyscript{O}_1,\fancyscript{O}_2,...,\fancyscript{O}_k\}\). In the present scenario, \(k = |\mathbb {F}_i|\times |\Gamma _i|\). This follows the theorem.
Appendix 3: Proof for theorem 3
The airtime link metric value is additive in nature, and therefore it supports isotonicity. According to Algorithm 2, before broadcasting a PPREQ message, an MP, \(MP_i\), updates the path metric value as follows,
where \({{\mathfrak {P}}_{ij}^{k}}^*\) is the updated path metric value. Considering two sets \(\mathbb {A} \subseteq \mathbb {R}\) and \(\mathbb {B} \subseteq \mathbb {R}\), where \(\mathbb {R}\) is the set of real numbers. if \(\min \{x| x \in \mathbb {A}\} \le \min \{y| y \in \mathbb {B}\}\), then for any \(\omega \in \mathbb {R}\), following inequality always holds true.
Based upon this inequality, it can be easily seen that \({{\mathfrak {P}}_{ij}^k}^*\) is isotonic. During greedy selection, let us assume the link dispersion factor be \(\rho\). Considering \({{\mathfrak {P}}_{ij}^k}^* \le {{\mathfrak {P}}_{uv}^w}^*\) for two candidate forwarders \(\langle MP_j, I_j^k \rangle\) and \(\langle MP_v, I_u^w \rangle\), following inequalities always hold true.
Therefore the utility function, as given in Eq. (3), also follows the isotonicity property.
Appendix: Proof for theorem 4
The method of contradiction is used to proof the theorem. For the notational shorthand, let us use only the next-hop MP as the candidate from the set of potential forwarders, and imply that the corresponding interface is used. Let \({\mathfrak {P}}_i\) and \({\mathfrak {C}}_i\) denote the path metric and the link metric for the next hop \(MP_i\) respectively, with the implication of corresponding interfaces.
Let us assume that the greedy selection introduces a routing loop at \(MP_i\). Assume the routing loop be \(\{MP_i, MP_j, ..., MP_k, MP_i\}\). Because of the additive and non-zero properties of the airtime metric value,
\(\forall {i};\;\min \{{\mathfrak {P}}_i + {\mathfrak {C}}_i\} \in \mathbb {R}^+\), where \(\mathbb {R}^+\) is the set of positive real numbers. Therefore, the inequality given in Eq. (8) is never possible. This contradicts with our assumption.
Hence, the greedy selection never introduces a routing loop.
Rights and permissions
About this article
Cite this article
Chakraborty, S., Nandi, S. Selective greedy routing: exploring the path diversity in backbone mesh networks. Wireless Netw 20, 1995–2017 (2014). https://doi.org/10.1007/s11276-014-0724-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-014-0724-z