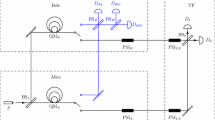
Abstract
Two efficient quantum private comparison (QPC) protocols are proposed, employing single photons and collective detection. In the proposed protocols, two distrustful parties (Alice and Bob) compare the equivalence of information with the help of a semi-honest third party (TP). Utilizing collective detection, the cost of practical realization is reduced greatly. In the first protocol, TP gains the result of the comparison. While in the second protocol, TP cannot get the comparison result. In both of our protocols, Alice and Bob only need be equipped with unitary operation machines, such as phase plates. So Alice and Bob need not to have the expensive quantum devices, such as qubit generating machine, quantum memory machine and quantum measuring machine. Security of the protocols is ensured by theorems on quantum operation discrimination.
Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. In: Proc. IEEE International Conference on Computers, Systems and Signal, Bangalore, India, pp. 175–179 (1984)
Ekert A.K.: Quantum cryptography based on Bell theorem. Phys. Rev. Lett. 67, 661–663 (1991)
Bennett C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Long G., Liu X.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65, 032302 (2002)
Jackson D.J., Hockney G.M.: Securing QKD links in the full Hilbert space. Quantum Inf. Process. 4, 35–47 (2005)
Brandt H.E.: Unambiguous state discrimination in quantum key distribution. Quantum Inf. Process. 4, 387–398 (2005)
El Allati A., El Baz M., Hassouni Y.: Quantum key distribution via tripartite coherent states. Quantum Inf. Process. 10, 589–602 (2011)
Shih H., Lee K., Hwang T.: New efficient three-party quantum key distribution protocols. IEEE J. Sel. Top. Quant. Electron. 15, 1602–1606 (2009)
Gao F., Qin S.J., Guo F.Z., Wen Q.Y.: Dense-coding attack on three-party quantum key distribution protocols. IEEE J. Quant. Electron. 47, 630–635 (2011)
Liu B., Gao F., Wen Q.Y.: Single-photon multiparty quantum cryptographic protocols with collective detection. IEEE J. Quant. Electron. 47, 1383–1390 (2011)
Nayak A.: Bit-commitment-based quantum coin flipping. Phys. Rev. A 67, 012304–012314 (2003)
Barrett J., Massar S.: Quantum coin tossing and bit-string generation in the presence of noise. Phys. Rev. A 69, 022322–022327 (2004)
Berlín G., Brassard G., Bussières F., Godbout N.: Fair loss-tolerant quantum coin flipping. Phys. Rev. A 80, 062321–062331 (2009)
Cleve R., Gottesman D., Lo H.-K.: How to share a quantum secret. Phys. Rev. Lett. 83, 648–651 (1999)
Hillery M., Buzěk V., Berthiaume A.: Quantum secret sharing. Phys. Rev. A 59, 1829–1834 (1999)
Karlsson A., Koashi M., Imoto N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59, 162–168 (1999)
Qin S.J., Gao F., Wen Q.Y., Zhu F.C.: Improving the security of multiparty quantum secret sharing against an attack with a fake signal. Phys. Lett. A 357, 101–103 (2006)
Yang Y., Wang Y., Chai H., Teng Y., Zhang H.: Member expansion in quantum (t,n) threshold secret sharing schemes. Opt. Commun. 284, 3479–3482 (2011)
Li Q., Long D.Y., Chan W.H., Qiu D.W.: Sharing a quantum secret without a trusted party. Quantum Inf. Process. 10, 97–106 (2011)
Shi R.H., Huang L.S., Yang W., Zhong H.: Asymmetric multi-party quantum state sharing of an arbitrary m-qubit state. Quantum Inf. Process. 10, 53–61 (2011)
Jia H.Y., Wen Q.Y., Song T.T., Gao F.: Quantum protocol for millionaire problem. Opt. Commun. 284, 545–549 (2011)
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS 82), Washington, DC, USA, p. 160 (1982)
Boudot F., Schoenmakers B., Traore J.: A fair and efficient solution to the socialist millionaires problem. Discr. Appl. Math. (Special Issue on Coding and Cryptology) 111(1–2), 23–36 (2001)
Lo H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1997)
Yang Y.G., Wen Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A-Math. Theor. 42, 055305 (2009)
Yang Y.G., Wen Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement (vol. 42, 055305, 2009). J. Phys. A-Math. Theor. 43, 209801 (2010)
Yang Y.G., Cao W.F., Wen Q.Y.: Secure quantum private comparison. Phsy. Scripta 80, 065002 (2009)
Chen X.B., Xu G., Niu X.X., Wen Q.Y., Yang Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1161–1165 (2009)
Lin J., Tseng H.Y., Hwang T.: Intercept-resend attacks on Chen et al.’s quantum private comparison protocol and the improvements. Opt. Commun. 284, 2212–2214 (2011)
Liu W., Wang Y.B., Jiang Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284, 3160–3163 (2011)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. doi:10.1007/s11128-011-0251-0 (2011)
Scherpelz P., Resch R., Berryrieser D., Lynn T.W.: Entanglement-secured single-qubit quantum secret sharing. Phys. Rev. A 84, 032303 (2011)
Wang G.M., Ying M.S.: Unambiguous discrimination among quantum operations. Phys. Rew. A 73, 042301 (2006)
D’Ariano M.G., Lo Presti P., Paris M.G.A.: Using entanglement improves the precision of quantum measurements. Phys. Rev. Lett. 87, 270404 (2001)
Gao F., Qin S.J., Wen Q.Y.: A simple participant attack on the Bradler-Dusek protocol. Quantum Inf. Comput. 7, 329 (2007)
Gisin N., Fasel S., Kraus B., Zbinden H., Ribordy G.: Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 73, 022320 (2006)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, B., Gao, F., Jia, Hy. et al. Efficient quantum private comparison employing single photons and collective detection. Quantum Inf Process 12, 887–897 (2013). https://doi.org/10.1007/s11128-012-0439-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-012-0439-y