Abstract
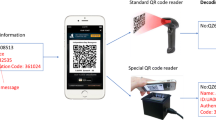
Quick Response (QR) code is widely used nowadays but its authenticity is an open issue. Attackers can easily replace the original barcode by a modified one which is generated through the standard encoder. This paper proposes to embed the authentication data such as message authentication code and cryptographic signature for QR code authentication. The scheme utilizes the redundancy of the error correction codewords to store the authentication data while still maintaining the default error correction capability. The stego barcode can be decoded by common users with a standard barcode decoder. The embedded data can be extracted with the knowledge of the barcode structure and the embedding process. The authenticity of the QR codes can then be verified off-line by the authorized user as and when needed. In our experiment, 100 % of the embedded data and encoded information can be retrieved correctly in the decodable barcodes with the off-the-shelf cameras. Security analysis shows that the proposed scheme is secure against attacks in tampering the barcode content. Compared with the existing data hiding scheme, the proposed method has much higher embedding capacity under the same error correction level.






Similar content being viewed by others
Notes
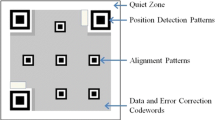
the smallest black/white blocks in a barcode as is shown in Fig. 1b.
References
Chen C Preprocessing and Authentication of 2D Barcodes, Ph.D. dissertation, School of Electrical and Electronic Engineering, Nanyang Technological University, Singapore, 2012, available at: http://hdl.handle.net/10356/54745
Villan R, Voloshynovskiy S, Koval O, Pun T (2006) Multilevel 2-D bar codes: Toward high-capacity storage modules for multimedia security and management. IEEE Trans Inf Forensics Secur 1(4):405–420
Park N, Lee W, Woo W Barcode-assisted planar object tracking method for mobile augmented reality. In: Proc. of International Symposium on Ubiquitous Virtual Reality, Jul. 2011, pp 40–43
Gao J, Kulkarni V, Ranavat H, Chang L, Mei H A 2D barcode-based mobile payment system. In: Proc. of International Conference on Multimedia and Ubiquitous Engineering, Jun. 2009, pp 320–329
Ebling M, Cáceres R (2010) Bar codes everywhere you look. IEEE Pervasive Comput 9:24–5
Kato H, Tan KT (2007) Pervasive 2D barcodes for camera phone applications. IEEE Pervasive Comput 6:476–85
Kieseberg P, Leithner M, Mulazzani M, Munroe L, Schrittwieser S, Sinha M, Weippl E (2010) QR code security. In: Proc. of the International Conference on Advances in Mobile Computing and Multimedia, pp 430–435
Jing Q, Vasilakos AV, Wan J, Lu J, Qiu D (2014) Security of the internet of things: Perspectives and challenges. Wirel Netw 20(8):2481–2501
Rowe RK (2011) Copy-resistant barcodesc. SPIE Newsroom
Wilds M, Chambers S Bar code authentication, Patent US 2010/0 012 736 A1, Jan., 2010
Eldefrawy M, Alghathbar K, Khan M Hardcopy document authentication based on public key encryption and 2D barcodes. In: Proc. of International Symposium on Biometrics and Security Technologies, Mar. 2012, pp 77–81
Li CM, Hu P, Lau WC Authpaper: Protecting paper-based documents and credentials using authenticated 2d barcodes. In: 2015 IEEE International Conference on Communications (ICC). IEEE, 2015, pp 7400–7406
Kishk S, Javidi B (2004) Robust and secure two-dimensional barcode system. Opt Eng 43(10):2256–2265
National retail federation return fraud survey results 2011. [Online]. Available: http://www.nrf.com/modules.phpname=Documents
Tzeng C-H, Tsai W-H (2003) A new approach to authentication of binary images for multimedia communication with distortion reduction and security enhancement. IEEE Commun Lett 7(9):443–445
Wu M, Liu B (2004) Data hiding in binary image for authentication and annotation. IEEE Trans Multimedia 6(4):528–538
Yang H, Kot A C (2007) Pattern-based data hiding for binary image authentication by connectivity-preserving. IEEE Trans Multimedia 9(3):475–486
Yang H, Kot AC, Rahardja S (2008) Orthogonal data embedding for binary images in morphological transform domain- a high-capacity approach. IEEE Trans Multimedia 10(3):339–351
Villán R, Voloshynovskiy S, Koval O, Vila J, Topak E, Deguillaume F, Rytsar Y, Pun T (2006). In: III EJD, Wong PW (eds) Text data-hiding for digital and printed documents: theoretical and practical considerations, vol 6072, p 607212. SPIE
Varna A, Rane S, Vetro A (2009) Data hiding in hard-copy text documents robust to print, scan and photocopy operations. In: Proc. of IEEE International Conference on Acoustics, Speech and Signal Processing, pp 1397–1400
Das S, Rane S, Vetro A Hiding information inside structured shapes. In: Proc. of IEEE International Conference on Acoustics Speech and Signal Processing, Mar 2010, pp 1782–1785
Reed IS, Solomon G (1960) Polynomial codes over certain finite fields. J Soc Ind Appl Math 8(2):300–304
Moreira J, Farrell P (2006) Essentials of Error-Control Coding. Wiley
(2006) Information technology–Automatic Identification and data capture techniques–QR Code 2005 bar code symbology,BS ISO/IEC 18004:2006, International Organization for Standardization
(2011) Information technology -Security techniques - Message Authentication Codes (MACs) Part 1: Mechanisms using a block cipher, BS ISO/IEC 9797-1:2011, International Organization for Standardization
Information technology -Security techniques - Message Authentication Codes (MACs) Part 2: Mechanisms using a dedicated hash function BS ISO/IEC 9797-2:2011 International Organization for Standardization (2011)
Information technology -Security techniques - Message Authentication Codes (MACs) Part 3: Mechanisms using a universal hash-function BS ISO/IEC 9797-3:2011 International Organization for Standardization (2011)
Black J, Halevi S, Krawczyk H, Krovetz T, Rogaway P UMAC: Fast and secure message authentication. In: Advances in Cryptology - CRYPTO’99, ser. Lecture Notes in Computer Science, M. Wiener, Ed. Springer Berlin Heidelberg, 1999, vol. 1666, pp 216–233
Krovetz T (2006) UMAC: Message Authentication Code using Universal Hashing. Request for Comments:4418
Arregoces M, Portolani M (2003) Data Center Fundamentals. Cisco Press
FIPS (2009) Digital signature standard. Ferderal Information Processing Standards Publication:186–3
Johnson D, Menezes A, Vanstone S (2001) The Elliptic Curve Digital Signature Algorithm (ECDSA). Int J Inf Secur 1:36–63
Hankerson D, Menezes A J, Vanstone S (2003) Guide to Elliptic Curve Cryptography. Secaucus, NJ, USA: Springer-Verlag New York, Inc.
Rivest R L, Shamir A, Adleman L (1978) A method for obtaining digital signatures and public-key cryptosystems. Commun ACM 21(2):120–126
Chen C, Marziliano P, Kot A C (2012) 2D finite rate of innovation reconstruction method for step edge and polygon signals in the presence of noise. IEEE Trans Signal Process 60(6):2851–2859
ZXing: multi-format 1D/2D barcode image processing library for Android, Java. [Online]. Available: http://code.google.com/p/zxing/
BoucyCastle.org: The Bouncy Castle Crypto APIs. [Online]. Available: http://www.bouncycastle.org/
Daemen J, Rijmen V (2002) The Design of Rijndael: AES - The Advanced Encryption Standard. Secaucus, NJ, USA: Springer-Verlag New York, Inc
Chen C, Marziliano P, Kot AC (2012) 2D Finite Rate of Innovation Reconstruction Method for Step Edge and Polygon Signals in the Presence of Noise. IEEE Trans Signal Process 60(6):2851–2859
Wen J, Zhu X, Li D (2013) Improved Bounds on the Restricted Isometry Constant for Orthogonal Matching Pursuit. Electron Lett 49:1487–1489
Wen J, Li D, Zhu F (2015) Stable Recovery of Sparse Signals via L p -Minimization. Appl Comput Harmon Anal 38:161–176
Acknowledgements
The authors would like to thank Prof. Alex C. Kot at NTU for valuable instructions and suggestions. He is also grateful to the Associate Editor and anonymous reviewers for the valuable comments and suggestions to improve the quality of the paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Preliminary version of this work has been presented in [1]. This work was supported by the NSFC (61402295, 61572329, 61001182), the Guangdong NSF Grant (2014A030313557, 2016A030313046), Fundamental Research Program of Shenzhen City (JCYJ20140418182 819173, JCYJ20150324141711690), and Faculty Startup Grant of Shenzhen University (2016052).
Rights and permissions
About this article
Cite this article
Chen, C. QR Code Authentication with Embedded Message Authentication Code. Mobile Netw Appl 22, 383–394 (2017). https://doi.org/10.1007/s11036-016-0772-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-016-0772-y