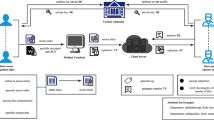
Abstract
Cloud-based Personal Health Record (PHR) in the electronic and information system has become next generation cloud platform for facilitating efficient, secure and scalable data access to foster the collaborative care. Data owner prefers to outsource their confidential electronic data to the cloud for effective retrieval and storage without provoking the depletion or losses due to data management and maintenance. Secure data sharing and searching are vital. Be that as it may, secure search for the outsourced data is a formidable errand, which may easily incur the leakage of sensitive personal information. In this research, we propose a novel diversified access control framework composed of User Usage Based Encryption (UUBE) which is normally based on the searchable encryption scheme. In the UUBE demonstrate, Usage is mapped as credential/accreditation with time allotment to each event, where the event is considered as security trait or a privacy attribute. Data user/client can decipher an event if and only if there is a match between the accreditation and credential related to the event. A searchable encryption enables efficient routing of encrypted events using data or feature extraction algorithm as an important technique. Multicredential routing is modelled as an event dissemination strategy to strengthen weak data user confidentiality. The data user is permitted to maintain the accreditations/credentials as per their usage category. Private keys are assigned to the user/client as labels with the accreditations or credentials. A data owner/proprietor associates and relates each enciphered event with a set of credentials.



Similar content being viewed by others
References
Baek, J., Safavi-Naini, R., and Susilo, W.: Public key encryption with keyword search revisited. In: Proc. International Conference on Computational Science and Its Applications (ICCSA), Vol. 5072, p. 12491259, Springer, 2008.
Bethencourt, J., Sahai, A., and Waters, B.: Ciphertext-Policy Attribute-Based Encryption. Security and Privacy IEEE Symposium on, IEEE pp. 321–334, 2007
Chase, M.: Multi-authority attribute based encryption. In: Proceedings of the 4th conference on Theory of cryptography, Berlin, pp. 515–534, 2007
Chase, M., and Chow, S.S.: Improving privacy and security in multi-authority attribute-based encryption. In: Proceedings of the 16th ACM Conference on Computer and Communications Security, ACM, pp. 121–130, 2009
Fukunaga, K., Introduction to Statistical Pattern Recognition. London: Academic Press, 1991.
Ghani, M.K., and Wen, L.C.: The design of flexible pervasive electronic health record (PEHR), Humanities, Science and Engineering (CHUSER), 249–254, 2011
Karakoyunlu, D., Gurkaynak, F., Sunar, B., and Leblebici, Y., Efficient and side-channel-aware implementations of elliptic curve cryptosystems over prime fields. IET Inf. Secur. 4(1):30–43 , 2010.
Li, M., Yu, S., Zheng, Y., Ren, K., and Lou, W., Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 24(1):131–143, 2013.
Liu, P., Wang, J., Ma, H., and Nie, H.: Efficient Verifiable Public Key Encryption with Keyword Search Based on KP-ABE. In: Ninth International Conference on Broadband and Wireless Computing, Communication and Applications, IEEE, pp. 584–589, 2014
Lohr, H., Sadeghi, A.R., and Winandy, M.: Securing the e-health cloud. In: Proceedings of the 1st ACM International Health Informatics Symposium, pp. 220–229, 2010
Lv, Z., Zhang, M., and Feng, D.: Multi-user searchable encryption with efficient access control for cloud storage. In: IEEE 6th International Conference on Cloud Computing Technology and Science, pp. 366–373. IEEE, Singapore, 2014.
Miller, V.S., and Williams, H.C., Use of elliptic curves in cryptography. Advances in Cryptology - CRYTO ’85 128:417–426, 1985.
Pandey, O., Goyal, V., Sahai, A., and Waters, B.: Attribute-based encryption for fine-grained access control of encrypted data. In: Proceedings of the 13th ACM Conference on Computer and Communications Security, pp. 89–98, 2006
Peleg, M., Beimel, D., Dori, D., and Denekamp, Y., Situation-based access control: Privacy management via modeling of patient data access scenarios. J. Biomed. Inform. 41(6):1028–1040, 2008.
Mehta, P., Bansal, M., and Upadhyaya, A.: Stream cipher and block cipher based performance analysis of symmetric cryptography algorithms: AES and DES In: International Journal of Modem Trends in Engineering and Research, vol. 2, no. 7, 2015
Sagar, B., Vhatkar, P.A., and Gajwani, J.: Towards Secure and Dependable Storage Services in Cloud Computing. International Journal of Innovative Research in Advanced Engineering (IJIRAE) ISSN: 2349-2163. 57–64, 2014
Smitha, S., Squicciarini, A.C., and Lin, D., Ensuring distributed accountability for data sharing in the cloud. IEEE Trans. Dependable Secure Comput. 9(4):556–568, 2012.
Tim, M., Kumaraswamy, S., and Latif, S., Cloud Security and Privacy, p. 95472. Sebastopol: O’Reilly Media, 2009.
Yinlai, J., Hayashi, I., and Wang, S., Knowledge acquisition method based on singular value decomposition for human motion analysis. IEEE Trans. Knowl. Data Eng. 26(12):3038–3050, 2014.
Tiayni, Z., Weidong, L., and Jiaxing, S.: An Efficient role based access control system for cloud computing, In: 11th IEEE International Conference on Computer and Information Technology, 2011
Acknowledgements
I would like to thank THE LORD MY SAVIOR for guiding and showering HIS blessings throughout my life. I take immense pleasure in thanking my guide Dr. M. Lilly Florence for rendering her valuable knowledge and guidance. I would like to thank my husband for his love and support. I would like to thank my parents and my son for their patience and care.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection on Wearable Computing Techniques for Smart Health
Rights and permissions
About this article
Cite this article
Suresh, D., Florence, M.L. Securing Personal Health Record System in Cloud Using User Usage Based Encryption. J Med Syst 43, 171 (2019). https://doi.org/10.1007/s10916-019-1301-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-019-1301-x