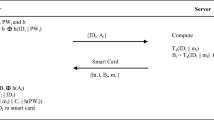
Abstract
With the development of Internet, patients could enjoy health-care delivery services through telecare medicine information systems (TMIS) in their home. To control the access to remote medical servers’ resources, many authentication schemes using smart cards have been proposed. However, the performance of these schemes is not satisfactory since modular exponential operations are used in these schemes. In the paper, we propose a chaotic map-based authentication scheme for telecare medicine information systems. The security and performance analysis shows our scheme is more suitable for TMIS.


Similar content being viewed by others
References
Istepanian, R. S. H., Jovanov, E., and Zhang, Y. T., Guest editorial introduction to the special section on M-health: Beyond seamless mobility and global wireless health-care connectivity. IEEE Trans. Inf. Technol. Biomed. 8(4):405–414, 2004.
Latré, B., Braem, B., Moerman, I., Blondia, C., and Demeester, P., A survey on wireless body area networks. J. Wireless Netw. 17(1). January 2011.
Wu, Z.-Y., Lee, Y.-C., Lai, F., Lee, H.-C., and Chung, Y., A secure authentication scheme for Telecare medicine information systems. J. Med. Syst., 2010. doi:10.1007/s10916-010-9614-9.
He, D., Chen, J., and Zhang, R., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst., 2011. doi:10.1007/s10916-011-9658-5.
Wei, J., Hu, X., and Liu, W., An Improved Authentication Scheme for Telecare Medicine Information Systems. J. Med. Syst., 2012. doi:10.1007/s10916-012-9835-1.
Zhu, Z., An Efficient Authentication Scheme for Telecare Medicine Information Systems. J. Med. Syst., 2012. doi:10.1007/s10916-012-9856-9.
Kocher, P., Jaffe, J., Jun, B., Differential power analysis. Proc. Adv. Cryptology (CRYPTO 99), pp. 388–397, 1999.
Messerges, T., Dabbish, E., and Sloan, R., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Tseng, H., Jan, R., Yang, W., A chaotic maps-based key agreement protocol that preserves user anonymity. IEEE Int. Conf. Commun. (ICC09), 2009; p.1–6.
Yujun, N., and Xingyuan, W., An anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear. Sci. Numer. Simulat. 16(4):1986–1992, 2011.
Xue, K., and Hong, P., Security improvement on an anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simulat., 2011. doi:10.1016/j.cnsns.2011.11.025.
Guo, C., and Chang, C., Chaotic Maps-Based Password-Authenticated Key Agreement Using Smart Cards. Commun. Nonlinear Sci. Numer. Simulat., 2012. doi:10.1016/j.cnsns.2012.09.032.
Wang, X., and Zhao, J., An improved key agreement protocol based on chaos, Communications in Commun. Nonlinear. Sci. Numer. Simulat. 15:4052–4057, 2010.
Bergamo, P., Arco, P., Santis, A., and Kocarev, L., Security of public key cryptosystems based on Chebyshev polynomials. IEEE. Trans. Circ. Syst. I 52:1382–1393, 2005.
Zhang, L., Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos. Soliton. Fract. 37(3):669–674, 2008.
Li, X., Qiu, W., Zheng, D., Chen, K., and Li, J., Anonymity enhancement on robust and efficient password-authenticated key agreement using smart cards. IEEE Trans. Ind. Electron. 57(2):793–800, 2010.
Acknowledgments
The authors thank Prof. R.R. Grams and the anonymous reviewers for their valuable comments. This research was supported by the National Natural Science Foundation of China (Nos. 61201180, 61001127), the Beijing Municipal Natural Science Foundation (N0.4132055), and the Excellent Young Scholars Research Fund of Beijing Institute of Technology.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hao, X., Wang, J., Yang, Q. et al. A Chaotic Map-based Authentication Scheme for Telecare Medicine Information Systems. J Med Syst 37, 9919 (2013). https://doi.org/10.1007/s10916-012-9919-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-012-9919-y