Abstract
The pentagram map, introduced by R. Schwartz, is a birational map on the configuration space of polygons in the projective plane.
We study the singularities of the iterates of the pentagram map. We show that a “typical” singularity disappears after a finite number of iterations, a confinement phenomenon first discovered by Schwartz. We provide a method to bypass such a singular patch by directly constructing the first subsequent iterate that is well-defined on the singular locus under consideration. The key ingredient of this construction is the notion of a decorated (twisted) polygon, and the extension of the pentagram map to the corresponding decorated configuration space.
Similar content being viewed by others
1 Introduction
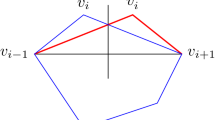
The pentagram map, introduced by R. Schwartz [10], is a geometric construction which produces one polygon from another. Successive applications of this operation (cf. Fig. 1) define a discrete dynamical system that has received considerable attention in recent years (see, e.g., [2, 5, 6, 9, 11]) due to its integrability properties and its connections to moduli spaces and cluster algebras. This paper is devoted to the study of singularity confinement for the pentagram map, a phenomenon first observed experimentally by Schwartz. Informally speaking, a singularity of a map at a point is said to be confined if some higher iterate of the map is well-defined at that point. We investigate singularities of the pentagram map and prove confinement in several cases.
The pentagram map is typically defined for objects called twisted polygons described by Schwartz [9]. A twisted polygon is a sequence A=(A i ) i∈ℤ of points in the projective plane that is periodic modulo some projective transformation ϕ, i.e., A i+n =ϕ(A i ) for all i∈ℤ. We will place the additional restriction that every quadruple of consecutive points of A be in general position, meaning that no three of the four may be collinear. Two twisted polygons A and B are said to be projectively equivalent if there exists a projective transformation ψ such that ψ(A i )=B i for all i. Let \(\mathcal{P}_{n}\) denote the space of twisted n-gons modulo projective equivalence.
It is convenient also to allow the vertices of a twisted polygon to be indexed by \(\frac{1}{2}+\mathbb{Z}\) instead of ℤ. Let \(\mathcal{P}_{n}^{*}\) denote the space of twisted n-gons indexed by \(\frac{1}{2} + \mathbb{Z}\), modulo projective equivalence.
The pentagram map, denoted T, inputs a twisted polygon A and constructs a new twisted polygon B defined by \(B_{i} = \overleftrightarrow{A_{i-\frac{3}{2}} A_{i+\frac{1}{2}}} \cap \overleftrightarrow{A_{i-\frac{1}{2}} A_{i+\frac{3}{2}}}\). Note that if A is indexed by ℤ then B is indexed by \(\frac {1}{2}+\mathbb{Z}\) and vice versa. The pentagram map preserves projective equivalence, so it induces maps

Schwartz [9] gives coordinates x 1,…,x 2n defined generically on \(\mathcal{P}_{n}\) and related coordinates also denoted x 1,…,x 2n on \(\mathcal{P}_{n}^{*}\). These are naturally ordered cyclically, so let x i+2n =x i for all i∈ℤ. Expressed in these coordinates, the maps α 1 and α 2 take a simple form.
Proposition 1.1
[9, (7)]
Suppose that (x 1,…,x 2n ) are the x-coordinates of A. If \(A \in \mathcal{P}_{n}^{*}\) then
Alternately, if \(A \in\mathcal{P}_{n}\) then
We will be interested in T k, the kth iterate of the pentagram map. Defined on \(\mathcal{P}_{n}\) it takes the form \(T^{k} = \underbrace {\cdots\circ\alpha_{2} \circ\alpha_{1} \circ\alpha_{2}}_{k}\) and has image in either \(\mathcal{P}_{n}\) or \(\mathcal{P}_{n}^{*}\) depending on the parity of k. By (1) and (2), T k is a rational map. The purpose of this paper is to better understand the singularities of the pentagram map and its iterates. For us, a singular point of a rational map is an input at which one of the components of the map has a vanishing denominator.
Let \(A \in\mathcal{P}_{n}\) be a singular point of the pentagram map. Then typically A will be a singular point of T k for all k less than some m, but not of T m. This phenomenon is known as singularity confinement and was identified by Grammaticos, Ramani, and Papageorgiou [3] as a feature common to many discrete integrable systems. Now, the pentagram map is a discrete integrable system as proven by Ovsienko, Schwartz, and Tabachnikov [5, 6], Soloviev [11], and Gekhtman, Shapiro, Tabachnikov, and Vainshtein [4]. That singularity confinement holds in this setting has been observed experimentally by Schwartz. The current paper seeks to understand singularity confinement for the pentagram map from both an algebraic and geometric perspective.
Algebraically, (2) suggests that a polygon \(A \in\mathcal {P}_{n}\) is a singular point of the pentagram map whenever x 2i (A)x 2i+1(A)=1 for some i∈ℤ. To check how many steps the singularity persists, one must determine for which k the rational expression for T k has a vanishing denominator at the given point. We use generating function formulas for these denominators from [2] to better understand when this occurs.
What we discover is that the behavior of a singularity seems to depend on the set S of integers i for which x 2i (A)x 2i+1(A)=1. We call S the type of the singularity and attempt to understand when singularity confinement holds for generic polygons of a given type. The simplest case is when S consists of a single element, in which event the singularity is confined to two iterations (i.e. A is a singular point of T and T 2 but not of T 3). More generally, suppose S is a finite arithmetic progression with common difference equal to 1 or 2. We prove that generic singularities of these types are confined to l+1 steps where l is the size of the arithmetic progression.
We do not have as complete an understanding of the situation for other singularity types. If the number of sides n of the polygon is odd, we show that singularity confinement holds generically for every type except the worst case S={1,…,n}. In addition we have an upper bound for the number of iterations such singularities last. The case of n even seems to be more complicated and we only have a conjectural answer as to which types exhibit singularity confinement.
From a geometric perspective, the condition x 2i (A)x 2i+1(A)=1 indicates that the triple of vertices A i−2, A i , and A i+2 are collinear. Although one can construct B=T(A) in this case, the result will violate the condition that quadruples of consecutive vertices be in general position. In fact, \(B_{i-\frac{3}{2}}\), \(B_{i-\frac{1}{2}}\), \(B_{i+\frac{1}{2}}\), and \(B_{i+\frac{3}{2}}\) will be collinear making it impossible to carry the construction any further. The notion of singularity confinement also has a geometric interpretation. If A has a singularity which vanishes after m steps, then one can approximate A by nonsingular polygons, apply the construction T m to them, and take a limit to find T m(A). Since A is a regular point of T m, the result of this procedure does not depend on the approximations of A.
Our main result on the geometric side is a straightedge construction of the first defined iterate T m(A) of a polygon A of certain singularity types. The basic idea is to fix, up to the first order, a family of approximations of A by nonsingular polygons. The data needed to accomplish this are encoded by a collection of points and lines which we call a decoration of A. With this done, the iterates between A and T m(A) become well-defined. To determine T m(A), we iterate a procedure which constructs these intermediate polygons one by one.
This paper is organized as follows. Section 2 reviews previous work on the pentagram map, including a non-recursive formula for T k as a rational map of the x-coordinates. This map factors into polynomials, some properties of which are given in Sect. 3. Section 4 identifies a hierarchy of singularity types of the pentagram map and establishes that generic polygons of these types exhibit singularity confinement. The remainder of the paper addresses the problem of moving past singularities by constructing T m(A) from A when A is a singular point of T,T 2,…,T m−1. An approach which works for the simplest singularity type is given in Sect. 5 along with a discussion of its limitations in handling more severe singularities. Section 6 introduces decorated polygons which will serve as the underlying objects of the main construction. In Sect. 7 we develop the procedure which is iterated in our main construction. Section 8 states the main construction itself and discusses what is needed to prove its correctness for a given singularity type. All algorithms are stated explicitly, but some contain steps which are nontrivial to accomplish via a straightedge construction. In the Appendix we fill in the details for these steps.
The following notation will be used throughout. If a,b,k∈ℤ, a≤b, k≥1 and a≡b(modk) then let [a,b] k denote the arithmetic progression
Twisted polygons will be denoted by capital letters with individual vertices indexed by either ℤ or \(\frac{1}{2} + \mathbb {Z}\). The sides of a polygon (i.e. lines passing through two consecutive vertices) will be denoted by the corresponding lowercase letter and indexed using the opposite indexing scheme. For instance, if A is a twisted polygon indexed by ℤ then its vertices are denoted A i for i∈ℤ and its sides are denoted \(a_{j} = \overleftrightarrow{A_{j-\frac{1}{2}} A_{j+\frac{1}{2}}}\) for \(j \in (\frac{1}{2} + \mathbb{Z})\).
2 Pentagram map background
The cross ratio of four real numbers a,b,c,d is defined to be
This definition extends to the projective line, on which it gives a projective invariant of four points. We will be interested in taking the cross ratio of four collinear points in the projective plane, or dually, the cross ratio of four lines intersecting at a common point. To be consistent with notation from [2], let χ(a,b,c,d) denote the cross ratio taken in a different order: χ(a,b,c,d)=[b,a,c,d].
Let A be a twisted polygon. The x-coordinates of A are defined by Schwartz [9] as follows. For each index k of A let

where \(B=\overleftrightarrow{A_{k-2} A_{k-1}} \cap\overleftrightarrow {A_{k} A_{k+1}}\), \(C=\overleftrightarrow{A_{k-1} A_{k}} \cap \overleftrightarrow{A_{k+1} A_{k+2}}\), and \(D=\overleftrightarrow {A_{k-2} A_{k-1}} \cap\overleftrightarrow{A_{k+1} A_{k+2}}\) (see Fig. 2). Now x j+2n =x j for all j∈ℤ, and as mentioned in the introduction, x 1,…,x 2n give a set of coordinates on \(\mathcal{P}_{n}\) and on \(\mathcal{P}_{n}^{*}\).
In [2], we work with related quantities called the y-parameters and denoted y j for j∈ℤ. These parameters are defined on \(\mathcal{P}_{n}\) by
and on \(\mathcal{P}_{n}^{*}\) by
We have y j+2n =y j for all j due to the analogous property of the x j . However, y 1,…,y 2n do not give a set of coordinates as they satisfy the single relation y 1 y 2⋯y 2n =1.
The y-parameters can equivalently be defined using cross ratios (see Fig. 3). For each index k of A


where \(B=\overleftrightarrow{A_{k-2} A_{k-1}} \cap\overleftrightarrow {A_{k} A_{k+1}}\) and \(E=\overleftrightarrow{A_{k} A_{k+1}} \cap \overleftrightarrow{A_{k+2} A_{k+3}}\).
The y-parameters transform under the pentagram map according to the Y-pattern dynamics of a certain cluster algebra. We used results of Fomin and Zelevinsky [7] to give formulas for the iterates of the pentagram map in terms of the F-polynomials F j,k of this cluster algebra. These can be defined recursively by F j,−1=F j,0=1 and
for k≥0 where
Theorem 2.1
[2, Theorems 4.2 and 1.2]
Let \(A \in\mathcal{P}_{n}\), x j =x j (A), and y j =y j (A). Then


The F-polynomials are polynomials in the y j (hence Laurent polynomials in the x j ) with positive coefficients. They have a simple combinatorial description as generating functions of order ideals of certain posets P k , which were first studied by Elkies, Kuperberg, Larsen, and Propp [1]. Specifically, let Q k to be the set of triples (r,s,t)∈ℤ3 such that |r|+|s|≤k−2, r+s≡k(mod2), and
Note that Q k and Q k+1 are disjoint. Let P k =Q k+1∪Q k . Define a partial order on P k by saying that (r′,s′,t′) covers (r,s,t) if and only if t′=t+1 and |r′−r|+|s′−s|=1. The partial order on P k restricts to a partial order on Q k . Let J(P k ) denote the set of order ideals of P k . The Hasse diagrams for P 2 and P 3 are given in Fig. 4.
Theorem 2.2
[2, Theorem 6.6]
3 The F-polynomials
According to (1) and (2), the pentagram map has singularities for polygons with x j x j+1=1, i.e., y j =−1, for some j. According to (6), the iterate T k has a singularity whenever F j,k−1=0 or F j,k =0 for some j. In this section we examine under which circumstances having y j =−1 for certain j forces an F-polynomial to vanish. Results along these lines will indicate how many steps a given singularity persists.
For the purpose of this section, relax the assumptions y i+2n =y i for all i and y 1 y 2⋯y 2n =1. Instead consider the F j,k as polynomials in the countable collection of variables {y i :i∈ℤ}. By way of notation, if S⊆ℤ let F j,k | S be the polynomial in {y i :i∈ℤ∖S} obtained by substituting y i =−1 for all i∈S into F j,k .
An alternating sign matrix is a square matrix of 1’s, 0’s, and −1’s such that
-
the non-zero entries of each row and column alternate in sign and
-
the sum of the entries of each row and column is 1.
Let ASM(k) denote the set of k by k alternating sign matrices.
Elkies, Kuperberg, Larsen, and Propp [1] establish connections between alternating sign matrices and the posets P k and Q k . Specifically, they give a bijection from ASM(k) to J(Q k ). Alternating sign matrices A∈ASM(k) and B∈ASM(k+1) are called compatible if the corresponding order ideals I∈J(Q k ), J∈J(Q k+1) have the property that I∪J is an order ideal of P k =Q k ∪Q k+1. Compatible pairs of alternating sign matrices are in bijection with J(P k ).
We will not explicitly state the bijection between ASM(k) and J(Q k ). Instead, we will list the needed properties of the bijection in the following two lemmas. Each of these statements can easily be deduced from results of [1].
Lemma 3.1
Let A∈ASM(k). Suppose that A has m entries equal to 1, namely entries (i 1,j 1),(i 2,j 2),…,(i m ,j m ). Then there are 2m alternating sign matrices B∈ASM(k+1) compatible with A. Moreover, there exist an order ideal J 0∈J(Q k+1) and elements (r 1,s 1,t 1),…,(r m ,s m ,t m )∈Q k+1∖J 0 such that
-
The map (i,j)↦(i+j−k−1,−i+j) sends (i 1,j 1),…,(i m ,j m ) to (r 1,s 1),…,(r m ,s m ).
-
An order ideal J∈J(Q k+1) corresponds to a matrix B compatible with A if and only if
$$ J_0 \subseteq J \subseteq J_0 \cup\bigl \{(r_1,s_1,t_1),\ldots ,(r_m,s_m,t_m) \bigr\} $$
By way of notation, let B 0=B 0(A)∈ASM(k+1) be the matrix corresponding to the order ideal J 0 from the lemma.
Lemma 3.2
Let A∈ASM(k) and suppose that a 11=a kk =1. This implies a 1k =a k1=0. Let A′∈ASM(k) be identical to A except on the corners where \(a'_{11} = a'_{kk} = 0\) and \(a'_{1k} = a'_{k1} = 1\). Let B=B 0(A) and B′=B 0(A′).
-
Let I,I′∈J(Q k ) be the order ideals corresponding to A and A′, respectively. Then I⊆I′, and I′∖I contains exactly one element (r,s,t) for each r,s with |r|+|s|≤k−2 and r+s≡k(mod2).
-
Let J,J′∈J(Q k+1) be the order ideals corresponding to B and B′, respectively. Then J⊆J′, and J′∖J contains exactly one element (r,s,t) for each r,s with |r|+|s|≤k−1, r+s≡k+1(mod2), and s≠±(k−1).
Define the weight of an alternating sign matrix A with respect to an integer j to be
where I∈J(Q k ) is the order ideal corresponding to A. By (8) we have
where the sum is over all compatible pairs A∈ASM(k), B∈ASM(k+1). Recall that r+s≡k(mod2) for (r,s,t)∈Q k . Therefore \(\operatorname{wt}(A,j)\) is a monomial in {y i :i≡j+k(mod2)} while \(\operatorname{wt}(B,j)\) is a monomial in {y i :i≡j+k+1(mod2)}.
Proposition 3.3
Proof
We need to show for each fixed A∈ASM(k) that
where the sum is over B compatible with A. By Lemma 3.1, both sides have 2m terms where m is the number of 1’s in A. Moreover, the lowest degree term of both sides is \(\operatorname {wt}(B_{0}(A),j)\). Let J 0 be the order ideal corresponding to B 0(A). If a il =1 then Lemma 3.1 says that it is possible to add some (r,s,t) with r=i+l−k−1 and s=l−i to J 0 to get a new order ideal J corresponding to a matrix B compatible with A. Computing:

By Lemma 3.1, this can be done for arbitrary subsets of the set of 1’s of A, so the proposition follows. □
Let S be a set of integers. Say that a matrix A∈ASM(k) avoids (S,j) if j+2i+4l−3k−3∉S for all (i,l) with a il =1. As i and l range from 1 to k, the index j+2i+4l−3k−3 takes on values in the k by k array
Hence, A avoids (S,j) if and only if the entries of A equal to 1 avoid the entries of this array contained in S.
Let S be a set of integers. Then we can use (9) to compute F j,k | S by substituting y i =−1 for all i∈S. If some A∈ASM(k) does not avoid (S,j) then the corresponding term of the sum will have a factor 1+y i for some i∈S. Hence this whole term will vanish in F j,k | S .
Corollary 3.4
Fix j and k, and let S⊆{i:i≡j+k+1(mod2)}. Then
where the sum is over those A∈ASM(k) which avoid (S,j). In particular, if no such A exists then F j,k | S ≡0.
Unfortunately, if there do exist matrices A∈ASM(k) avoiding (S,j), then it is not safe to conclude that \(F_{j,k}|_{S} \not\equiv 0\). Indeed, recall that \(\operatorname{wt}(B_{0}(A),j)\) is a monomial in {y i :i≡j+k+1(mod2)}. When we substitute y i =−1 for i∈S, a sign is introduced. It is therefore possible that different terms of (11) cancel with each other. We can at least conclude that \(F_{j,k}|_{S} \not\equiv0\) if there exists a unique A avoiding (S,j).
Proposition 3.5
Fix l∈[−(k−1),k−1]2. Let S⊆ℤ be either
-
1.
[j+l−2(k−1),j+l+2(k−1)]4 or
-
2.
[j+2l−(k−1),j+2l+(k−1)]2.
Then F j,k | S ≡0.
Proof
Suppose S=[j+l−2(k−1),j+l+2(k−1)]4. Then S consists precisely of the elements of some row of (10). Every A∈ASM(k) must have at least one entry equal to 1 in this row by the definition of alternating sign matrices. So by Corollary 3.4, F j,k | S ≡0. Similarly S=[j+2l−(k−1),j+2l+(k−1)]2 corresponds to a column of (10), so the same result holds. □
Lemma 3.6
Fix l∈[−(k+1),k+1]2 and let
Then the set of entries of (10) contained in {j+l−2k,j+l+σ,j+l+2k} corresponds to the 1’s of a permutation matrix.
Proof
Consider a “knight’s path” in a k by k matrix which starts at some entry in the first column and moves one column right and two rows up each step. Suppose the rows are ordered cyclically so whenever the knight passes the top of the matrix it wraps around to the bottom. Continue until the knight reaches the last column placing 1’s everywhere it visits. One possible resulting matrix for k=7 is
The wrap-arounds divide the path into three segments (one of which might have length zero). The entries of (10) are constant along each segment, and differ by 2k between consecutive segments. If k is odd then the result is a permutation matrix, and the 1’s correspond to entries of the array equal to j+l−2k, j+l, or j+l+2k for some l. One can check that the set of values of l that arise in this manner is precisely [−(k+1),k+1]2.
If k is even then the resulting matrix will not be a permutation matrix, but one can be obtained by shifting the 1’s of the middle segment either up or down by one row. For instance, in the following example with k=6 the middle segment is shifted down:
The effect on the corresponding entry of the array is accounted for by adding σ. □
Proposition 3.7
Fix l∈[−(k+1),k+1]2 and let
for σ as in Lemma 3.6. Let A be the permutation matrix from the conclusion of Lemma 3.6. Then
for some nonnegative integers a,b,c with a+b+c=k. In particular, \(F_{j,k}|_{S} \not\equiv0\).
Proof
By Lemma 3.6, all entries of (10) are contained in S except those corresponding to the 1’s of A. On the one hand, this means that A avoids (S,j). On the other hand, let A′∈ASM(k) be any matrix avoiding (S,j). Each column of A′ must have at least one entry equal to 1, and 1’s can only occur away from elements of S. So each column of A′ must have exactly one 1 and it must be in the same place as a 1 of A. As each column of A′ has only a single 1, there cannot be any −1’s, so in fact A′=A. Hence A is the only element of ASM(k) avoiding (S,j). The proposition follows from Corollary 3.4, where a, b, and c are the sizes of the three segments of the knight’s path as defined in the proof of Lemma 3.6. □
Corollary 3.8
Fix l∈[−(k+1),k+1]2 and let S be any of
-
1.
S=[j+l−2k+4,j+l+2k−4]4,
-
2.
S=[j+l−2k+2,j+l+σ−2]2, or
-
3.
S=[j+l+σ+2,j+l+2k−2]2.
for σ as above. Then \(F_{j,k}|_{S} \not\equiv0\).
Proof
Each S is contained in the corresponding one from Proposition 3.7. As fewer substitutions are made, F j,k | S remains nonzero. □
Corollary 3.9
Let S be a finite arithmetic sequence such that
-
|S|<k,
-
consecutive terms of S differ by 4 or 2, and
-
the elements of S have the same parity as j+k+1.
Then \(F_{j,k}|_{S} \not\equiv0\).
Proof
We may assume without loss of generality that S⊆[j−3(k−1),j+3(k−1)]1, as those are the indices of the only y-variables that F j,k depends on. In this case, S is contained in some S from Corollary 3.8 so we still have \(F_{j,k}|_{S} \not\equiv0\). □
Proposition 3.5 and Corollary 3.9 give a complete picture as to when F j,k | S ≡0 for S of the form [a,b]4 or [a,b]2. We will use these results to prove confinement for certain singularity types in the next section. There, we will assume that n is large relative to |S| so that the relations among the y-variables do not enter into play. In contrast, the following proposition pertains to a more severe singularity type, so we will reintroduce those relations at this point.
Proposition 3.10
Suppose that n is odd and S=[2,2n−2]2. Assume that y i+2n =y i for all i∈ℤ, y i =−1 for all i∈S, and y 1⋯y 2n =1. Let j,k∈ℤ with j+k odd and k∈{n,n+1}. Then evaluated at this input, F j,k ≠0 provided y 0≠−1 and y i ≠0 for all i.
Proof
First suppose that k=n, which implies that k is odd and j is even. Then in Proposition 3.7, σ=0. Moreover, we can choose l∈[−(k+1),(k+1)]2 such that l≡−j(mod2n). So
By Proposition 3.7 we have
for some monomial M in y 1,…,y 2n . Since y 0≠−1 and no y i is zero, we have F j,k ≠0.
Now let k=n+1, in which case k is even and j is odd. Since y i+2n =y i for all i, we can consider the entries of (10) modulo 2n. For example, if n=7, k=8, and j=3 the result is
Since n is odd, each row and each column contains each of 0,2,4,…,2n−2 with a single repeat, namely the first and last entry. We are interested in matrices A∈ASM(k) whose 1’s avoid S and hence all correspond to elements of the array equal to 0. There are two cases. If j≠n, then the corner entries of the array are nonzero. This is the situation in the above example. There will always be a single row and column in the interior of the array that each start and end with 0. Every other row and column will have a single 0. There is a unique alternating sign matrix A avoiding (S,j) in this case. It has 1’s everywhere there is a 0 in the array, and a single −1 where needed. The matrix A corresponding to the above example is
This matrix will always have n+2 entries equal to 1, so by Corollary 3.4 we have
where M is a monomial.
Lastly, if j=n (still assuming k=n+1) then the corner entries of the array all equal 0. In the case n=7 this looks like
In general, there will be two alternating sign matrices avoiding (S,j), both permutation matrices. For n=7 they are
Call these A and A′, respectively, and let B=B 0(A), B′=B 0(A′). By Corollary 3.4 we have
Now, Lemma 3.2 determines how the order ideals corresponding to A, A′, B, and B′ relate to each other. Using this result, one can check that the weights are related by

Consequently,
where \(M = \operatorname{wt}(A,j)\operatorname{wt}(B,j)\). Now, y 0 y 1 y 2⋯y 2n−1=1 and y 2=y 4=⋯=y 2n−2=−1 so
□
4 Singularity patterns
For i∈ℤ let
For \(j \in(\frac{1}{2} + \mathbb{Z})\) let
The reason for the different notation is as follows.
Lemma 4.1
[2, Lemma 7.2]
Let \(A \in\mathcal{P}_{n}\), i∈ℤ, \(j \in(\frac{1}{2} + \mathbb{Z})\).
-
1.
A∈X i if and only if A i−2, A i , and A i+2 are collinear.
-
2.
A∈Y j if and only if a j−2, a j , and a j+2 are concurrent.
Define in the same way subvarieties \(X_{j} \subseteq\mathcal{P}_{n}^{*}\) for \(j \in(\frac{1}{2} + \mathbb{Z})\) and \(Y_{i} \subseteq\mathcal {P}_{n}^{*}\) for i∈ℤ.
For S⊆ℤ or \(S \subseteq(\frac{1}{2} + \mathbb {Z})\) let

For instance, X {3,5}=X 3∩X 5 is the set of twisted polygons A for which A 1,A 3,A 5,A 7 are all collinear. On X S , we have y 2i =−1 for all i∈S. Therefore we can replace the F j,k in (6) with F j,k |2S where 2S={2i:i∈S}. If all of these restricted polynomials are nonzero, then the corresponding iterate of the pentagram map is defined generically on X S .
Theorem 4.2
Let i,m∈ℤ with 1≤m<n/3−1. Let

Then the map T k is singular on X S for 1≤k≤m+1, but T m+2 is nonsingular at generic A∈X S . Moreover, T m+2(A)∈Y S′ for such A.
In words, the theorem says that if A is a twisted polygon such that
are collinear then A is a singular point of the first m+1 iterates of the pentagram map. Moreover, a generic such A is not a singular point of T m+2 and the sides
of B=T m+2(A) pass alternately through two points.
Lemma 4.3
F j,m |2S ≡0 for all j∈2S′.
Proof
Suppose j∈2S′. Then j=2i−l for some l∈[−(m−1),m−1]2. Hence 2S=[j+l−2(m−1),j+l+2(m−1)]4. So by Proposition 3.5 we have F j,m |2S ≡0. □
Lemma 4.4
\(F_{j,k}|_{2S} \not\equiv0\) for all j,k∈ℤ with k∈{m+1,m+2} and j+k odd.
Proof
This would seem to follow immediately from Corollary 3.9. The only difficulty is that the assumption y i+2n =y i was relaxed in that section. Recall that F j,k depends only on those y i for i∈[j−3(k−1),j+3(k−1)]1, a total of 6k−5 consecutive variables. We are assuming that k≤m+2<n/3+1 so 6k−5≤2n. It follows that assuming y i+2n =y i has no effect on the y-variables appearing in F j,k . □
Proof of Theorem 4.2
By Lemma 4.3 and (6) we find that T m+1 and T m are singular on X S . This same lemma applied to smaller m implies that all T k with k<m are also singular on X S .
Now let k=m+2. Then Lemma 4.4 shows that none of the factors in the expression (6) for T k are identically zero. Hence (6) defines T m+2 generically on X S . It remains to show that the image is in Y S′. Let A∈X S be such that B=T m+2(A) is defined and let y j =y j (A) for all j∈ℤ. Let j∈S′ be given. By Lemma 4.3, F 2j,m =0. Therefore by (5)
Rearranging and using (7)

This is justified because T m+2(A) is defined so the factors being divided by are nonzero. We have y 2j (B)=−1 for all j∈S′ so B∈Y S′ as desired. □
The roles of S and S′ can be interchanged in Theorem 4.2. This is apparently an instance of projective duality.
Theorem 4.5
Let S and S′ be as in Theorem 4.2. Then the map T k is singular on X S′ for 1≤k≤m+1, but T m+2 is nonsingular at generic A∈X S′. Moreover, T m+2(A)∈Y S for such A.
Proof
The proof is essentially obtained by switching S and S′ throughout in the proofs of Theorem 4.2 and its lemmas. The only difference is that the proof now utilizes different cases of Proposition 3.5 and Corollary 3.9, namely the cases involving arithmetic sequences with common difference 2. □
We now have singularity confinement on X S for S an arithmetic sequence whose terms differ by 1 or 2. Generally, if S is a disjoint union of such sequences which are far apart from each other, then the corresponding singularities do not affect each other. Hence singularity confinement holds and the number of steps needed to get past the singularity is dictated by the length of the largest of the disjoint sequences.
Not all singularity types are of this form. For instance, consider S={3,4,7,8}. By Theorem 4.5, T 4 is defined generically on both X {3,4} and X {7,8}. One can check that T 4 is singular on X S , although another step does suffice to move past the singularity. For general types S, it is difficult to predict how many steps the corresponding singularities last. However, it would seem that singularity confinement does hold outside of some exceptional cases.
If n is odd, the only exceptional type is S=[1,n]1. Moreover, for any other S and generic A∈X S the corresponding singularity lasts at most n steps. We establish this by considering the worst case where |S|=n−1.
Proposition 4.6
Suppose n is odd and let S=[1,n]1∖{i} for some i∈[1,n]1. Then T n+1 is nonsingular at generic A∈X S .
Proof
Suppose without loss of generality that i=n. Then y 2=y 4=⋯=y 2n−2=−1. As always, we have y j+2n =y j for all j and y 1 y 2⋯y 2n =1. So Proposition 3.10 implies that, generically, F j,k ≠0 for j+k odd and k∈{n,n+1}. Therefore, T n+1 is generically defined by (6). □
Remark 4.7
In fact, Proposition 3.10 says more, namely that the relevant F-polynomials never vanish unless y 0=−1 or some y i =0. The assumption that quadruples of consecutive vertices be in general position forces all of the y i to be nonzero. As such, we find that the only singularities of T n+1 on X S occur when y 2n =y 0=−1. Hence, T n+1 restricts to a regular map on \(X_{S} \setminus X_{[1,n]_{1}}\).
Corollary 4.8
Suppose that n is odd and that S⊆̷[1,n]1. Then T n+1 is nonsingular for generic A∈X S .
Proof
Since S≠[1,n]1, there exists some S′ such that S⊆S′⊆̷[1,n]1 and |S′|=n−1. Since S⊆S′ we have X S ⊇X S′. Now T n+1 is nonsingular at generic A∈X S′ by Proposition 4.6. In particular, the map is defined at some such A, which is necessarily also in X S . It follows that T n+1 is defined generically on X S . □
Of course for general S, it will usually be the case that T m is defined on X S for some m<n+1. The corollary only ensures that n+1 steps will be sufficient. This appears to also be true for n even outside of some exceptional cases. We state this as a conjecture.
Conjecture 4.9
Suppose that n is even.
-
Singularity confinement holds generically on X S unless [1,n−1]2⊆S or [2,n]2⊆S.
-
Whenever singularity confinement holds for a type, there exists an m≤n such that generic singularities of that type last m steps (i.e. T m is singular but T m+1 is not).
Remark 4.10
The cases where singularity confinement fails to hold are quite extreme. If S=[1,n]1 then A∈X S has all its vertices lying on two lines. It follows that all the vertices of T(A) are equal. If n is even and say S contains [1,n−1]2 then half the vertices of A∈X S are collinear and T(A) will be contained in the common line. Amazingly, if n is even and A∈X S for S=[1,n]1 then a finite number of iterations of T −1 takes A to Y S [9, Theorem 3], [2, Theorem 7.9]. Similar results likely hold for the other exceptional singularity types.
5 Straightedge constructions: a first attempt
Let \(A \in\mathcal{P}_{n}\) be a singular point of T k for 1≤k<m but not of T m. The remainder of this paper focuses on the problem of constructing B=T m(A).
One possible approach would be to compute the x-coordinates of A, plug into (6) and (8) to find the x-coordinates of B, and then use these to construct B itself. This process would be computationally expensive as the number of terms of F j,k grows superexponentially with k. More to the point, this approach has the drawback that it ignores the geometry of the pentagram map.
As an alternative, we could choose a one-parameter family A(t) of twisted polygons varying continuously with t such that
-
1.
A(0)=A and
-
2.
A(t) is a regular point of T k for all t≠0 and k≤m.
For small t≠0, we can obtain B(t)=T m(A(t)) by iterating the geometric construction defining T. By continuity, B is given by lim t→0 B(t) which can be found numerically. This method is perhaps more feasible, but it involves a limiting procedure. More satisfying would be a finite construction, preferably one which can be carried out with a straightedge alone, as is the case with the pentagram map.
In this section we introduce an iterative approach to finding such a straightedge construction, which works in simple situations. The idea is to attempt to make sense of the polygon T k(A) for k<m despite the presence of the singularity. Let A(t) be as above, and fixing k<m, let C(t)=T k(A(t)). For each appropriate index i, let
We say that C i is well-defined if this limit always exists and is independent of the choice of the curve A(t) through A. We can define sides c j of T k(A) in the same way. In fact it is possible that each of the C i and c j are well-defined, despite the singularity. This would simply indicate that the resulting polygon C fails to satisfy the property that quadruples of consecutive vertices be in general position, which is needed for all the x-coordinates to be defined.
As before, suppose \(A \in\mathcal{P}_{n}\) is a singular point of T k for 1≤k<m but not of T m. In addition, assume that all of the vertices and sides of T k(A) for 1≤k<m are well-defined. Then it should be possible to construct the components of these intermediate polygons successively. Ideally, each individual side or vertex can be constructed by a simple procedure depending only on nearby objects.
The most basic of these local rules is the usual definition of the pentagram map, namely, if B=T(A) then
for each index i of A and
for each index j of B. These rules only work when A i−1≠A i+1 and \(b_{j-\frac {1}{2}} \neq b_{j+\frac{1}{2}}\), respectively. Other rules are needed to handle other cases. The next simplest rule involves triple ratios which are a six point analogue of cross ratios.
Definition 5.1
Let A,B,C,D,E,F be points in the plane with A,B,C collinear, C,D,E collinear, and E,F,A collinear. The triple ratio of these points is defined to be
where for instance, \(\frac{AB}{BC}\) refers to the ratio of these two lengths, taken to be positive if B lies between A and C and negative otherwise.
We will need to following properties of triple ratios, which can be found for instance in [8].
Proposition 5.2
-
Triple ratios are invariant under projective transformations.
-
(Ceva’s theorem) If the lines \(\overleftrightarrow{A D}\), \(\overleftrightarrow{C F}\), and \(\overleftrightarrow{E B}\) are concurrent then
$$ [A,B,C,D,E,F] = 1 $$ -
(Menelaus’ theorem) If B, D, and F, are collinear then
$$ [A,B,C,D,E,F] = -1 $$
Proposition 5.3
Suppose \(A \in\mathcal{P}_{n}\) is a regular point of T and T 2, and let B=T(A), C=T 2(A). Then for all i∈ℤ
Proof
That the triple ratio makes sense, and that it satisfies the condition of Menelaus’ theorem, are both clear from Fig. 5.
□
Now imagine continuously deforming the polygons until all six of these points are collinear. This relation holds as the polygons are being deformed, so it continues to hold in the limit. In particular, if five of these points are well-defined and collinear, then generically the sixth is also well-defined and is the unique point on the line for which the relation holds. Stated as a rule, if B=T(A), C=T(B), and if \(A_{i},B_{i-\frac{3}{2}},B_{i-\frac{1}{2}},B_{i+\frac {1}{2}},B_{i+\frac{3}{2}}\) are collinear for some index i of A then
Here, TripleConjugate is a function that inputs five collinear points P 1,P 2,P 3,P 4,P 5 and outputs the unique point P 6 on the common line such that [P 1,P 2,P 3,P 4,P 5,P 6]=−1.
The ordered sextuple of sides \(a_{j},b_{j-\frac{3}{2}},b_{j+\frac {1}{2}},b_{j-\frac{1}{2}},b_{j+\frac{3}{2}},c_{j}\) satisfy the same incidences as the vertices \(A_{i},B_{i-\frac{3}{2}},B_{i-\frac {1}{2}},B_{i+\frac{1}{2}},B_{i+\frac{3}{2}},C_{i}\) (see Fig. 6). So we get the analogous rule that if for some index j of B the sides \(a_{j},b_{j-\frac{3}{2}},b_{j+\frac{1}{2}},b_{j-\frac {1}{2}},b_{j+\frac{3}{2}}\) are all concurrent then
A configuration of lines dual to the configuration of points in Fig. 5
These rules are already enough to handle singularities of the simplest type. The full construction is described in the next subsection. The following subsection explains the difficulty in handling more complicated singularities.
5.1 The map T 3:X 3→Y 3
The case m=1 of Theorem 4.2 says that T 3 restricts to a rational map from X i to Y i . Assume without loss of generality that i=3. Throughout this subsection, assume A∈X 3 and let B=T(A), C=T 2(A), and D=T 3(A). Since A∈X 3 we see that A 1,A 3,A 5 are collinear, so let l denote the line containing them. In the following, i and j will denote elements of ℤ and \(\frac{1}{2} + \mathbb{Z}\), respectively.
We start by constructing B, which can be done via the usual pentagram map. So construct \(b_{i} = \overleftrightarrow{A_{i-1} A_{i+1}}\) for all i and \(B_{j} = b_{j-\frac{1}{2}} \cap b_{j+\frac{1}{2}}\) for all j. Note that b 2=b 4=l. Therefore, B 1.5,B 2.5,B 3.5,B 4.5 all lie on l and moreover
Let P be this common point. The construction of B is shown in Fig. 7.
Generically, B j−1≠B j+1 for all j, so the sides of C can all be constructed as \(c_{j} = \overleftrightarrow{B_{j-1} B_{j+1}}\). Note that c 2.5=c 3.5=l. Hence, we cannot use c 2.5∩c 3.5 to construct C 3. However, A 3,B 1.5,B 2.5,B 3,5,B 4.5 all lie on l so the rule (12) applies:
As usual, \(C_{i} = \overleftrightarrow{c_{i-\frac{1}{2}} c_{i+\frac {1}{2}}}\) for all i≠3. In particular we have

Figure 8 shows the construction of C from B.
The last difficulty is in constructing the side d 3 since C 2=C 4. However, b 3,c 1.5,c 2.5,c 3.5,c 4.5 all pass through P so by (13)
In particular, d 3 contains P. Letting d i =C i−1∩C i+1 for all i≠3, we see that d 1 contains C 2=P and d 5 contains C 4=P as well. This verifies that D∈Y 3. Finally, the vertices of D are constructed as \(D_{j} = d_{j-\frac{1}{2}} \cap d_{j+\frac{1}{2}}\) for all j. The construction of D from C is given in Fig. 9. The full construction of D from A is summarized in Algorithm 1.
Remark 5.4
All algorithms in this paper can be carried out as straightedge constructions. When this is not completely apparent from the algorithm itself, more details are provided in the surrounding text and/or in the Appendix. For example, Algorithm 1 uses the function TripleConjugate, a construction for which is given in Algorithm 5 of the Appendix. In addition to the usual operations of projective geometry (finding a line through two points or the intersection point of two lines) we assume as a primitive a function RandomPoint() which returns the next in an arbitrarily long sequence P 1,P 2,… of points in the plane. All algorithms are only claimed to behave correctly for generic choices of these points. For convenience, define
-
\(\texttt{RandomLine}() := \overleftrightarrow{\mbox{ \texttt {RandomPoint}()} \mbox{\texttt{RandomPoint}() }}\)
-
RandomPointOn(l):=RandomLine()∩l
-
\(\texttt{RandomLineThrough}(P) := \overleftrightarrow{\mbox { \texttt{RandomPoint}()} P}\)
5.2 The map T 4:X {3,5}→Y {3.5,4.5}
The next simplest case, m=2, of Theorem 4.2 concerns a singularity which disappears after four steps. Specifically, taking i=4 there is a map T 4:X {3,5}→Y {3.5,4.5}. Suppose A∈X {3,5} which means that A 1, A 3, A 5, and A 7 are collinear. Let l be their common line. Then E=T 4(A)∈Y {3.5,4.5}, i.e., e 1.5,e 3.5,e 5.5 are concurrent and e 2.5,e 4.5,e 6.5 are also concurrent. As before, we will attempt to successively construct the intermediate polygons, namely B=T(A), C=T 2(A), and D=T 3(A). However, in this case not all of these polygons will be completely well-defined. Again, let i and j range over ℤ and \(\frac{1}{2} + \mathbb{Z}\), respectively. The constructions that follow are illustrated in Figs. 10, 11, 12, and 13.
As before, B can be constructed using the standard pentagram map. In this case, it will have three sides equal to l, namely b 2, b 4, and b 6. As a result, the six consecutive vertices B 1.5,B 2.5,…,B 6.5 will all lie on l. Moreover, we have

The sides \(c_{j} = \overleftrightarrow{B_{j-1} B_{j+1}}\) of C are all defined, although c 2.5,c 3.5,c 4.5,c 5.5 all equal l. So the first problems arise in constructing the vertices C 3, C 4, and C 5. In general, C 3 only depends on vertices A 0 through A 6 of the original polygon, so the assumption A 7∈l is irrelevant for its construction. This puts us in the context of the previous subsection, so as there we have
By symmetry there is a similar construction of C 5:
The situation with C 4 is more complicated. Ordinarily, we would use the fact
and solve for C 4. However, B 2.5=B 3.5 and B 5.5=B 4.5 so the triple ratio comes out to 0/0. As such, we cannot use this method to construct C 4. In fact, it turns out that C 4 is simply not well-defined.
The fact that an intermediate vertex is not well-defined causes great difficulty in the current approach to devising straightedge constructions. In the following sections, we demonstrate how enriching the input A with first-order data counteracts this difficulty and leads to a general algorithm. Before moving on, we finish describing a construction particular to the present context which works around the matter of C 4.
Recall that sides c 2.5 through c 5.5 of C all equal l, so its vertices C 2 through C 6 all lie on this line. As such, we know \(d_{3} = \overleftrightarrow{C_{2} C_{4}}=l\) and \(d_{5} = \overleftrightarrow {C_{4} C_{6}} = l\) even though C 4 is itself not well-defined. The rest of the sides of D are constructed similarly, and of note d 4 also equals l. The other sides are all generic so we can construct \(D_{j} = d_{j-\frac{1}{2}} \cap d_{j+\frac{1}{2}}\) for all j other than 3.5 and 4.5. For these two vertices, we work backwards. We know ultimately that e 1.5,e 3.5,e 5.5 will be concurrent. But e 1.5∩e 3.5=D 2.5 and e 3.5∩e 5.5=D 4.5 so D 4.5=D 2.5. Similarly, the fact that e 2.5,e 4.5,e 6.5 are concurrent implies that D 3.5=D 5.5.
For the final step, let \(e_{j} = \overleftrightarrow{D_{j-1} D_{j+1}}\) for all j besides 3.5 and 4.5. The usual construction fails for e 3.5 because D 2.5=D 4.5 and the construction involving triple conjugates also fails because d 3=d 4=d 5. However, e 3.5 certainly is well-defined as it is a side of \(E = T^{4}(A) \in\mathcal {P}_{n}\). Through trial and error we discovered the following construction for e 3.5, and by symmetry, one for e 4.5.
Proposition 5.5
Under the assumptions of this subsection

Remark 5.6
In principle, results like Proposition 5.5 can be proven computationally. In instances for which we are unaware of a more illuminating proof, we will simply fall back on this sort of reasoning. The computations required are generally quite tedious, so we will tend to omit them.
6 Decorated polygons
Let A be a twisted polygon which is a singular point of T k. As explained in the previous section, we can attempt to define T k(A) as a limit of T k(A(t)) where A(t) is a curve in the space of polygons passing through A=A(0). As we saw in Sect. 5.2, the result sometimes depends on the choice of the curve. This suggests a different approach to constructing the first nonsingular iterate T m(A). Start by fixing arbitrarily the one-parameter family A(t). With respect to this choice the intermediate polygons T k(A) are well-defined. Constructing them in turn we eventually get T m(A). Since A is not a singular point of T m, the final result will not depend on the choice of A(t).
Working with actual curves would be difficult. However, all that will actually matter will be the first-order behavior of the curve near t=0. This information can be encoded using geometric data which we call decorations.
Let A be a point in the projective plane, and let γ be a smooth curve with γ(0)=A. Define the associated decoration of A, denoted A ∗, to be the tangent line of γ at A:
When defined, A ∗ is a line passing through A.
By the same token, if a is a line in the projective plane then a can be thought of as a point in the dual plane. Given a curve γ through that point we can define the decoration a ∗ as
When defined, a ∗ is a point lying on a.
Finally, let A be a twisted polygon and γ a curve in the space of twisted polygons with γ(0)=A. Then γ determines a curve in the plane through each vertex of A and a curve in the dual plane through each side of A. By the above, we can define decorations on each of these individual objects.
Definition 6.1
A decorated polygon is a twisted polygon A together with the decorations of each of its vertices and sides induced by some curve γ in the space of twisted polygons with γ(0)=A.
Decorated polygons will be denoted by the appropriate script letter. For instance if the underlying polygon is A then the decorated polygon will be called \(\mathcal{A}\). It is possible for different curves to give rise to the same decorated polygon \(\mathcal{A}\). As such, \(\mathcal{A}\) corresponds to a whole class of curves. We will call any curve γ in this class a representative of \(\mathcal{A}\).
Remark 6.2
Definition 6.1 refers to the space of twisted polygons. This should not be confused with \(\mathcal{P}_{n}\) or \(\mathcal{P}_{n}^{*}\) which are spaces of projective equivalence classes of twisted polygons. In general, we will be working with actual polygons instead of equivalence classes of polygons for the remainder of the paper.
Given a collection of geometric objects which satisfy certain incidences (e.g. the vertices and sides of a polygon), a consistent choice of decorations of these objects may have to satisfy some relations. The simplest example of such a relation occurs for a closed triangle.
Proposition 6.3
In △ABC let \(a = \overleftrightarrow{B C}\), \(b = \overleftrightarrow{A C}\), and \(c = \overleftrightarrow{A B}\) (see Fig. 14). Let A(t), B(t), and C(t) be curves through the vertices and use them to define curves corresponding to the sides (e.g. \(a(t) = \overleftrightarrow{B(t) C(t)}\)). Then the corresponding decorations satisfy
Lemma 6.4
Let △A′B′C′ be another triangle with \(a' = \overleftrightarrow{B' C'}\), \(b' = \overleftrightarrow{A' C'}\), and \(c' = \overleftrightarrow{A' B'}\) (see Fig. 15). Then
Proof
Both sides of (15) depend in a projectively natural way on the six points A,B,C,A′,B′,C′. We can hence use a projective transformation to normalize four of these points as we see fit. We can then compute both sides in terms of the coordinates of the remaining two points. We omit the details as per Remark 5.6. □
Proof of Proposition 6.3
In Lemma 6.4, take A′=A(t), B′=B(t), and C′=C(t) and consider the limit as t goes to 0. In the limit, the vertices and sides of △A′B′C′ approach their counterparts in △ABC. By definition, \(\overleftrightarrow{A A'}\) approaches A ∗ and similarly for the other vertices and sides. So the limit of (15) is precisely (14). □
Remark 6.5
For each n, there is a relation similar to (14) among the decorations of a closed n-gon. Moreover, this is the only relation that holds. Hence, one can pick n vertex decorations and n−1 sides decorations (or the other way around) independently, and the last decoration is then determined. The space of decorations of a fixed polygon A, then, has dimension 2n−1. One can check that this space naturally corresponds to the projectivized tangent space of A within the space of closed n-gons. A similar statement is probably true for twisted polygons, but we do not understand what the relations are among the individual decorations.
The next proposition shows that repeated applications of (14) can be used to extend the pentagram map to decorated polygons.
Proposition 6.6
Let A(t) be a curve in the space of polygons and let B(t)=T(A(t)) for all t. Let \(\mathcal{A}\) and \(\mathcal{B}\) be the corresponding decorations of A=A(0) and B=B(0), respectively. Then \(\mathcal{B}\) is uniquely determined by \(\mathcal{A}\).
Proof
Given an index i of A, consider the triangle with vertices A i−1, A i , and A i+1 (see Fig. 16). It has all three vertices and two of its sides coming from A. The last side is \(\overleftrightarrow{A_{i-1} A_{i+1}}=b_{i}\). Applying Proposition 6.3 to this triangle, then, expresses \(b_{i}^{*}\) in terms of \(\mathcal{A}\).
Next, consider the triangle with vertices \(A_{j-\frac{1}{2}}\), B j and \(A_{j+\frac{1}{2}}\) for some index j of B (see Fig. 17). Two of its vertices and one of its sides belong to A. The other two sides are in fact sides of B, namely

These were both decorated in the previous step. Another application of Proposition 6.3, then, determines \(B_{j}^{*}\).
□
The procedure above to construct \(\mathcal{B}\) from \(\mathcal{A}\) should be thought of as a lift of the pentagram map to the space of decorated polygons. To distinguish this operation from the original map, write \(\mathcal{B} = \tilde{T}(\mathcal{A})\). The construction defining \(\tilde{T}\) is given in Algorithm 2.
The subroutines DecorateSide and DecorateVertex build the triangles in Figs. 16 and 17 respectively, and use (14) to compute the desired decoration.
Remark 6.7
We will only be using decorated polygons and the map \(\tilde{T}\) as tools in our straightedge constructions. However, these are likely interesting objects to study in their own right. Some problems immediately come to mind, including the following:
-
Find a good set of coordinates on the space of decorated polygons.
-
Compute the map \(\tilde{T}\) in these coordinates.
-
Determine if \(\tilde{T}\) defines a discrete integrable system.
7 Degenerations
We saw in the previous section that (14) is the only identity needed to apply the pentagram map to a generic decorated polygon. However, the motivation for introducing decorations is to handle degenerate cases. In this section, we introduce methods which will eventually be used to apply the pentagram map to a large class of degenerate polygons. Everything will be expressed in terms of local rules involving triangles and complete quadrilaterals.
7.1 Triangles
Let A(t), B(t), C(t) be curves in the plane passing through points A, B, and C at time t=0. Assume that for all t≠0, the points A(t), B(t), and C(t) are in general position, and let a(t), b(t), and c(t) denote the sides of the triangle they form. We allow A, B, and C to be collinear, or even equal to each other. However, assume that the limits

all exist. Assume that the limits defining the decorations A ∗,B ∗,C ∗,a ∗,b ∗,c ∗ all exist as well.
Now, Proposition 6.3 did not allow for A, B and C to be collinear. However, by continuity (14) still holds in the present context.
Proposition 7.1
Assume that the decorations of the triangle are generic (i.e. distinct from each other and from the vertices and sides of the triangle). Then the vertex B is uniquely determined by the sides a,b,c, the vertices A,C, and all the corresponding decorations.
Proof
If a≠c, then B=a∩c, so assume a=c. There are two cases depending on if b equals the other sides.
If b≠a=c then A=b∩c=b∩a=C. In general, if P 1=P 5 then

so (14) simplifies to
Note that the dependence on B ∗ has disappeared, so this identity determines B from the given geometric data.
Alternately, suppose b=a=c. Whenever P 1=P 3=P 5 we have

Consequently, (14) becomes
so again we can construct B. □
To sum up, if a=c in a triangle then (14) can be used to construct the vertex B. The downside is that this identity can no longer be used to determine the decoration B ∗. In fact, B ∗ is independent from the rest of the triangle when a=c. As such, we will need more data to construct vertex decorations when degeneracies occur.
7.2 Complete quadrilaterals
A complete quadrilateral is a projective configuration consisting of four lines (called sides) in general position together with the six points (called vertices) at which they intersect. Call the sides l 1,l 2,l 3,l 4 and call the vertices A,B,C,D,E,F as in Fig. 18.
As with triangles, we define degenerate complete quadrilaterals to be configurations that can be obtained as a limit of ordinary complete quadrilaterals. More precisely, let l 1(t),…,l 4(t) and A(t),…,F(t) be smooth curves which define a complete quadrilateral at each time t≠0. Let l 1=l 1(0),l 2=l 2(0),…,F=F(0). Then some or all of the sides l i could be equal. Assume that the decorations \(l_{1}^{*}, l_{2}^{*}, \ldots, F^{*}\) are all defined.
Proposition 7.2
Consider a degenerate complete quadrilateral with l 1=l 2=l 3=l 4. Then the vertex decoration F ∗ is uniquely determined by the other vertices, sides, and decorations.
Proof
By Menelaus’ theorem, [A,B,C,D,E,F]=−1. According to the Appendix, F can be constructed from the other vertices using a construction as in Fig. 23. The idea of the present construction is to build a configuration as in that figure at each time t.
Choose generically in the plane a point c ∗ and lines P ∗ and (C′)∗ (the reason for these names will become clear shortly). For each t, define

Note that
which justifies the notation c ∗. Similar remarks hold for P ∗ and C′∗. Defining

we get at time t=0 a configuration as in Fig. 23. In particular B′, D′, and F are collinear. The proof of this fact given in the Appendix generalizes to show that B′(t), D′(t), and F(t) are collinear for all t. Let \(l_{3}'(t)\) denote the common line. By way of notation, let \(l_{1}'(t) = \overleftrightarrow{A(t) C'(t)}\), \(l_{4}'(t) = \overleftrightarrow{E(t) C'(t)}\), \(b(t) = \overleftrightarrow{B(t) P(t)}\), and \(d(t) = \overleftrightarrow{D(t) P(t)}\).
We are given decorations of A,B,…,E and l 1,l 2,l 3,l 4 from the outset. We chose arbitrarily decorations of P, C′, and c. In a generic triangle, knowing five of the six decorations determines the sixth by Proposition 6.3. This fact can be used to find all missing decorations in our configuration. To start, use the first triangle in Fig. 19 to find \((l_{1}')^{*}\) and the second triangle to find b ∗. Once these decorations are found, the third triangle in the figure can be used to determine (B′)∗. A similar method is used to find \((l_{4}')^{*}\), d ∗, and then (D′)∗. Finally, use the first triangle in Fig. 20 to find \((l_{3}')^{*}\) and the other triangle to find F ∗.
□
7.3 Degenerate polygons
A degenerate polygon is a sequences of points and an interlacing sequence of lines, which occur as the limits of the vertices and sides, respectively, of some twisted polygons. More precisely, if A(t) is a twisted polygon for t≠0 and the appropriate limits are defined, then we get a degenerate polygon A with vertices A i =lim t→0 A i (t) and sides a j =lim t→0 a j (t). Fixing such a curve A(t), we get a decoration for A as before.
Using our understanding of degenerate triangles and complete quadrilaterals, we are ready to state a version of \(\tilde{T}\) which works for degenerate polygons. As will be explained, the algorithm requires two consecutive iterates of the pentagram map, \(\mathcal{A}\) and \(\mathcal{B}\), as input. The output is the iterate \(\mathcal{C}\) which follows these two. The new procedure is called \(\tilde{T}_{2}\) and is given in Algorithm 3. In the algorithm, j ranges over the index set of B and i ranges over the index set of C. A description of the subroutines appearing in the algorithm will follow.
The outline of this algorithm is the same as that of the original version of \(\tilde{T}\). First the sides of \(\mathcal{C}\) are constructed, then the side decorations, then the vertices, and finally the vertex decorations. Each individual step, though, is made more complicated by the possibility of degeneracies.
The subroutine ConstructVertex2 works with the triangle pictured in Fig. 21. All of the components of the triangle besides C i have already been constructed. Hence by Proposition 7.1, it is always possible to construct C i .
The subroutine DecorateVertex2 begins from this same triangle. If \(c_{i-\frac{1}{2}} \neq c_{i+\frac{1}{2}}\) then (14) is used to compute \(C_{i}^{*}\). Otherwise, more data are needed. Consider the complete quadrilateral in Fig. 5. We are assuming that two of its sides, namely \(c_{i-\frac{1}{2}}\) and \(c_{i+\frac{1}{2}}\), are equal. This forces the five vertices other than A i to lie on the common line. Generically, these five vertices are distinct forcing the two remaining sides (namely b i−1 and b i+1) of the complete quadrilateral to be equal to each other and to \(c_{i-\frac{1}{2}}=c_{i+\frac{1}{2}}\). This puts us in the situation of Proposition 7.2. All vertices besides C i and all sides have been decorated already, so the procedure can determine the decoration on C i .
We used above the fact that if two sides of a complete quadrilateral are equal, then generically, they all must be equal. However, non-generic example where this fails will arise in practice. For instance, in Figs. 10 and 11 we have c 3.5=c 4.5 but b 3 and b 5 are different. In these situations, DecorateVertex2 will simply return a random decoration, i.e., a random line passing through C i .
The subroutines ConstructSide2 and DecorateSide2 behave like ConstructVertex2 and DecorateVertex2 respectively. The difference is that they operate with configurations which are projectively dual to the ones in Figs. 21 and 5. First, Fig. 22 shows the triangle used by ConstructSide2. This procedure constructs c j in the dual manner to how ConstructVertex2 finds C i in Fig. 21.
Similarly, Fig. 6 contains a configuration that is projectively dual to the complete quadrilateral in Fig. 5. As such, DecorateSide2 can find \(c_{j}^{*}\) via the projective dual of the construction used by DecorateVertex2.
The case where DecorateVertex2 outputs a random line, and the analogous case of DecorateSide2, are not currently justified. However, all other cases are covered by Propositions 7.1 and 7.2. Hence we have the following correctness property of Algorithm 3.
Proposition 7.3
Let A(t) be a curve in the space of twisted polygons that is generic away from t=0. Let B(t)=T(A(t)) and C(t)=T(B(t)) for t≠0. Let \(\mathcal{A}\), \(\mathcal{B}\), and \(\mathcal{C}\) be the decorated polygons associated to these curves. Suppose that


where j and i run over the vertex indices of B and C, respectively. Then \(\mathcal{C} = \tilde{T}_{2}(\mathcal{A},\mathcal{B})\).
More specifically, if (17) fails for some j, then DecorateSide2 chooses a random decoration for c j . If (18) fails for some i, then DecorateVertex2 chooses a random decoration for C i . Otherwise, the algorithm \(\tilde {T}_{2}\) behaves deterministically and correctly.
8 The main algorithm
The goal of our main algorithm is to construct B=T m(A) from A when the usual construction fails, i.e. when A is a singular point of various T k for k<m. According to the previous section, it is typically possible to construct and decorate T 2(A) given A, T(A), and the corresponding decorations, even when singularities arise. The main construction, given in Algorithm 4, simply iterates this procedure.
Given S⊆{1,2,…,n} such that singularity confinement holds on X S , let m be the smallest positive integer such that T m is generically defined on X S . We want to say for generic A∈X S that the main algorithm, given A and m as input, produces T m(A). For the simplest singularity types, S={i}, this result follows from Propositions 6.6 and 7.3.
For more complicated S, a difficulty arises because the assumptions (17) and (18) in Proposition 7.3 will not hold at every step. Hence, some applications of \(\tilde{T}_{2}\) in the main algorithm will produce random decorations. To prove correctness of the algorithm for such S, it is necessary to determine at which steps this occurs and to demonstrate that the outcome is independent of the random choices.
We will focus our attention on the types covered by Theorem 4.2. Taking i=0 for convenience in the Theorem, let S=[−(m−1),(m−1)]2. Suppose A∈X S is generic. Tracing through the beginning of the main algorithm, let \(\mathcal{A}\) be some decoration of A, let \(\mathcal{B} = \tilde{T}(\mathcal{A})\), and let \(\mathcal{C} = \tilde{T}_{2}(\mathcal{A},\mathcal{B})\).
Since A∈X S , the A i for i∈[−m−1,m+1]2 all lie on a common line, say l. It follows (see e.g. Figs. 7, 8, 10, and 11) that b i =l for i∈[−m,m]2 and c j =l for j∈[−m+1/2,m−1/2]1. Consequently, condition (18) holds for i∈[−m+1,m−1]2 but fails for i∈[−m+2,m−2]2 (assuming m≥2). As such the corresponding C i are decorated randomly.
To establish that main(A, m+2) = T m+2(A) for A as above, we need to prove two facts. The first is that the output of the algorithm does not depend on the decorations of the C i that are chosen randomly. For given m, we can check this computationally by showing that any such choice of decorations is possible for an appropriate choice of representative A(t) of \(\mathcal{A}\). The second fact is that no other violations of (17) or (18) occur until computing Iterates[m+2] in the last step. For given m, it suffices to check that this fact is true for a single \(\mathcal{A}\) as it then follows for generic examples.
We have no general proof for the necessary facts, but we have verified that they hold for the first several values of m. Assuming them, we can repeatedly apply Proposition 7.3 to conclude that Iterates[k] is the decoration corresponding to the curve T k(A(t)) for some curve A(t) through A and all k<m+2. At the last step condition (17) will fail in some places, so Iterates[k+2] will have some randomly decorated sides. However, the sides of Iterates[k+2] themselves will be correct proving that its underlying polygon is in fact T m+2(A). Hence we see that the main algorithm works correctly for polygons of type [−m+1,m−1]2 when m is small. We expect that this result holds for all m.
Remark 8.1
The main algorithm is stated without regard to a particular singularity type. Hence it has the potential to work in greater generality than is discussed above. Experiments indicate that the algorithm does work for many, but not all, other singularity types. The simplest types for which it fails are S={3,4,6} and similar.
References
Elkies, N., Kuperberg, G., Larsen, M., Propp, J.: Alternating-sign matrices and domino tilings. J. Algebr. Comb. 1, 111–132 (1992)
Glick, M.: The pentagram map and Y-patterns. Adv. Math. 227, 1019–1045 (2011)
Grammaticos, B., Ramani, A., Papageorgiou, V.: Do integrable mappings have the Painlevé property? Phys. Rev. Lett. 67, 1825–1828 (1991)
Gekhtman, M., Shapiro, M., Tabachnikov, S., Vainshtein, A.: Higher pentagram maps, weighted directed networks, and cluster dynamics. Electron. Res. Announc. Math. Sci. 19, 1–17 (2012)
Ovsienko, V., Schwartz, R., Tabachnikov, S.: The pentagram map: a discrete integrable system. Commun. Math. Phys. 299, 409–446 (2010)
Ovsienko, V., Schwartz, R., Tabachnikov, S.: Liouville-Arnold integrability of the pentagram map on closed polygons. arXiv:1107.3633
Fomin, S., Zelevinsky, A.: Cluster algebras IV: Coefficients. Compos. Math. 143, 112–164 (2007)
Richter-Gibert, J.: Perspectives on Projective Geometry: A Guided Tour Through Real and Complex Geometry. Springer, Heidelberg (2011)
Schwartz, R.: Discrete monodromy, pentagrams, and the method of condensation. J. Fixed Point Theory Appl. 3, 379–409 (2008)
Schwartz, R.: The pentagram map. Exp. Math. 1, 71–81 (1992)
Soloviev, F.: Integrability of the pentagram map. arXiv:1106.3950
Acknowledgements
I thank Pavlo Pylyavskyy, Sergei Tabachnikov, and particularly Sergey Fomin for many valuable discussions during the course of this project. I am grateful to Richard Schwartz who introduced me to this problem and explained to me his previous work in the area.
Author information
Authors and Affiliations
Corresponding author
Additional information
Partially supported by NSF grants DMS-0943832 and DMS-1101152.
Appendix: Some basic constructions
Appendix: Some basic constructions
This appendix states and proves straightedge constructions for the primitives used in the algorithms throughout the paper. The first, namely TripleConjugate, is given in Algorithm 5. This construction was shown to me by Pavlo Pylyavskyy.
This algorithm constructs points B′, C′, D′ and F such that (A,B′,C′,D′,E,F) is a Menelaus configuration (see Fig. 23). Therefore [A,B′,C′,D′,E,F]=−1. Applying a projective transformation we may assume that P is a point at infinity. The lines \(\overleftrightarrow{B B'}\), \(\overleftrightarrow{C C'}\), and \(\overleftrightarrow{D D'}\) all pass through this point, so they must be parallel. Therefore △ABB′ is similar to △ACC′, so \(\frac{AB}{BC} = \frac{AB'}{B'C'}\). Also, △EDD′ is similar to △ECC′, so \(\frac{CD}{DE} = \frac{C'D'}{D'E}\). It follows that
as desired.
Next, Algorithm 6 inputs four points A, B, C, D, on one line, and three points A′, B′, C′ on another. There exists a unique projective transformation from the first line to the second taking A to A′, B to B′, and C to C′. The algorithm returns the result of applying this projective transformation to D.
The algorithm selects a line l and a point P such that projection through P onto l sends A to A′. The images of B, C, are called B″ and C″, respectively. Then Q is constructed so that projection through Q onto the target line sends B″ to B′ and C″ to C′, while necessarily fixing A′ (see Fig. 24). Hence, the composition of these two projections is the desired projective transformation. Applying it to D gives the output D′.
Cross ratios are invariant under projective transformation. Hence [A′,B′,C′,D′]=[A,B,C,D] and D′ is the unique point on the line containing A′,B′,C′ with this property. As such, we use this construction to find a point B satisfying (16). This appears to be a more complicated situation because one of the cross ratios is inverted, and also because both points and lines are involved. The identity can be expressed in terms of points alone using the fact that [l 1,l 2,l 3,l 4]=[l 1∩l,l 2∩l,l 3∩l,l 4∩l] for any other line l. The reciprocal can be eliminated by reordering via the property [P 1,P 2,P 3,P 4]−1=[P 1,P 4,P 3,P 2].
Another component of several of our algorithms involves finding one point or line from (14) in terms of the others. By similar remarks to before, it is possible to cast this as a problem involving points alone, namely to construct F′ from the other points assuming
Here, not all points are assumed to be collinear, only those triples required by the definition of triple ratios.
Lemma 9.1
[A,B,C,D,E,F]=[A,P,E,F] where
(see Fig. 25).
Proof
For any point P on A∩E, we have
For the particular P chosen, Ceva’s theorem guarantees that [A,B,C,D,E,P]=1. □
In light of this lemma, it is easy to construct the point F′ above. The details are given in Algorithm 7.
Rights and permissions
About this article
Cite this article
Glick, M. On singularity confinement for the pentagram map. J Algebr Comb 38, 597–635 (2013). https://doi.org/10.1007/s10801-012-0417-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10801-012-0417-6