Abstract
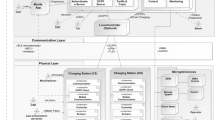
This work performs a security analysis of the vehicle-to-grid charging protocol ISO 15118 and presents various scenarios of how to compromise the availability of the charging service or the integrity, authenticity, or confidentiality of the communication on a protocol level. Furthermore, it analyzes processes related to the authentication, transfer of information, and the certification hierarchy for vulnerabilities, which could be used by an adversary to gain unfair advantage over the charging process and use it for his own self-interest, mostly harming legitimate users or other participants.


Similar content being viewed by others
References
ISO 15118-1:2013. Road vehicles—vehicle to grid communication interface—Part 1: general information and use-case definition. International Organization for Standardization
ISO 15118-2:2014. Road vehicles—vehicle-to-grid communication interface—Part 2: network and application protocol requirements. International Organization for Standardization
ISO 15118-3:2015. Road vehicles—vehicle to grid communication interface—Part 3: physical and data link layer requirements. International Organization for Standardization
BSI TR-03109-1 (2013) Anforderungen an die Interoperabilität der Kommunikationseinheit eines intelligenten Messsystems. Federal Office for Information Securtity (BSI)
Bräuchle T (2017) Datenschutzprinzipien in IKT-basierten kritischen Infrastrukturen
Bretthauer S (2017) Smart Meter im Spannungsfeld zwischen Europäischer Datenschutzgrundverordnung und Messstellenbetriebsgesetz. Zeitschrift für das gesamte Recht der Energiewirtschaft, pp 56–61
Damon E, Dale J, Laron E, Mache J, Land N, Weiss R (2012) Hands-on denial of service lab exercises using slowloris and rudy. In: Proceedings of the 2012 information security curriculum development conference, InfoSecCD ’12, pp 21–29. ACM, New York, NY, USA. doi:10.1145/2390317.2390321
Deutscher Bundestag: Drucksache 18/7555, Entwurf eines Gesetzes zur Digitalisierung der Energiewende (17.02.2016). http://dip21.bundestag.de/dip21/btd/18/075/1807555.pdf
Deutscher Bundestag: Drucksache 18/8919, Beschlussempfehlung und Bericht zum Entwurf eines Gesetzes zur Digitalisierung der Energiewende (22.06.2016). http://dip21.bundestag.de/dip21/btd/18/089/1808919.pdf
Dolev D, Yao A (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208
Falk R, Fries S (2012) Electric vehicle charging infrastructure security considerations and approaches. In: Proceedings of INTERNET, pp 58–64
Falk R, Fries S (2013) Securely connecting electric vehicles to the smart grid. Int J Adv Internet Technol 6(1 & 2): 57–67
Garcia FD, de Koning Gans G, Muijrers R, van Rossum P, Verdult R, Schreur RW, Jacobs B (2008) Dismantling MIFARE classic. Springer, Berlin, pp 97–114. doi:10.1007/978-3-540-88313-5_7
Höfer C, Petit J, Schmidt R, Kargl F (2013) Popcorn: privacy-preserving charging for emobility. In: Proceedings of the 2013 ACM workshop on security, privacy & dependability for cyber vehicles, pp 37–48. ACM
Kühling J, Martini M (2016) Die Datenschutz-Grundverordnung: Revolution oder Evolution im europäischen und deutschen Datenschutzrecht? Europäische Zeitschrift für Wirtschaftsrecht, pp 448–454
Lee S, Park Y, Lim H, Shon T (2014) Study on analysis of security vulnerabilities and countermeasures in ISO/IEC 15118 based electric vehicle charging technology. In: 2014 International conference on IT convergence and security (ICITCS), pp 1–4. IEEE
Mültin M (2014) Das Elektrofahrzeug als flexibler Verbraucher und Energiespeicher im Smart Home. Ph.D. Thesis. http://digbib.ubka.uni-karlsruhe.de/volltexte/1000042102. Karlsruhe, KIT, Diss
Nohl K, Evans D, Starbug S, Plötz H (2008) Reverse-engineering a cryptographic RFID tag. In: USENIX security symposium, vol 28
Verdult R, Garcia FD, Balasch J (2012) Gone in 360 seconds: Hijacking with Hitag2
Author information
Authors and Affiliations
Corresponding author
Additional information
This work is partially supported by the project Inductive and InteroperabLe charging Systems for Electric vehicles (IILSE) (No. 01MX15004), part of the funding program ELEKTRO POWER II: Electric Mobility Positioning Along the Value Chain by the German Federal Ministry for Economic Affairs and Energy (BMWi) and by the project Security for interconnected infrastructures (No. 16KIS0521) within the KASTEL competence center of the German Federal Ministry of Education and Research (BMBF).
Rights and permissions
About this article
Cite this article
Bao, K., Valev, H., Wagner, M. et al. A threat analysis of the vehicle-to-grid charging protocol ISO 15118. Comput Sci Res Dev 33, 3–12 (2018). https://doi.org/10.1007/s00450-017-0342-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00450-017-0342-y