Abstract
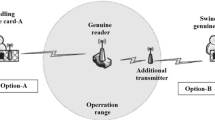
Distance bounding protocols are proposed based upon the round trip time measurements of the executed messages to prevent sensor networks against wormhole attack and to safeguard RFID systems against relay attack. In such protocols, the verifier authenticates users as well as establishing an upper bound on its physical distance between the users and itself. These protocols are also vulnerable to mafia fraud, distance fraud and terrorist fraud attacks. This paper deploys all-or-nothing method to propose a new distance bounding protocol with higher security level that can prevent terrorist fraud attack performed over the existing distance bounding protocols. Actually, the proposed protocol is the first protocol which can overcome all the three fraud attacks simultaneously with the lowest success probability of the attacks compared with the well known distance bounding protocols. Besides, the proposed protocol can be implemented on a low-cost device due to low computational cost and minimum system memory requirements.






Similar content being viewed by others
References
Abu-Mahfouz, A., & Hancke, G. P. (2013). Distance bounding: A practical security solution for real-time location systems. IEEE Transactions on Industrial Informatics, 9(1), 16–27.
Avoine, G., Bingöl, M. A., Kardaş, S., Lauradoux, C., & Martin, B. (2011). A framework for analyzing RFID distance bounding protocols. Journal of Computer Security, Special Issue on RFID Security (RFIDSec 2010), 19(2), 289–317.
Avoine, G., & Kim, C. H. (2013). Mutual distance bounding protocols. IEEE Transactions on Mobile Computing, 12(5), 830–839.
Avoine, G., Lauradoux, C., & Martin, B. (2011). How secret-sharing can defeat terrorist fraud. In Proceedings of the 4th conference on wireless network security (pp. 145–156). New York: ACM.
Avoine, G., & Tchamkerten, A. (2009). An efficient distance bounding RFID authentication protocol: balancing false-acceptance rate and memory requirement. In P. Samarati, M. Yung, F. Martinelli, & C. A. Ardagna (Eds.), LNCS (Vol. 5735) , Information security (ISC 2009) (pp. 250–261) Heidelberg: Springer.
Buccafurri, F., & Lax, G. (2011). Implementing disposable credit card numbers by mobile phones. Electronic Commerce Research, 11(3), 271–296.
Čapkun, S., & Hubaux, J. P. (2006). Secure positioning in wireless networks. IEEE Journal on Selected Areas in Communications, 24(2), 221–232.
Chen, I. C., & Hu, S. C. (2012). Gender differences in shoppers’ behavioural reactions to ultra-low price tags at online merchants. Electronic Commerce Research, 12(4), 485–504.
Chiang, J. T., Haas, J. J., & Hu, Y. C. (2009). Secure and precise location verification using distance bounding and simultaneous multilateration. In: Proceedings of the 2nd conference on wireless network security (pp. 181–192). New York: ACM.
Chien, H. Y., Yang, C. S., & Hou, H. P. (2012). Non-linearity cannot help RFID resist full-disclosure attacks and terrorist fraud attacks. Security and Communication Networks, doi:10.1002/sec.410. John Wiley
Falahati, A., & Jannati, H. (2012). Application of distance bounding protocols with random challenges over RFID noisy communication systems. In Proceedings of IET conference on wireless sensor systems (WSS 2012), London, UK (pp. 1–5).
Francillon, A., Danev, B., & Čapkun, S. (2011). Relay attacks on passive keyless entry and start systems in modern cars. In: Proceedings of the 18th annual network and distributed system security symposium, San Diego, California, USA.
Gürel, A. Ö., Arslan, A., & Akgün, M. (2011). Non-uniform stepping approach to RFID distance bounding problem. In J. Garcia-Alfaro, G. Navarro-Arribas, A. Cavalli, & J. Leneutre (Eds.), LNCS (Vol. 6514 ), Data privacy management and autonomous spontaneous security (DPM 2011) (pp. 64–78) US: Springer.
Hancke, G. P., & Kuhn, M. (2005). An RFID distance bounding protocol. In Proceedings of the 1st International conference on security and privacy for emergent areas in communications networks (SecureComm 2005) (pp. 67–73). Athens, Greece.
Hu, Y. C., Perrig, A., & Johnson, D. B. (2006). Wormhole attacks in wireless networks. IEEE Journal on Selected Areas in Communications, 24(2), 370–380.
Isaac, J. T., Zeadally, S., & Cámara, J. S. (2012). A lightweight secure mobile payment protocol for vehicular ad-hoc networks (VANETs). Electronic Commerce Research, 12(1), 97–123.
Isaac, J. T., Zeadally, S., & Sierra, J. C. (2010). Implementation and performance evaluation of a payment protocol for vehicular ad hoc networks. Electronic Commerce Research, 10(2), 209–233.
Issovits, W., & Hutter, M. (2011). Weaknesses of the ISO/IEC 14443 protocol regarding relay attacks. In Proceedings of the international conference on RFID technologies and applications (RFID-TA 2011) (pp. 335–342). Sitges, Spain.
Jain, S., & Baras, J. S. (2012). Preventing wormhole attacks using physical layer authentication. In Proceedings of the wireless communications and networking conference (WCNC 2012) (pp. 2712–2717). Paris, France.
Jannati, H., & Falahati, A. (2012). Mutual implementation of predefined and random challenges over RFID distance bounding protocol. In Proceedings of the 9th international conference on information security and cryptology (ISCISC 2012) (pp. 43–47). Tabriz, Iran.
Kardas, S., Kiraz, M. S., Bingöl, M. A., & Demirci, H. (2012). A novel RFID distance bounding protocol based on physically unclonable functions. In: A. Jules & C. Paar (Eds.), LNCS (Vol. 7055), RFID security and privacy (RFIDsec 2012) ( pp. 78–93). Heiledberg: Springer.
Kim, C. H., & Avoine, G. (2011). RFID distance bounding protocols with mixed challenges. IEEE Transactions on Wireless Communications, 10(5), 1618–1626.
Kim, C. H., Avoine, G., Koeune, F., Standaert, F. X., & Pereira, O. (2009). The swiss-knife RFID distance bounding protocol. In P. J. Lee & J. H. Cheon (Eds.), LNCS (Vol. 5461), Information security and cryptology (ICISC 2009) ( pp. 98–115) Heiledberg: Springer.
Kim, J. S., Cho, K., Yum, D. H., Hong, S. J., & Lee, P. J. (2012). Lightweight distance bounding protocol against relay attacks. IEICE Transactions on Information and Systems, E95-D(4), 1155–1158.
Koukopoulos, D., & Styliaras, G. (2013). Design of trustworthy smartphone-based multimedia services in cultural environments. Electronic Commerce Research, 13(2), 129–150.
Maheshwari, R., Gao, J., & Das, S. R. (2007). Detecting wormhole attacks in wireless networks using connectivity information. In Proceedings of the 26th international conference on computer communications (INFOCOM 2007) (pp. 107–115). Alaska, USA.
Munilla, J., & Peinado, A. (2008). Security analysis of Tu and Piramuthu’s protocol. In Proceedings of the 2nd international conference on new technologies, mobility and security (NTMS 2008) (pp. 1–5). Tangier, Morocco.
Peris-Lopez, P., Hernández-Castro, J. C., Estévez-Tapiador, J. M., & van der Lubbe, J. C. A. (2009). Shedding some light on RFID distance bounding protocols and terrorist attacks. arXiv.org, Computer science, cryptography and security.
Ranganathan, A., Tippenhauer, N. O., Škorić, B., Singelée, D., & Čapkun, S. (2012). Design and implementation of a terrorist fraud resilient distance bounding system. In S. Foresti, M. Yung & F. Martinelli (Eds.), LNCS (Vol. 7459), Computer security (ESORICS 2012) (pp. 415–432) Heiledberg: Springer.
Reid, J. F., Gonzalez-Nieto, J. M., Tang, T., & Senadji, B. (2007). Detecting relay attacks with timing-based protocols. In Proceedings of the 2nd symposium on information, computer and communications security (pp. 204–213). New York: ACM.
Scarle, S., Arnab, S., Dunwell, I., Petridis, P., Protopsaltis, A., & de Freitas, S. (2012). E-commerce transactions in a virtual environment: Virtual transactions. Electronic Commerce Research, 12(3), 379–407.
Shi, F., Liu, W., Jin, D., & Song, J. (2013). A countermeasure against wormhole attacks in MANETs using analytical hierarchy process methodology. Electronic Commerce Research.
Singelee, D., & Preneel, B. (2005). Location verification using secure distance bounding protocols. In Proceedings of the 2nd international conference on mobile adhoc and sensor systems (MASS 2005) (pp. 834–840). Washington, DC.
Thevenon, P., Savry, O., & Tedjini, S. (2011). On the weakness of contactless systems under relay attacks. In Proceedings of the 19th international conference on software, telecommunications and computer networks (SoftCOM 2011) (pp. 1–5). Split, Croatia.
Tu, Y. J., & Piramuthu, S. (2007). RFID distance bounding protocols. In Proceedings of the 1st international EURASIP workshop on RFID technology, Vienna, Austria.
Yum, D. H., Kim, J. S., Hong, S. J., & Lee, P. J. (2011). Distance bounding protocol for mutual authentication. IEEE Transactions on Wireless Communications, 10(2), 592–601.
Yum, D. H., Kim, J. S., Hong, S. J., & Lee, P. J. (2011). Distance bounding protocol with adjustable false acceptance rate. IEEE Communications Letters, 15(4), 434–436.
Zhou, T. (2013). An empirical examination of user adoption of location-based services. Electronic Commerce Research, 13(1), 25–39.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Falahati, A., Jannati, H. All-or-nothing approach to protect a distance bounding protocol against terrorist fraud attack for low-cost devices. Electron Commer Res 15, 75–95 (2015). https://doi.org/10.1007/s10660-014-9167-y
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10660-014-9167-y