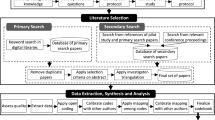
Abstract
In recent years, web security has been viewed in the context of securing the web application layer from attacks by unauthorized users. The vulnerabilities existing in the web application layer have been attributed either to using an inappropriate software development model to guide the development process, or the use of a software development model that does not consider security as a key factor. Therefore, this systematic literature review is conducted to investigate the various security development models used to secure the web application layer, the security approaches or techniques used in the process, the stages in the development model in which the approaches or techniques are emphasized, and the tools and mechanism used to detect vulnerabilities. The study extracted 499 publications from respectable scientific sources, i.e. the IEEE Computer Society, ACM Digital Library, Google-Scholar, Science Direct, Scopus, Springer Link and ISI Web. After investigation, only 43 key primary studies were considered for this review based on defined inclusion and exclusion criteria. From the review, it appears that no one development model is referred to as a standard or preferred model for web application development. However, agile development models seem to have gained more attention, probably due to the multiple stakeholders that are involved in discussing security viewpoints, rather than a few members of the development team. It appears also that there is consistency in the use of the threat-modeling technique, probably due to its effectiveness in dealing with different kinds of vulnerabilities.
Similar content being viewed by others
References
Alalfi MH, Cordy JR, Dean TR (2009) A verification framework for access control in dynamic web applications. Paper presented at the Proceedings of the 2nd Canadian conference on computer science and software engineering, Montreal, Quebec, Canada
Aydal EG, Paige RF, Chivers H, Brooke PJ (2006) Security planning and refactoring in extreme programming. Lecture Notes in Computer Science, vol 4044
Bala MS, Norita MN (2011) Secure E-commerce web development framework. Inf Technol J 10(4):769–779
Balzarotti D, Cova M, Felmetsger VV, Vigna G (2007) Multi-module vulnerability analysis of web-based applications. Paper presented at the Proceedings of the 14th ACM conference on computer and communications security, Alexandria, Virginia, USA
Blanco C, Lasheras J, Valencia-Garcia R, Fernandez-Medina E, Toval A, Piattini MA (2008) Systematic review and comparison of security ontologies. In: Availability, reliability and security, 2008. ARES 08. Third international conference on, 4–7 March 2008, pp 813–820. doi:10.1109/ares.2008.33
Cachia E, Micallef M (2007) A Multi-Tier, multi-role security framework for E-commerce systems. Paper presented at the Proceedings of the 14th annual IEEE international conference and workshops on the engineering of computer-based systems
Choi KC, Lee GH (2006) Automatic test approach of web application for security (AutoInspect). Lecture Notes in Computer Science 3983:659–668
Chong S, Liu J, Myers AC, Qi X, Vikram K, Zheng L, Zheng X, (2009) Building secure web applications with automatic partitioning. Commun ACM 52(2):79–87. doi:10.1145/1461928.1461949
Dadeau F, Potet ML, Tissot R (2008) AB formal framework for security developments in the domain of smart card applications. In: Proceedings of the Ifip Tc 11 23rd international information security conference on, 7–10 Sept 2008, Springer, pp 141–155, Milano, Italy. doi:10.1007/978-0-387-09699-5_10
Dimitrakos T, Raptis D, Ritchie B, Stølen K (2002) Model-based security risk analysis for web applications: the CORAS approach. In: Proceedings of the EuroWeb 2002, (Electronic Workshops in Computing). British Computer Society, St Anne’s College, Oxford, UK. Available on-line at: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.195.6095&rep=rep1&type=pdf
Dong J, Peng T, Zhao Y (2010) Automated verification of security pattern compositions. Inf Softw Technol 52(3):274–295
Dyba T, Dingsoyr T (2008) Empirical studies of agile software development: a systematic review. Inf Softw Technol 50(9–10):833–859
Fernandez EB (2007) Security patterns and secure systems design. Paper presented at the Proceedings of the 45th annual southeast regional conference, Winston-Salem, North Carolina
Futcher L, Solms R (2007) SecSDM: a model for integrating security into the software development life cycle. In: IFIP international federation for information processing, Boston, pp 41–48
Ge X, Paige RF, Polack FAC, Chivers H, Brooke PJ (2006) Agile development of secure web applications. Paper presented at the Proceedings of the 6th international conference on web engineering, Palo Alto, California, USA, pp 305–312. doi:10.1145/1145581.1145641
Gürgens S, Ochsenschläger P, Rudolph C (2005) On a formal framework for security properties. Comput Stand Interfaces 27(5):457–466
Halfond WGJ, Orso A (2005) AMNESIA: analysis and monitoring for NEutralizing SQL-injection attacks. Paper presented at the Proceedings of the 20th IEEE/ACM international conference on automated software engineering, Long Beach, CA, USA
Hassan R, Bohner S, El-Kassas S, Eltoweissy M (2008) Goal-oriented, B-based formal derivation of security design specifications from security requirements. In: Availability, reliability and security, 2008. ARES 2008. Third international conference on, 4–7 March 2008, pp 1443–1450. doi:10.1109/ares.2008.77
Hermosillo G, Gomez R, Seinturier L, Duchien L (2007) AProSec: an aspect for programming secure web applications. In: Conference the second international on availability, reliability and security, Vienna, pp 1026–1033
Huang YW, Huang SK, Lin TP, Tsai CH (2003) Web application security assessment by fault injection and behavior monitoring. Paper presented at the Proceedings of the 12th international conference on World Wide Web, Budapest, Hungary
Huang YW, Yu F, Hang C, Tsai CH, Lee DT, Kuo SY (2004) Securing web application code by static analysis and runtime protection. Paper presented at the Proceedings of the 13th international conference on World Wide Web, New York, NY, USA
Huang Y, Geng X, Whinston AB (2007) Defeating DDoS attacks by fixing the incentive chain. ACM Trans Internet Technol 7(1):5. doi:10.1145/1189740.1189745
Jones R, Rastogi A (2004) Secure coding: building security into the software development, life cycle 29-39
Kals S, Kirda E, Kruegel C, Jovanovic N (2006) SecuBat: a web vulnerability scanner. Paper presented at the Proceedings of the 15th international conference on World Wide Web, Edinburgh, Scotland
Keramati H, Mirian-Hosseinabadi S-H (2008) Integrating software development security activities with agile methodologies. Paper presented at the Proceedings of the 2008 IEEE/ACS international conference on computer systems and applications
Kim YG, Cha S (2012) Threat scenario-based security risk analysis using use case modeling in information systems. Secur Commun Netw 5(3):293–300. doi:10.1002/sec.321
Kitchenham B (2007) Guidelines for performing systematic literature reviews in software engineering, Version 2.3, EBSE Technical Report EBSE-2007-01, Keele University and University of Durham
Lam MS, Martin M, Livshits B, Whaley J (2008) Securing web applications with static and dynamic information flow tracking. Paper presented at the Proceedings of the 2008 ACM SIGPLAN symposium on partial evaluation and semantics-based program manipulation, San Francisco, California, USA
Lipner S (2004) The trustworthy computing security development lifecycle. Paper presented at the Proceedings of the 20th annual computer security applications conference
Livshits B, Erlingsson l (2007) Using web application construction frameworks to protect against code injection attacks. Paper presented at the Proceedings of the 2007 workshop on programming languages and analysis for security, San Diego, California, USA
Lucas FJ, Molina F, Toval A (2009) A systematic review of UML model consistency management. Inf Softw Technol 51(12):1631–1645
Mao L (2006) Research of electronic commerce systems modeling method on RUP. Dyn Continuous Discret Impuls Syst Ser B Appl Algorithms 13:731–734
Mellado D, Blanco C, Sánchez LE, Fernández-Medina E (2010a) A systematic review of security requirements engineering. Comput Stand Interfaces 32(4):153–165
Mellado D, Fernandez ME, Piattini M (2010b) Security requirements engineering framework for software product lines. Inf Softw Technol 52(10):1094–1117
Moebius N, Haneberg D, Reif W, Schellhorn G(2007) A modeling framework for the development of provably secure E-commerce applications. In: Software engineering advances, 2007. ICSEA 2007. International conference on, 25–31 August 2007, pp 8–8
Moffett JD, Nuseibeh BA, (2006) A framework for security requirements engineering. Softw Engineering for secure systems workshop with the 28th Int”l conference software engineering, Shanghai, China, pp 35–41
Moja LP, Telaro E, D’Amico R, Moschetti I, Coe L, Liberati A (2005) Assessment of methodological quality of primary studies by systematic reviews: results of the metaquality cross sectional study. BMJ 330(7499):1053. doi:10.1136/bmj.38414.515938.8F
Mourad A, Laverdière M, Debbabi M (2008) An aspect-oriented approach for the systematic security hardening of code. Comput Secur 27(3–4):101–114
Mouratidis H, Jürjens J, Fox J (2006) Towards a comprehensive framework for secure systems development. Paper presented at the 18th International conference on advanced information systems engineering, CAiSE 2006, Luxembourg, 5–9 June, 2006
Okubo T, Tanaka H (2007) Secure software development through coding conventions and frameworks. In: Availability, reliability and security, 2007. ARES 2007. The second international conference on, 10–13 April 2007, pp 1042–1051
Olsen BMJ, O, Middleton P, Ezzo J, Gotzsche PC, Hadhazy V, Herxheimer A, Kleijnen J, McIntosh H (2001) Quality of cochrane reviews: assessment of sample from 1998. BMJ 323(7317):829–832. doi:10.1136/bmj.323.7317.829
Oxman AD (1994) Systematic reviews: checklists for review articles. BMJ 309(6955):648–651
Popp G, Jurjens J, Wimmel G, Breu R (2003)Security-critical system development with extended use cases. In: Software engineering conference, 2003. Tenth Asia-Pacific, 10–12 Dec 2003, pp 478–487
Schumacher M, Ackermann R, Steinmetz R (2000) Towards security at all stages of a system’s life cycle. In: Proceedings of international conference on software, telecommunications, and computer networks (Softcom), 2000
Scott D, Sharp R (2002) Developing secure Web applications. Internet Comput IEEE 6(6):38–45
Seo SC, You JH, Kim YD, Choi JY, Lee SJ, Kim BK, (2005) Building security requirements using state transition diagram at security threat location. Lecture Notes in Computer Science 3802:451–456
Sharma S, Sugumaran V, Rajakopalan B (2002) Framework for creating hybrid-open source software communittees. Inf Syst J 12(1):7–25
Stuttard D, Pinto M (2008) The web application hacker’s handbook: discovering and exploiting security flaws. Wiley, Indianapolis
Sulayman M (2009) A systematic literature review of software process improvement for small and medium Web companies. The University of Auckland, New Zealand
Sulayman M, Mendes E (2009) A systematic literature review of software process improvement in small and medium web companies. In: Advances in software engineering, vol 59. Communications in computer and information science. Springer, Berlin, Heidelberg, pp 1–8. doi:10.1007/978-3-642-10619-4_1
Tappenden A, Beatty P, Miller J, Geras A, Smith M, IEEE Computer SOC (2005) Agile security testing of Web-based systems via HTTPUnit. AGILE 2005, Proceedings
Vidakovic D, Simic D (2007) A novel approach to building secure systems. In: Availability, reliability and security, 2007. ARES 2007. The second international conference on, 10–13 April 2007, pp 1074–1084
Viega J, McGraw G (2001) Building secure software. Addison-Wesley, Boston
Viega J, McGraw G (2002) Token-based scanning of source code for security problems. ACM Trans Inf Syst Secur 5(3):238–261. doi:10.1145/545186.545188
Ware MS, Bowles JB, (2006) Eastman CM using the common criteria to elicit security requirements with use cases. In: SoutheastCon, 2006. Proceedings of the IEEE, March 31 2005–April 2 2005, pp 273–278
Xiong P, Peyton L (2010) A model-driven penetration test framework for Web applications. In: 2010 Eighth annual international conference on privacy security and trust (PST), Ottawa, 17–19 Aug. 2010, pp 173–180
Zhang X, Wang G, Fan L (2007) Web-based coordination for E-commerce. In: IFIP advances in information and communication technology, Boston, 2007. IFIP advances in information and communication technology. Springer, Boston, pp 515-522. doi:10.1007/978-0-387-09699-5_10
Acknowledgments
We wish to thank the Library Staff of Universiti Sains Islam Malaysia and Universiti Putra Malaysia for their support in ensuring the success of retrieval process and also the reviewers for their profound support and scrutiny which assisted tremendously towards this research.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Musa Shuaibu, B., Md Norwawi, N., Selamat, M.H. et al. Systematic review of web application security development model. Artif Intell Rev 43, 259–276 (2015). https://doi.org/10.1007/s10462-012-9375-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10462-012-9375-6