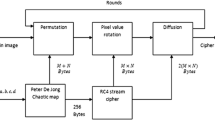
Abstract
As the systems are enabling us to transmit large chunks of data, both in the form of texts and images, there is a need to explore algorithms which can provide a higher security without increasing the time complexity significantly. This paper proposes an image encryption scheme which uses intertwining chaotic maps and RC4 stream cipher to encrypt/decrypt the images. The scheme employs chaotic map for the confusion stage and for generation of key for the RC4 cipher. The RC4 cipher uses this key to generate random sequences which are used to implement an efficient diffusion process. The algorithm is implemented in MATLAB-2016b and various performance metrics are used to evaluate its efficacy. The proposed scheme provides highly scrambled encrypted images and can resist statistical, differential and brute-force search attacks. The peak signal-to-noise ratio values are quite similar to other schemes, the entropy values are close to ideal. In addition, the scheme is very much practical since having lowest time complexity then its counterparts.








Similar content being viewed by others
References
Anuradha, K., & Naik, P. P. S. (2015). Medical image cryptanalysis using histogram matching bitplane and adjoin mapping algorithms. International Journal and Magazine of Engineering, Technology, Management and Research, 2, 100–105. http://www.ijmetmr.com/oloctober2015/KolakaluriAnuradha-PPeddaSadhuNaik-13.pdf.
Bansal, R., Gupta, S., & Sharma, G. (2016). An innovative image encryption scheme based on chaotic map and Vigenère scheme. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-016-3926-9.
Baptista, M. S. (1998). Cryptography with chaos. Physics Letters A, 240, 50–54. http://cmup.fc.up.pt/cmup/murilo.baptista/baptista_PLA1998.pdf.
Barker, W. C., & Barker, E. (2012). Recommendation for the triple data encryption algorithm (TDEA) block cipher. National Institute of Standards and Technology. Special Publication, 800–867. http://dx.doi.org/10.6028/NIST.SP.800-67r1
Basu, S. (2011). International data encryption algorithm (IDEA)—A typical illustration. Journal of Global Research in Computer Science, 2, 116–118. http://www.rroij.com/open-access/international-data-encryption-algorithm-idea-a-typical-illustration-116-118.pdf.
Biham, E., & Shamir, A. (1993). Differential cryptanalysis of the data encryption standard. Springer-Verlag. http://www.cs.technion.ac.il/~biham/Reports/differential-cryptanalysis-of-the-data-encryption-standard-biham-shamir-authors-latex-version.pdf.
Biryukov, A., & Kushilevitz, E. (1998). Improved cryptanalysis of RC5. In K. Nyberg (Ed.), Advances in cryptology—EUROCRYPT’98. EUROCRYPT 1998. Lecture notes in computer science (Vol. 1403). Berlin: Springer. https://doi.org/10.1007/bfb0054119.
Chang, C. C., Hwang, M. S., & Chen, T. S. (2001). A new encryption algorithm for image cryptosystems. Journal of Systems and Software, 58, 83–91. https://doi.org/10.1016/S0164-1212(01)00029-2.
Chen, G., Mao, Y., & Chui, C. K. (2004). A symmetric image encryption based on 3D chaotic maps. Chaos, Solitons & Fractals, 21, 749–761. https://doi.org/10.1016/j.chaos.2003.12.022.
Dang, P. P., & Chau, P. M. (2000). Image encryption for secure internet multimedia applications. IEEE Transactions on Consumer Electronics, 46, 395–403. https://doi.org/10.1109/30.883383.
Ferguson, N., et al. (2001). Improved cryptanalysis of Rijndael. In G. Goos, J. Hartmanis, J. van Leeuwen, & B. Schneier (Eds.), Fast software encryption. FSE 2000. Lecture notes in computer science (Vol. 1978). Berlin: Springer. https://doi.org/10.1007/3-540-44706-7_15.
François, M., Grosges, T., Barchiesi, D., & Erra, R. (2012). A new image encryption scheme based on a chaotic function. Signal Processing: Image Communication, 27, 249–259. https://doi.org/10.1016/j.image.2011.11.003.
Gao, T., & Chen, Z. (2008). A new image encryption algorithm based on hyper-chaos. Physics Letters A, 372, 394–400. https://doi.org/10.1016/j.physleta.2007.07.040.
Hanchinamani, G., & Kulkarni, L. (2015). An efficient image encryption scheme based on a Peter De Jong chaotic map and a RC4 stream cipher. 3D. Research, 6, 30. https://doi.org/10.1007/s13319-015-0062-7.
Jawad, L. M., & Sulong, G. (2015). Chaotic map-embedded Blowfish algorithm for security enhancement of colour image encryption. Nonlinear Dynamics, 81(4), 2079–2093. https://doi.org/10.1007/s11071-015-2127-9.
Jianquan, X., Chunhua, Y., Qing, X., Lijun, T. (2009). An encryption algorithm based on transformed logistic map. In International conference on networks security, wireless communications and trusted computing (pp. 111–114). https://doi.org/10.1109/nswctc.2009.201.
Karuvandan, V., Chellamuthu, S., & Periyasamy, S. (2016). Cryptanalysis of AES-128 and AES-256 block ciphers using Lorenz information measure. The International Arab Journal of Information Technology, 13, 306–312. http://ccis2k.org/iajit/PDF/Vol.13,%20No.3/5373.pdf.
Knudsen, L. R., & Meier, W. (2001). Correlations in RC6 with a reduced number of rounds. In G. Goos, J. Hartmanis, J. van Leeuwen, & B. Schneier (Eds.), Fast software encryption. FSE 2000. Lecture notes in computer science (Vol. 1978). Berlin: Springer. https://doi.org/10.1007/3-540-44706-7_7.
Kocarev, L., & Lian, S. (2011). Chaos based cryptography theory algorithms and applications. Springer-Verlag. https://doi.org/10.1007/978-3-642-20542-2.
Kumar, S., & Sharma, R. K. (2016). Securing color images using two-square cipher associated with Arnold map. Multimedia Tools and Applications. https://doi.org/10.1007/s11042-016-3504-1.
Kumara, M., Mishra, D. C., & Sharma, R. K. (2014). A first approach on an RGB image encryption. Journal of Optics and Lasers in Engineering, 52, 27–34.
Li, C., Li, S., Asim, M., Nunez, J., Alvarez, G., & Chen, G. (2009). On the security defects of an image encryption scheme. Image and Vision Computing, 27, 1371–1381. https://doi.org/10.1016/j.imavis.2008.12.008.
Liu, F., & Liu, Y. (2016). Research on image encryption based on Lorenz chaotic mapping in finite field. International Journal of Hybrid Information Technology, 9(10), 281–288. https://doi.org/10.14257/ijhit.2016.9.10.28.
Liu, L., & Miao, S. (2016). A new image encryption algorithm based on logistic chaotic map with varying parameter. SpringerPlus, 5, 289. https://doi.org/10.1186/s40064-016-1959-1.
Liu, Z., Guo, Q., Xu, L., Ahmad, M. A., & Liu, S. (2010). Double image encryption by using iterative random binary encoding in gyrator domains. Optics Express, 18, 12033–12043. https://doi.org/10.1364/OE.18.012033.
Lucks, S. (1998). Attacking triple encryption. In S. Vaudenay (Ed.), Fast software encryption. FSE 1998. Lecture notes in computer science (Vol. 1372). Berlin: Springer. https://doi.org/10.1007/3-540-69710-1_16.
Matthews, R. (1989). On the derivation of a “chaotic” encryption algorithm. Cryptologia, 14, 29–42. https://doi.org/10.1080/0161-118991863745.
Mishra, D. C., & Sharma, R. K. (2016). An approach for security of color image data in coordinate, geometric, and frequency domains. Journal Information Security Journal: A Global Perspective, 25(4–6), 213–234.
Mishra, D. C., Sharma, R. K., Suman, S., & Prasad, A. (2017). Multi-layer security of color image based on chaotic system combined with RP2DFRFT and Arnold transform. Journal of Information Security and Applications, 37, 65–90.
Mousa, A., & Hamad, A. (2006). Evaluation of the RC4 algorithm for data encryption. International Journal of Computer Science & Applications, 3, 44–56. http://www.tmrfindia.org/ijcsa/v3i24.pdf.
Pareek, N. K., Patidar, V., & Sud, K. K. (2003). Discrete chaotic cryptography using external key. Physics Letters A, 309, 75–82. https://doi.org/10.1016/S0375-9601(03)00122-1.
Pareek, N. K., Patidar, V., & Sud, K. K. (2006). Image encryption using chaotic logistic map. Image and Vision Computing, 24, 926–934. https://doi.org/10.1016/j.imavis.2006.02.021.
Rehman, A. U., Khan, J. S., Ahmad, J., & Hwang, S. O. (2016). A new image encryption scheme based on dynamic S-boxes and chaotic maps. 3D Research, 7(7), 7. https://doi.org/10.1007/s13319-016-0084-9.
Rivest, R. L. (1995). RC5 encryption algorithm. Dr Dobb’s Journal, 226, 146–148. http://www.drdobbs.com/security/the-rc5-encryption-algorithm/184409480.
Rivest, R. L., & Schuldt, J. C. N. (2014). Spritz—a spongy RC4-like stream cipher and hash function. In Proceedings of the Charles River Crypto Day, Palo Alto, CA, USA. https://people.csail.mit.edu/rivest/pubs/RS14.pdf.
Sam, I. S., Devaraj, P., & Bhuvaneswaran, R. S. (2012). A novel image cipher based on mixed transformed logistic maps. Multimedia Tools and Applications, 56, 315–330. https://doi.org/10.1007/s11042-010-0652-6.
Sam, I. S., Devaraj, P., & Bhuvaneswaran, R. S. (2012). An intertwining chaotic maps based image encryption scheme. Nonlinear Dynamics, 69, 1995–2007. https://doi.org/10.1007/s11071-012-0402-6.
Scharinger, J. (1998). Fast encryption of image data using chaotic Kolmogorov flows. Journal of Electronic Engineering, 7, 318–325. https://doi.org/10.1117/1.482647.
Schneier, B. (1994). The Blowfish encryption algorithm. Dr. Dobb’s Journal, 19, 38–40. http://www.drdobbs.com/security/the-blowfish-encryption-algorithm/184409216.
Shimoyama, T., Takenaka, M., & Koshiba, T. (2002). Multiple linear cryptanalysis of a reduced round RC6. In J. Daemen & V. Rijmen (Eds.), Fast software encryption. FSE 2002. Lecture notes in computer science (Vol. 2365). Berlin: Springer. https://doi.org/10.1007/3-540-45661-9_6.
Solak, E., Çokal, C., Yildiz, O. T., & Biyikoğlu, T. (2010). Cryptanalysis of Fridrich’s chaotic image encryption. International Journal of Bifurcation and Chaos, 10, 1405–1413. https://doi.org/10.1142/S0218127410026563.
Tayal, N., Bansal, R., Gupta, S., & Dhall, S. (2016). Analysis of various cryptography techniques: A survey. International Journal of Security and Its Applications, 10, 59–92. https://doi.org/10.14257/ijsia.2016.10.8.07.
The next tier, 8 security predictions for 2017, https://www.trendmicro.ae/vinfo/ae/security/research-and-analysis/predictions/2017.
Ye, G. (2010). Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recognition Letters, 31, 347–354. https://doi.org/10.1016/j.patrec.2009.11.008.
Yoon, J. W., & Kim, H. (2010). An image encryption scheme with a pseudorandom permutation based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation, 15, 3998–4006. https://doi.org/10.1016/j.cnsns.2010.01.041.
Younes, M. A. B., & Jantan. A. (2008). Image encryption using block-based transformation algorithm. International Journal of Computer Science, 35, 407–415. http://www.iaeng.org/IJCS/issues_v35/issue_1/IJCS_35_1_03.pdf.
Yu, X. Y., Zhang, J., Ren, H. E., Xu, G. S., & Luo, X. Y. (2006). Chaotic image scrambling algorithm based on S-DES. Journal of Physics: Conference Series, 48, 349–353. https://doi.org/10.1088/1742-6596/48/1/065.
Yun-peng, Z., Zheng-jun, Z., Wei, L., Xuan, N., Shui-ping, C., & Wei-di. D. (2009). Digital image encryption algorithm based on chaos and improved DES. In IEEE international conference on systems, man, and cybernetics (pp. 474–479). https://doi.org/10.1109/icsmc.2009.5346839.
Zeghid, M., Machhout, M., Khriji, L., Baganne, A., & Tourki, R. (2007). A modified AES based algorithm for image encryption. International Journal of Computer, Electrical, Automation, Control and Information Engineering, 1, 745–750. http://scholar.waset.org/1307-6892/7580.
Zhang, G., & Liu, Q. (2011). A novel image encryption method based on total shuffling scheme. Optics Communications, 284, 2775–2780. https://doi.org/10.1016/j.optcom.2011.02.039.
Zhang, Y., Xiao, D., Wen, W., et al. (2014). Cryptanalysis of image scrambling based on chaotic sequences and Vigenère cipher. Nonlinear Dynamics, 78, 235. https://doi.org/10.1007/s11071-014-1435-9.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kumari, M., Gupta, S. A Novel Image Encryption Scheme Based on Intertwining Chaotic Maps and RC4 Stream Cipher. 3D Res 9, 10 (2018). https://doi.org/10.1007/s13319-018-0162-2
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13319-018-0162-2