Abstract
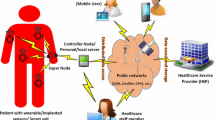
Location-based services (LBS) and information security is a major concern in communication system.With the increasing popularity of location based services more attention is paid to preserve location information to protect the data. In order to protect and preserve the MANET and location based services, there are various existing location based anonymity protocols such as k-anonymity location based, but these protocols are more overhead due to the dynamic mobility nature of ad-hoc networks. In this paper we proposed an Adaptive Risk Prediction and Anonymous Secured Communication protocol to predict the risk before processing anonymous communication. The proposed protocol estimates the risk against adjacent nodes and estimates the vulnerability paths using hidden markov model and decision tree. The decision tree determines the evidence to identify the trusted paths. The anonymous communication message authentication scheme assigns the anonymous communication and organize the secured authentication scheme. We simulated the network by considering different attacks to determine the efficiency of Adaptive Risk Prediction and Anonymous Secured Communication using NS2 simulator.










Similar content being viewed by others
References
Koh, J. Y., Nevat, I., Leong, D., and Wong, W.-C., Geo-spatial location spoofing detection for Internet of Things. IEEE Internet Things J. 3(6):971–978, 2016.
Wang, C., Lin, H., and Jiang, H., CANS: Towards congestion-adaptive and small stretch emergency navigation with wireless sensor networks. IEEE Trans. Mobile Comput. 15(5):1077–1089, 2016.
Baiardi, F., Falleni, A., Granchi, R., Martinelli, F., Petrocchi, M., and Vaccarelli, A., Seas, a secure e-voting protocol: Design and implementation. Comput. Secur. 24(8):642–652, 2005.
Shepard, S. S., Dong, R., Kresman, R., and Dunning, L., Anonymous id assignment and opt-out. In: Ao, S., Gleman, L. (Eds), Lecture notes in electrical engineering. New York: Springer, 2010, 420–431.
Zhao, Z., Hu, H., Ahn, G.-J., and Wu, R., Risk-aware response for mitigating MANET routing attacks. IEEE Transactions on Dependable and Secure Computing 9(2), 2012.
Zhao, P., Li, J., Zeng, F., Xiao, F., Wang, C., and Jiang, H., ILLIA: Enabling k-anonymity-based privacy preserving against location injection attacks in continuous LBS queries. IEEE Internet Things J. 5(2), 2018.
Cui, J., Wen, J., Han, S., and Zhong, H., Efficient privacy-preserving scheme for real-time location data in vehicular ad-hoc network, 2327–4662 (c) IEEE, 2018.
Memon, I., Hussain, I., Akhtar, R., and Chen, G., Enhanced privacy and authentication: An efficient and secure anonymous communication for location based service using asymmetric cryptography scheme. New York: Springer Science+Business Media, 2017. https://doi.org/10.1007/s11277-015-2699-1
Sarathamani, T., and Babu, D. M. R., Robust and secure anonymity based routing protocol in manet. Journal of Advanced Research in Dynamical and Control Systems 9(6), 2017.
Xia, H., Li, Z., Zheng, Y., Liu, A., Choi, Y.-J., and Sekiya, H., A novel light-weight subjective trust inference framework in MANETs, IEEE transactions on sustainable computing, manuscript tsusc-2017-07-0063.
Cai, F., Ming, L., Jing, C., Li, Z., and Liu, X., A projection pursuit based risk assessment method in mobile ad hoc networks. International Journal of Computational Intelligence Systems 4(5):749–758, 2011.
Liu, A., Joy, A., and Thompson, R., A dynamic trust model for mobile ad hoc networks. In: Proceedings of 10th IEEE Int'l Workshop Future Trends Of Distributed Computing Systems (Ftdcs '04), 80–85, 2004.
Dai, H., Jia, Z., and Kin, Z., Trust evaluation and dynamic routing decision based on fuzzy theory for MANETs. Journal of Software 4(10):1091–1101, 2009.
Zhang, Y., and Lee, W., Intrusion detection in wireless ad-hoc networks. In: Proceedings of the sixth annual international conference on mobile computing and networking, Boston, 2000.
Bhargava, S., and Agrawal, D., Security enhancements in AODV protocol for wireless ad hoc networks. Proceedings of Vehicular Technology Conference (VTC) Fall, 4:2143–2147, 2001.
Mishra, A., Nadkarni, A., and Patcha, A intrusion detection in wireless adhoc networks. IEEE Wirel. Commun. 11(1):48–60, 2004.
Takagi, H., and Kleinrock, L., Optimal transmission ranges for randomly distributed packet radio terminals. IEEE Trans. Commun. 32(3):246–257, 1984.
Cao, Y., and Xie, S. A position based beaconless routing algorithm for mobile ad hoc networks. Proceedings of the International Conference on Communications, Circuits and Systems 1(1):303–307, 2005.
Giruka, V., and Singhal, M., Angular routing protocol for mobile ad-hoc networks. IEEE international conference on distributed computing systems workshops. Columbus, OH. 2005.
Bing, W. U. et al., Network-based malcode detection technology. J. Commun.:87–91, 2007.
Ritchey, R. W et al., Using model checking to analyze network vulnerabilities. IEEE Conference on Security and Privacy, 2000.
Beaudoin, L. et al., Asset valuation technique for network management and security. IEEE Conference on Data Mining Workshops, 2006.
Shen, D. et al., Adaptive Markov game theoretic data fusion approach for cyber network defense. IEEE Conference on Military Communications, 2007.
Cardenas, A. A., Ramezani, V., and Baras, J. S., HMM Sequential Hypothesis Tests for Intrusion Detection in MANETs, U.S. Army Research Office under Award No. DAAD19–01-1-0494 t
Estahbanati, M. M., Rasti, M., and Hamami, S. M. S., A mobile ad hoc network routing based on energy and Markov chain trust
Das, S., Mukhopadhyay, A., Saha, D., and Sadhukhan, S., A Markov-Based model for information security risk assessment in healthcare MANETs. Springer Science+Business Media, LLC, 2017.
Kannan, A., Sathiyamoorthy, E., A decision tree-based rule formation with combined PSO-GA algorithm for intrusion detection system. In: International Journal of Internet Technology and Secured Transactions Vol 6, no: 186, 2016.
Cayirci, E., Ghergherehchi, R., Modeling cyber attacks and their effects on decision process. Proceedings of the 2011 Winter Simulation Conference.
Network simulator <http://www.isi.edu/nsnam/ns>.
Lu, H., Li, J., and Guizani, M., Secure and efficient data transmission for cluster-based wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 25(3):750–761, 2014.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Ambidi, N., Katta, R.L.R. Adaptive Risk Prediction and Anonymous Secured Communication in MANET for Medical Informatics. J Med Syst 43, 115 (2019). https://doi.org/10.1007/s10916-019-1231-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-019-1231-7