Abstract
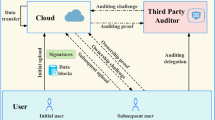
The public cloud storage auditing with deduplication has been studied to assure the data integrity and improve the storage efficiency for cloud storage in recent years. The cloud, however, has to store the link between the file and its data owners to support the valid data downloading in previous schemes. From this file-owner link, the cloud server can identify which users own the same file. It might expose the sensitive relationship among data owners of this multi-owners file, which seriously harms the data owners’ privacy. To address this problem, we propose an identity-protected secure auditing and deduplicating data scheme in this paper. In the proposed scheme, the cloud cannot learn any useful information on the relationship of data owners. Different from existing schemes, the cloud does not need to store the file-owner link for supporting valid data downloading. Instead, when the user downloads the file, he only needs to anonymously submit a credential to the cloud, and can download the file only if this credential is valid. Except this main contribution, our scheme has the following advantages over existing schemes. First, the proposed scheme achieves the constant storage, that is, the storage space is fully independent of the number of the data owners possessing the same file. Second, the proposed scheme achieves the constant computation. Only the first uploader needs to generate the authenticator for each file block, while subsequent owners do not need to generate it any longer. As a result, our scheme greatly reduces the storage overhead of the cloud and the computation overhead of data owners. The security analysis and experimental results show that our scheme is secure and efficient.







Similar content being viewed by others
References
Ateniese, G., Burns, R., Curtmola, R., Herring, J., Kissner, L., Peterson, Z., Song, D.: Provable data possession at untrusted stored. In: Proceeding of the 14th ACM Conference on Computer and Communication Security, pp. 598–609 (2007)
Ateniese, G., Pietro, R., Mancini, L., Tsudik, G.: Scalable and efficient provable data possession. In: Proceeding of the 4th ACM Conference on Computer and Communications Security, pp. 1–10 (2008)
Aggarwal, M., Jain, P., Krishna, G.: File specific deduplication for cloud storages. Int. J. Appl. Res. Inf. Technol. Comput. 8(3), 293–302 (2017)
Bellare, M., Goldreich, O.: On defining proofs of knowledge. In: Proceeding of the 12th Annual International Cryptology Conference, pp. 390–420 (1992)
Bellare, M., Keelveedhi, S., Ristenpart, T.: Message-locked encryption and secure deduplication. In: Proceeding of Annual International Conference on the Theory and Applications of Cryptographic Techniques, pp. 296–312 (2013)
Boneh, D., Lynn, B., Shacham, H.: Short signatures from the Weil pairing. In: Proceeding of Advances in Cryptology Asiacrypt, pp. 514–532 (2001)
Gantz, J., Reinsel, D.: The digital universe decade-are you ready? http://www.emc.com/collateral/analyst-reports/idc-digital-universe-are-you-ready.pdf (2010)
Halevi, S., Harnik, D., Pinkas, B., Shulman-Peleg, A.: Proofs of ownership in remote storage systems. In: Proceeding of the 18th ACM Conference on Computer and Communications Security, pp. 491–500 (2011)
Li, J., Li, J., Xie, D., Cai, Z.: Secure auditing and deduplicating data in cloud. IEEE Trans. Comput. 65(8), 2386–2396 (2016)
Liu, C., Ranjan, R., Zhang, X., Yang, C., Georgakopoulos, D., Chen, J.: Public auditing for big data storage in cloud computing—a survey. In: Proceeding of the 16th IEEE International Computational Science and Engineering, pp. 1128–1135 (2013)
Pairing-Based Cryptography (PBC) library. https://crypto.stanford.edu/pbc/howto.html
Pietro, R., Sorniotti, A.: Boosting efficiency and security in proof of ownership for deduplication. In: Proceeding of the 7th ACM Symposium on Information, Computer and Communications Security, pp. 81–82 (2012)
Shacham, H., Waters, B.: Compact proofs of retrievability. In: Proceeding of the 14th International Conference on the Theory and Application of Cryptology and Information Security, pp. 90–107 (2008)
Shen, W., Yang, G., Yu, J., Zhang, H., Kong, F., Hao, R.: Remote data possession checking with privacy preserving authenticators for cloud storage. Future Gener. Comput. Syst. 76, 136–145 (2017)
Shen, W., Yu, J., Xia, H., Zhang, H., Lu, X., Hao, R.: Light-weight and privacy-preserving secure cloud auditing scheme for group users via the third party medium. J. Netw. Comput. Appl. 82, 56–64 (2017)
Wang, C., Chow, S., Wang, Q., Ren, K., Lou, W.: Privacy preserving public auditing for secure cloud storage. IEEE Trans. Comput. 62(2), 362–375 (2013)
Wang, C., Wang, Q., Ren, K., Lou, W.: Privacy-preserving public auditing for data storage security in cloud computing. In: Proceeding of IEEE Conference on Computer Communications, pp. 525–533 (2010)
Wang, H.: Identity-based distributed provable data possession in multicloud storage. IEEE Trans. Serv. Comput. 8(2), 328–340 (2015)
Wang, H., He, D., Yu, J., Wang, Z.: Incentive and unconditionally anonymous identity-based public provable data possession. IEEE Trans. Serv. Comput. (2016). https://doi.org/10.1109/tsc.2016.2633260
Yang, G., Yu, J., Shen, W., Su, Q., Zhang, F., Hao, R.: Enabling public auditing for shared data in cloud storage supporting identity privacy and traceability. J. Syst. Softw. 113, 130–139 (2016)
Yu, J., Hao, R., Xia, H., Zhang, H., Cheng, X., Kong, F.: Intrusion-resilient identity-based signatures: concrete scheme in the standard model and generic construction. Inf. Sci. 442, 158–172 (2018)
Yu, J., Ren, K., Wang, C.: Enabling cloud storage auditing with verifiable outsourcing of key updates. IEEE Trans. Inf. Forensics Secur. 11(6), 1362–1375 (2016)
Yu, J., Ren, K., Wang, C., Varadharajan, V.: Enabling cloud storage auditing with key-exposure resistance. IEEE Trans. Inf. Forensics Secur. 10(6), 1167–1179 (2015)
Yu, J., Wang, H.: Strong key-exposure resilient auditing for secure cloud storage. IEEE Trans. Inf. Forensics Secur. 12(8), 1931–1940 (2017)
Yuan, J., Yu, S.: Efficient public integrity checking for cloud data sharing with multi-user modification. In: Proceeding of IEEE Conference on Computer Communications, pp. 2121–2129 (2014)
Yuan, J.,Yu, S.: Secure and constant cost public cloud storage auditing with deduplication. In: IEEE Conference on Communications and Network Security, pp. 145–153 (2013)
Zheng, Q., Xu, S.: Secure and efficient proof of storage with deduplication. In: Proceeding of ACM Conference on Data and Application Security and Privacy, pp. 1–12 (2012)
Zhang, Y., Yu, J., Hao, R., Wang, C., Ren, K.: Enabling efficient user revocation in identity-based cloud storage auditing for shared big data. IEEE Trans. Dependable Secure Comput. (2018). https://doi.org/10.1109/TDSC.2018.2829880
Acknowledgements
This research is supported by National Natural Science Foundation of China (61572267, 61272425, 61702294), National Development Foundation of Cryptography (MMJJ20170118, MMJJ20170126), the Open Project of Co-Innovation Center for Information Supply & Assurance Technology, Anhui University, the Open Project of the State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences(2017-MS-21, 2016-MS-23), Jiangsu Key Laboratory of Big Data Security & Intelligent Processing, NJUPT(BDSIP1806), Natural Science Foundation of Shandong Province (ZR2015FM020, ZR2016FQ02).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hou, H., Yu, J., Zhang, H. et al. Enabling secure auditing and deduplicating data without owner-relationship exposure in cloud storage. Cluster Comput 21, 1849–1863 (2018). https://doi.org/10.1007/s10586-018-2813-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-018-2813-8