Abstract
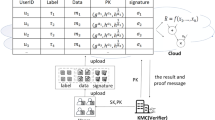
Storing the large-scale data on the cloud server side becomes nowadays an alternative for the data owner with the popularity and maturity of the cloud computing technique, where the data owner can manage the data with limited resources, and the user issues the query request to the cloud server instead of the data owner. As the server is not completely trusted, it is necessary for the user to perform results authentication to check whether or not the returned results from the cloud server are correct. We investigate in this paper how to perform efficient data update for the result authentication of the outsourced univariate linear function query. We seek to outsource almost all the data and computing to the server, and as few data and computations as possible are stored and performed on the data owner side, respectively. We present a novel scheme to achieve the security goal, which is divided into two parts. The first part is a verification algorithm for the outsourced computing of line intersections, which enables the data owner to store most of the data on the server side, and to execute less of the computing of the line intersections. The second part is an authentication data structure Two Level Merkle B Tree for the outsourced univariate linear function query, where the top level is used to index the user input and authenticate the query results, and the bottom level is used to index the query condition and authenticate the query results. The authentication data structure enables the data owner to update the data efficiently, and to implement the query on the server side. The theoretic analysis shows that our proposed scheme works with higher efficiency.





Similar content being viewed by others
References
Chen, X., Li, J., Ma, J., Tang, Q., Lou, W.: New algorithms for secure outsourcing of modular exponentiations. IEEE Trans. Parallel Distrib. Syst. 25(9), 2386–2396 (2014)
Chevalier, C., Laguillaumie, F., Vergnaud, D.: Privately outsourcing exponentiation to a single server: cryptanalysis and optimal constructions. In: Askoxylakis, I., Ioannidis, S., Katsikas, S., Meadows, C. (eds.) Proceedings of the 21st European Symposium on Research in Computer Security (ESORICS 2016), pp. 261–278. Springer, Cham (2016)
Devanbu, P.T., Gertz, M., Martel, C.U., Stubblebine, S.G.: Authentic third-party data publication. In: Proceedings of the IFIP TC11/ WG11.3 Fourteenth Annual Working Conference on Database Security: Data and Application Security, Development and Directions, pp. 101–112. Kluwer, Deventer (2001)
Fiore, D., Gennaro, R.: Publicly verifiable delegation of large polynomials and matrix computations, with applications. In: Proceedings of the 2012 ACM Conference on Computer and Communications Security (CCS ’12), pp. 501–512. ACM, New York (2012)
Hohenberger, S., Lysyanskaya, A.: How to securely outsource cryptographic computations. In: Kilian, J. (ed.) Proceedings Second Theory of Cryptography Conference (TCC 2005), Cambridge, MA, pp. 264–282. Springer, Berlin (2005)
Jia, K., Li, H., Liu, D., Yu, S.: Enabling efficient and secure outsourcing of large matrix multiplications. In: Proceedings of 2015 IEEE Global Communications Conference (GLOBECOM), pp. 1–6 (2015)
Li, F., Hadjieleftheriou, M., Kollios, G., Reyzin, L.: Dynamic authenticated index structures for outsourced databases. In: Proceedings of the 2006 ACM SIGMOD International Conference on Management of Data (SIGMOD ’06), pp. 121–132. ACM, New York (2006)
Li, F., Hadjieleftheriou, M., Kollios, G., Reyzin, L.: Authenticated index structures for aggregation queries. ACM Trans. Inf. Syst. Secur. 13(4), 747–759 (2010)
Li, H., Zhang, S., Luan, T.H., Ren, H., Dai, Y., Zhou, L.: Enabling efficient publicly verifiable outsourcing computation for matrix multiplication. In: Proceedings of 2015 International Telecommunication Networks and Applications Conference (ITNAC), pp. 44–50. IEEE, New York (2015)
Merkle, R.C.: A certified digital signature. In: Proceedings of CRYPTO ’89, Santa Barbara, CA, August 20–24, 1989, pp. 218–238 (1989)
Pang, H., Jain, A., Ramamritham, K., Tan, K.L.: Verifying completeness of relational query results in data publishing. In: Proceedings of the 2005 ACM SIGMOD International Conference on Management of Data (SIGMOD ’05), pp. 407–418. ACM, New York (2005)
Ren, Y., Ding, N., Zhang, X., Lu, H., Gu, D.: Verifiable outsourcing algorithms for modular exponentiations with improved checkability. In: Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security (ASIA CCS ’16), pp. 293–303. ACM, New York (2016)
Sheng, G., Wen, T., Guo, Q., Yin, Y.: Correctness authentication of preference top-k query in cloud computing. J. Jilin Univ. (Eng. Technol. Ed.) 44(1), 164–170 (2014)
Sheng, G., Tang, C., Gao, W., Yin, Y.: Md-\(\cal{VC}_{Matrix}\): an efficient scheme for publicly verifiable computation of outsourced matrix multiplication. In: Chen, J., Piuri, V., Su, C., Yung, M. (eds.) Proceedings of the 10th International Conference on Network and System Security (NSS 2016), pp. 349–362. Springer, Cham (2016)
Vaidya, J., Yakut, I., Basu, A.: Efficient integrity verification for outsourced collaborative filtering. In: IEEE International Conference on Data Mining, pp. 560–569 (2015)
Wang, C., Ren, K., Wang, J.: Secure and practical outsourcing of linear programming in cloud computing. Proc. IEEE INFOCOM 2011, 820–828 (2011)
Wang, C., Ren, K., Wang, J., Wang, Q.: Harnessing the cloud for securely outsourcing large-scale systems of linear equations. IEEE Trans. Parallel Distrib. Syst. 24(6), 1172–1181 (2013)
Wang, H., Yin, J.: Perng, C.S., Yu, P.S.: Dual encryption for query integrity assurance. In: Proceedings of the 17th ACM Conference on Information and Knowledge Management (CIKM ’08), pp. 863–872. ACM, New York (2008)
Wen, T., Sheng, G., Guo, Q., Sheng, G.J.: Query results authentication of outsourced append only databases. J. Comput. Res. Dev. 49(10), 2077–2085 (2012)
Xian, H., Feng, D.: An integrity checking scheme in outsourced database model. J. Comput. Res. Dev. 47(6), 1107–1115 (2010)
Xie, M., Wang, H., Yin, J., Meng, X.: Integrity auditing of outsourced data. In: Proceedings of the 33rd International Conference on Very Large Data Bases (VLDB ’07), pp. 782–793. VLDB Endowment, New York (2007)
Yang, Y., Papadopoulos, S., Papadias, D., Kollios, G.: Authenticated indexing for outsourced spatial databases. VLDB J. 18(3), 631–648 (2009)
Yang, G., Cai, Y., Hu, Z.: Authentication of function queries. In: Proceedings of IEEE 32nd International Conference on Data Engineering (ICDE 2016), pp. 337–348 (2016)
Zhao, Y., Yu, J.X., Wang, G., Chen, L., Wang, B., Yu, G.: Maximal subspace coregulated gene clustering. IEEE Trans. Knowl. Data Eng. 20(1), 83–98 (2007)
Acknowledgements
This work was supported in part by the National Natural Science Foundation of China under Grant No. 11271003, Guangdong Province Natural Science Foundation of major basic research and Cultivation Project under Grant No. 2015A030308016, Basic Research Major Projects of Department of Education Guangdong Province under Grant No. 2014KZDXM044, Innovation Team Construction Project of Guangdong Province Regular Universities under Grant No. 2015KCXTD014, Scientific Research Fund of Hunan Provincial Education Department under Grant No. 15C0536, and Collaborative Innovation Major Projects of Bureau of Education of Guangzhou City under Grant No. 1201610005.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sheng, G., Tang, C., Han, H. et al. Authentication of outsourced linear function query with efficient updates. Cluster Comput 22 (Suppl 4), 10031–10039 (2019). https://doi.org/10.1007/s10586-017-1064-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-017-1064-4