Abstract
Process mining helps infer valuable insights about business processes using event logs, whereas goal modeling focuses on the representation and analysis of competing goals of stakeholders and systems. Although there are clear benefits in mining the goals of existing processes, goal-oriented approaches that consider logs during model construction are still rare. Process mining techniques, when generalizing large instance-level data into process models, can be considered as a data-driven complement to use case/scenario elicitation. Requirements engineers can exploit process mining techniques to find new system or process requirements in order to align current practices and desired ones. This paper provides a systemic literature review, based on 24 papers rigorously selected from four popular search engines in 2018, to assess the state of goal-oriented process mining. Through two research questions, the review highlights that the use of process mining in association with goals does not yet have a coherent line of research, whereas intention mining (where goal models are mined) shows a meaningful trace of research. Research about performance indicators measuring goals associated with process mining is also sparse. Although the number of publications in process mining and goal modeling is trending up, goal mining and goal-oriented process mining remain modest research areas. Yet, synergetic effects achievable by combining goals and process mining can potentially augment the precision, rationality and interpretability of mined models and eventually improve opportunities to satisfy system stakeholders.

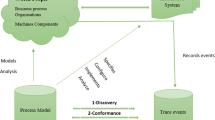
Adapted from [100]


Adapted from [115]

Adapted from [45]






Similar content being viewed by others
References
Abraham J, Reddy MC (2010) Challenges to inter-departmental coordination of patient transfers: a workflow perspective. Int J Med Informatics 79(2):112–122. https://doi.org/10.1016/j.ijmedinf.2009.11.001
Akhigbe O, Amyot D, Anda AA, Lessard L, Xiao D (2016) Consistency analysis for User Requirements Notation models. In: iStar 2016—ninth international i* workshop, CEUR-WS, vol 1674, pp 43–48
Aldin L, de Cesare S (2011) A literature review on business process modelling: new frontiers of reusability. Enterprise Inf Syst 5(3):359–383. https://doi.org/10.1080/17517575.2011.557443
Amyot D, Ghanavati S, Horkoff J, Mussbacher G, Peyton L, Yu E (2010) Evaluating goal models within the Goal-oriented Requirement Language. Int J Intell Syst 25(8):841–877. https://doi.org/10.1002/int.20433
Amyot D, Horkoff J, Gross D, Mussbacher G (2009) A lightweight GRL profile for i* modeling. In: Heuser CA, Pernul G (eds) Advances in conceptual modeling—challenging perspectives. LNCS, vol 5833. Springer. Berlin, Heidelberg, pp 254–364
Amyot D, Mussbacher G (2011) User Requirements Notation: the first ten years, the next ten years. J Softw 6(5): 747–768
Armentano MG, Amandi AA (2012) Towards a goal recognition model for the organizational memory. In: Computational science and its applications—ICCSA 2012, LNCS 7335, Springer, pp 730–742 https://doi.org/10.1007/978-3-642-31137-6
Baek S-J, Ko J-W, Kim G-J, Han J-S, Song Y-J (2012) Goal-heuristic analysis method for an adaptive process mining. In: Proceedings of the international conference on IT convergence and security 2011, LNEE 120, pp 409–418. Springer. https://doi.org/10.1007/978-94-007-2911-7_37
Ballou RH, Gilbert SM, Mukherjee A (2000) New managerial challenges from supply chain opportunities. Ind Mark Manage 29(1):7–18. https://doi.org/10.1016/S0019-8501(99)00107-8
Baum LE, Petrie T, Soules G, Weiss N (1970) A maximization technique occurring in the statistical analysis of probabilistic functions of Markov chains. Ann Math Stat 41(1):164–171. https://doi.org/10.1214/aoms/1177697196
Bernard G, Andritsos P (2017) CJM-ex: Goal-oriented exploration of customer journey maps using event logs and data analytics. In: BPM demo track and BPM dissertation award (BPM-D&DA 2017), CEUR-WS Vol-1920 (paper 172)
Bernard G, Andritsos P (2017) A process mining based model for customer journey mapping. In: Proceedings of the forum and doctoral consortium papers presented at the 29th international conference on advanced information systems engineering (CAiSE 2017). CEUR-WS vol 1848. pp 46–56
Blei DM, Ng AY, Jordan MI (2003) Latent dirichlet allocation. J Mach Learn Res 3:993–1022
Bresciani P, Perini A, Giorgini P, Giunchiglia F, Mylopoulos J (2004) Tropos: an agent-oriented software development methodology. Auton Agent Multi-Agent Syst 8(3):203–236. https://doi.org/10.1023/B:AGNT.0000018806.20944.ef
Buijs JC, van Dongen B, van der Aalst WMP (2013) Mining configurable process models from collections of event logs. In: Business process management 2013, LNCS 8094, pp 33–48, Springer. https://doi.org/10.1007/978-3-642-40176-3_5
Cailliau A, van Lamsweerde A (2014) Integrating exception handling in goal models. In: Requirements engineering conference (RE), 2014 IEEE 22nd International, pp 43–52. IEEE CS. https://doi.org/10.1109/re.2014.6912246
Cho M, Song M, Comuzzi M, Yoo S (2017) Evaluating the effect of best practices for business process redesign: an evidence-based approach based on process mining techniques. Decis Support Syst 104:92–103. https://doi.org/10.1016/j.dss.2017.10.004
Chung L, Nixon BA, Yu E, Mylopoulos J (2012) Non-functional requirements in software engineering. In: International series in software engineering (Vol 5). Springer. https://doi.org/10.1007/978-1-4615-5269-7
Cook JE, Wolf AL (1995) Process discovery and validation through event-data analysis. In: ICSE’95—Proceedings of the 17th international conference on software engineering. ACM, pp 73–82
Cook JE, Wolf AL (1998) Discovering models of software processes from event-based data. ACM Trans Softw Eng Methodol 7(3):215–249. https://doi.org/10.1145/287000.287001
Dąbrowski J (2017) Towards an adaptive framework for goal-oriented strategic decision-making. In: Requirements engineering conference (RE), 2017 IEEE 25th international. IEEE, pp 538–543 https://doi.org/10.1109/re.2017.53
Dabrowski J, Kifetew FM, Muñante D, Letier E, Siena A, Susi A (2017) Discovering requirements through goal-driven process mining. In: 2017 IEEE 25th international requirements engineering conference workshops REW, IEEE, pp 199–203 https://doi.org/10.1109/rew.2017.61
Dees M, de Leoni M, Mannhardt F (2017) Enhancing process models to improve business performance: a methodology and case studies. In: Panetto H, Debruyne C, Gaaloul W, Papazoglou M, Paschke A, Ardagna CA, Meersman R (eds) OTM confederated international conferences “On the move to meaningful internet systems”. Springer, Cham, pp 232–251. https://doi.org/10.1007/978-3-319-69462-7_15
Deneckère R, Hug C, Khodabandelou G, Salinesi C (2014) Intentional process mining: discovering and modeling the goals behind processes using supervised learning. Int J Inf Syst Model Design (IJISMD) 5(4):22–47. https://doi.org/10.4018/ijismd.2014100102
Dowson M (1987) Iteration in the software process; review of the 3rd international software process workshop. In: ICSE’87 - proceedings of the 9th international conference on software engineering, pp 36–41. IEEE CS
EDImine (2011) EDImine—mining inter-organizational business processes. Retrieved from http://edimine.ec.tuwien.ac.at/
El Kharbili M, de Medeiros AKA, Stein S, van der Aalst WM (2008) Business process compliance checking: current state and future challenges. In: Modellierung betrieblicher Informationssysteme (MobIS 2018), LNI 141, pp 107–113. GI-Edition
Epure EV, Hug C, Deneckère R, Brinkkemper S (2013) Intention-mining: a solution to process participant support in process aware information systems. Technical Report 2013-020, Department of Information and Computing Sciences, Utrecht University, The Netherlands
Epure EV, Hug C, Deneckère R, Brinkkemper S (2014) What shall I do next? Intention mining for flexible process enactment. Advanced information systems engineering LNCS, vol 8484. Springer, Cham, pp 473–487. https://doi.org/10.1007/978-3-319-07881-6_32
Fahland D, van der Aalst WMP (2015) Model repair—aligning process models to reality. Inf Syst 47:220–243. https://doi.org/10.1016/j.is.2013.12.007
Feldt R, Magazinius A (2010) Validity threats in empirical software engineering research-an initial survey. In: SEKE 2010—proceedings of the 22nd international conference on software engineering and knowledge engineering. KSI Research Inc, pp 374–379
Flapper SDP, Fortuin L, Stoop PPM (1996) Towards consistent performance management systems. Int J Oper Prod Manag 16(7):27–37. https://doi.org/10.1108/01443579610119144
Fluxicon (2016). Disco. Retrieved from fluxicon.com/disco/
Forney GD (1973) The viterbi algorithm. Proc IEEE 61(3):268–278. https://doi.org/10.1109/PROC.1973.9030
Georgeff M, Rao A (1998) Rational software agents: from theory to practice. In: Agent technology—foundations, applications, and markets. Springer, pp 139–160. https://doi.org/10.1007/978-3-662-03678-5_8
Ghanavati S, Amyot D, Peyton L (2011) A systematic review of goal-oriented requirements management frameworks for business process compliance. In: 2011 fourth international workshop on Requirements engineering and law (RELAW), IEEE CS. pp 25–34https://doi.org/10.1109/relaw.2011.6050270
Ghasemi M (2018) Towards goal-oriented process mining. In: Requirements engineering conference (RE), IEEE 26th international. IEEE CS, pp 484–489 https://doi.org/10.1109/re.2018.00066
Ghasemi M (2018) What requirements engineering can learn from process mining. In: 1st international workshop on learning from other disciplines for requirements engineering (D4RE), IEEE CS, pp 8–11. https://doi.org/10.1109/d4re.2018.00008
Ghasemi M, Amyot D (2016) Process mining in healthcare: a systematised literature review. Int J Electron Healthcare 9(1):60–88. https://doi.org/10.1504/IJEH.2016.078745
Groen EC, Seyff N, Ali R, Dalpiaz F, Doerr J, Guzman E, Hosseini M, Marco J, Oriol M, Perini A, Stade M (2017) The crowd in requirements engineering: the landscape and challenges. IEEE Softw 34(2):44–52. https://doi.org/10.1109/ms.2017.33
Gurgen Erdogan T, Tarhan A (2018) A goal-driven evaluation method based on process mining for healthcare processes. Appl Sci 8(6):894. https://doi.org/10.3390/app8060894
Hallerbach A, Bauer T, Reichert M (2010) Capturing variability in business process models: the Provop approach. J Softw Main Evol Res Practice 22(6–7):519–546. https://doi.org/10.1002/smr.v22:6/7
Hammer M, Champy J (1993) Reengineering the corporation: a manifesto for business revolution. Zondervan. https://doi.org/10.1016/s0007-6813(05)80064-3
Hartigan JA, Wong MA (1979) Algorithm AS 136: a k-means clustering algorithm. J R Stat Soc Ser C Appl Stat, 28(1), 100–108. https://doi.org/10.2307/2346830
Horita H, Hirayama H, Tahara Y, Ohsuga A (2015) Towards goal-oriented conformance checking. In: 27th international conference on software engineering and knowledge engineering (SEKE 2015), KSI Research Inc, pp 722–724
Horkoff J, Aydemir FB, Cardoso E, Li T, Maté A, Paja E, Salnitri M, Piras L, Mylopoulos J, Giorgini P (2017) Goal-oriented requirements engineering: an extended systematic mapping study. Require Eng 1–28. https://doi.org/10.1007/s00766-017-0280-z
Horkoff J, Barone D, Jiang L, Yu E, Amyot D, Borgida A, Mylopoulos J (2014) Strategic business modeling: representation and reasoning. Softw Syst Model 13(3):1015–1041. https://doi.org/10.1007/s10270-012-0290-8
Horkoff J, Li T, Li F-L, Salnitri M, Cardoso E, Giorgini P, Mylopoulos J (2015) Using goal models downstream: a systematic roadmap and literature review. Int J Inf Syst Model Design (IJISMD) 6(2):1–42. https://doi.org/10.4018/IJISMD.2015040101
Hornix P (2007) Performance analysis of business processes through process mining. Master’s thesis, Eindhoven University of Technology, The Netherlands
ITU-T (2012) Recommendation Z.151 (10/12): User Requirements Notation (URN)—language definition. http://www.itu.int/rec/T-REC-Z.151/en
Johann T, Maalej W (2015) Democratic mass participation of users in requirements engineering? In: Requirements engineering conference (RE), 2015 IEEE 23rd international. IEEE CS, pp 256–261 https://doi.org/10.1109/re.2015.7320433
Khodabandelou G (2013) Contextual recommendations using intention mining on process traces: Doctoral consortium paper. In: IEEE seventh international conference on research challenges in information science (RCIS). IEEE CS, pp 1–6. https://doi.org/10.1109/rcis.2013.6577728
Khodabandelou G (2014) Mining intentional process models. Doctoral dissertation, University of Paris-Est, France
Khodabandelou G, Hug C, Deneckère R, Salinesi C (2013) Process mining versus intention mining. In: Nurcan S, Proper HA, Soffer P, Krogstie J, Schmidt R, Halpin T, Bider I (eds) Enterprise, business-process and information systems modeling. LNBIP, vol 147. Springer. Berlin, Heidelberg, pp 466–480. https://doi.org/10.1007/978-3-642-38484-4_33
Khodabandelou G, Hug C, Deneckère R, Salinesi C (2013) Supervised intentional process models discovery using Hidden Markov models. In: IEEE seventh international conference on research challenges in information science (RCIS). IEEE CS, pp 1–11. https://doi.org/10.1109/rcis.2013.6577711
Khodabandelou G, Hug C, Deneckère R, Salinesi C (2014) Supervised vs. unsupervised learning for intentional process model discovery. In: Bider I, Gaaloul K, Krogstie J, Nurcan S, Proper HA, Schmidt R, Soffer P (eds) Enterprise, business-process and information systems modeling LNBIP, vol 175. Springer, Berlin, Heidelberg, pp 215–229. https://doi.org/10.1007/978-3-662-43745-2_15
Khodabandelou G, Hug C, Deneckère R, Salinesi C (2014) Unsupervised discovery of intentional process models from event logs. In: Proceedings of the 11th working conference on mining software repositories—MSR 2014. ACM Press, pp 282–291. https://doi.org/10.1145/2597073.2597101
Khodabandelou G, Hug C, Salinesi C (2014) A novel approach to process mining: Intentional process models discovery. In: 2014 IEEE eighth international conference on research challenges in information science (RCIS), IEEE CS, pp 1–12 https://doi.org/10.1109/rcis.2014.6861040
Khodabandelou G, Hug C, Salinesi C (2015) Mining users’ intents from logs. Int J Inf Syst Model Design (IJISMD) 6(2):43–71. https://doi.org/10.4018/IJISMD.2015040102
Kingston J, Schafer B, Vandenberghe W (2004) Towards a financial fraud ontology: a legal modelling approach. Artificial Intell Law 12(4):419–446. https://doi.org/10.1007/s10506-005-4163-0
Kitchenham B, Pearl Brereton O, Budgen D, Turner M, Bailey J, Linkman S (2009) Systematic literature reviews in software engineering—a systematic literature review. Inf Softw Technol 51(1):7–15. https://doi.org/10.1016/j.infsof.2008.09.009
Kraiem N, Kaffela H, Dimassi J, Al Khanjari Z (2014) Mapping from MAP models to BPMN processes. J Softw Eng 8(4):252–264. https://doi.org/10.3923/jse.2014.252.264
Krathu W, Engel R, Pichler C, Zapletal M, Werthner H (2013) Identifying inter-organizational key performance indicators from EDIFACT messages. In: 2013 IEEE 15th conference on business informatics, IEEE CS, pp 276–283. https://doi.org/10.1109/cbi.2013.46
Krathu W, Pichler C, Engel R, Zapletal M, Werthner H, Huemer C (2014) A framework for inter-organizational performance analysis from EDI messages. In: 2014 IEEE 16th conference on business informatics. IEEE CS. vol 1, pp 17–24 https://doi.org/10.1109/cbi.2014.19
Lapouchnian A, Yu Y, Mylopoulos J (2007) Requirements-driven design and configuration management of business processes. In: Business process management, LNCS 4714, Springer, pp 246–261 https://doi.org/10.1007/978-3-540-75183-0_18
Li J, Liu D, Yang B (2007) Process mining: extending α-algorithm to mine duplicate tasks in process logs. In: Advances in web and network technologies, and information management, LNCS 4537, Springer, pp 396–407 https://doi.org/10.1007/978-3-540-72909-9_43
Liu L, Yu ESK (2004) Designing information systems in social context: a goal and scenario modelling approach. Inf Syst 29(2):187–203. https://doi.org/10.1016/S0306-4379(03)00052-8
Ly LT, Maggi FM, Montali M, Rinderle-Ma S, van der Aalst WM (2015) Compliance monitoring in business processes: functionalities, application, and tool-support. Inf Syst 54:209–234. https://doi.org/10.1016/j.is.2015.02.007
Maalej W, Nayebi M, Johann T, Ruhe G (2016) Toward data-driven requirements engineering. IEEE Softw 33(1):48–54. https://doi.org/10.1109/ms.2015.153
Malinova M, Dijkman R, Mendling J (2013) Automatic extraction of process categories from process model collections. In: Business process management workshops, LNBIP 171, Springer, pp 430–441 https://doi.org/10.1007/978-3-319-06257-0_34
Maxwell JC, Antón AI, Swire P, Riaz M, McCraw CM (2012) A legal cross-references taxonomy for reasoning about compliance requirements. Requirements Eng 17(2):99–115. https://doi.org/10.1007/s00766-012-0152-5
Mikolov T, Chen K, Corrado G, Dean J (2013) Efficient estimation of word representations in vector space. arXiv preprint arXiv:1301.3781
Object Management Group (2011) Business process model and notation (BPMN), Version 2.0. Formal/2011-01-03
Outmazgin N (2012) Exploring workaround situations in business processes. In: International conference on business process management, Springer, Berlin, pp 426–437 https://doi.org/10.1007/978-3-642-36285-9_45
Outmazgin N, Soffer P (2016) A process mining-based analysis of business process work-arounds. Softw Syst Model 15(2):309–323. https://doi.org/10.1007/s10270-014-0420-6
Papadimitriou D, Koutrika G, Mylopoulos J, Velegrakis Y (2016) The goal behind the action: toward goal-aware systems and applications. ACM Trans Database Syst 41(4), Article 23. https://doi.org/10.1145/2934666
Pitman MA (1998) Qualitative research design: an interactive approach. Anthropol Education Quarterly 29(4):499–501. https://doi.org/10.1525/aeq.1998.29.4.499
Poelmans S (1998) Coping strategies and distributed viscosity in a workflow management system: a case study. In: Workshop on adaptive workflow systems, Seattle, USA, November (8 pages)
Poelmans S (1999) Workarounds and distributed viscosity in a workflow system: a case study. ACM SIGGROUP Bulletin 20(3):11–12. https://doi.org/10.1145/605610.605618
Poels G, Decreus K, Roelens B, Snoeck M (2013) Investigating goal-oriented requirements engineering for business processes. J Database Manag 24(2):35–71. https://doi.org/10.4018/jdm.2013040103
Ponnalagu K, Ghose A, Narendra NC, Dam HK (2015) Goal-aligned categorization of instance variants in knowledge-intensive processes. In: Business process management, LNCS 9253, Springer, pp 350–364 https://doi.org/10.1007/978-3-319-23063-4
Pourshahid A, Amyot D, Peyton L, Ghanavati S, Chen P, Weiss M, Forster AJ (2009) Business process management with the User Requirements Notation. Electron Commerce Res 9(4):269–316. https://doi.org/10.1007/s10660-009-9039-z
ProM Tools (2016). Retrieved from http://www.promtools.org/doku.php
Rabiner L, Juang B (1986) An introduction to hidden Markov models. IEEE ASSP Magazine 3(1):4–16. https://doi.org/10.1109/MASSP.1986.1165342
Rabiner LR (1989) A tutorial on hidden Markov models and selected applications in speech recognition. Proc IEEE 77(2):257–286. https://doi.org/10.1109/5.18626
Reijers HA, Mansar SL (2005) Best practices in business process redesign: an overview and qualitative evaluation of successful redesign heuristics. Omega 33(4):283–306. https://doi.org/10.1016/j.omega.2004.04.012
Rolland C, Prakash N, Benjamen A (1999) A multi-model view of process modelling. Requirements Eng 4(4):169–187. https://doi.org/10.1007/s007660050018
Rolland C, Salinesi C (2005) Modeling goals and reasoning with them. Engineering and managing software requirements, Springer, Berlin, pp 189–217 https://doi.org/10.1007/3-540-28244-0_9
Rozinat A, van der Aalst WMP (2008) Conformance checking of processes based on monitoring real behavior. Inf Syst 33(1):64–95. https://doi.org/10.1016/j.is.2007.07.001
Rubin VA, Mitsyuk AA, Lomazova IA, van der Aalst WM (2014) Process mining can be applied to software too! In: Proceedings of the 8th ACM/IEEE international symposium on empirical software engineering and measurement. ACM, p 57. https://doi.org/10.1145/2652524.2652583
Saiedian H, Kumarakulasingam P, Anan M (2005) Scenario-based requirements analysis techniques for real-time software systems: a comparative evaluation. Requirements Eng 10(1):22–33. https://doi.org/10.1007/s00766-004-0192-6
Santiputri M, Deb N, Khan MA, Ghose A, Dam H, Chaki N (2017) Mining goal refinement patterns: distilling know-how from data. In: International conference on conceptual modeling, Springer, Cham, pp 69–76 https://doi.org/10.1007/978-3-319-69904-2_6
Snijders R, Dalpiaz F, Hosseini M, Shahri A, Ali R (2014) Crowd-centric requirements engineering. In: Proceedings of the 2014 IEEE/ACM 7th international conference on utility and cloud computing, IEEE Computer Society, pp 614–615 https://doi.org/10.1109/ucc.2014.96
Soffer P (2013) A state-based intention driven declarative process model. Int J Inf Syst Model Design (IJISMD) 4(2):44–64. https://doi.org/10.4018/jismd.2013040103
Spoletini P, Ferrari A (2017) Requirements elicitation: a look at the future through the lenses of the past. In: Requirements engineering conference (RE), 2017 IEEE 25th international, IEEE CS, pp 476–477 https://doi.org/10.1109/re.2017.35
Sutcliffe A (2003) Scenario-based requirements engineering. In: 11th IEEE international requirements engineering conference, IEEE CS, pp 320–329 https://doi.org/10.1109/icre.2003.1232776
Sutcliffe AG, Maiden NA, Minocha S, Manuel D (1998) Supporting scenario-based requirements engineering. IEEE Trans Softw Eng 24(12):1072–1088. https://doi.org/10.1109/32.738340
Taghiabadi ER, Fahland D, van Dongen BF, van der Aalst WM (2013) Diagnostic information for compliance checking of temporal compliance requirements. In: International conference on advanced information systems engineering, Springer, Berlin, pp 304–320 https://doi.org/10.1007/978-3-642-38709-8_20
Tran H, Zdun U, Dustdar S (2008) Modeling human aspects of business processes–a view-based, model-driven approach. In: Schieferdecker I, Hartman A (eds) Model driven architecture-foundations and applications. LNCS, vol 5095. Springer. Berlin, Heidelberg, pp 246–261. https://doi.org/10.1007/978-3-540-69100-6_17
van der Aalst WMP (2011) Process mining: discovery, conformance and enhancement of business processes. Springer, Berlin. https://doi.org/10.1007/978-3-642-19345-3
van der Aalst WMP (2012) What makes a good process model? Softw Syst Model 11(4):557–569. https://doi.org/10.1007/s10270-012-0265-9
van der Aalst WMP (2016) Process mining data science in action (2nd edn), Springer, Berlin. https://doi.org/10.1007/978-3-642-19345-3
van der Aalst W, Adriansyah A, van Dongen B (2012) Replaying history on process models for conformance checking and performance analysis. Wiley Interdisciplinary Reviews: Data Mining and Knowledge Discovery 2(2):182–192. https://doi.org/10.1002/widm.1045
van der Aalst WMP, Weijters T, Maruster L (2004) Workflow mining: discovering process models from event logs. IEEE Trans Knowl Data Eng 16(9):1128–1142. https://doi.org/10.1109/TKDE.2004.47
van Dongen B, Alves de Medeiros K, Verbeek HMW, Weijters JMM, van der Aalst WMP (2005) The ProM framework: a new era in process mining tool support. In: Application and theory of petri nets 2005, LNCS 3536, Springer, pp 444–454 https://doi.org/10.1007/11494744_25
van Lamsweerde A (2001) Goal-oriented requirements engineering: a guided tour. In: RE’01 proc. of the fifth IEEE international symposium on requirements engineering, IEEE CS, pp 249–261 https://doi.org/10.1109/isre.2001.948567
van Lamsweerde A (2004) Goal-oriented requirements engineering: a roundtrip from research to practice. In: Proc 12th IEEE international requirements engineering conference, 2004, IEEE CS, pp 4–7 https://doi.org/10.1109/icre.2004.1335648
van Lamsweerde A (2008) Requirements engineering: from craft to discipline. In: Proceeding SIGSOFT’08/FSE-16, ACM, pp 238–249 https://doi.org/10.1145/1453101.1453133
van Lamsweerde A, Darimont R, Letier E (1998) Managing conflicts in goal-driven requirements engineering. IEEE Trans Softw Eng 24(11):908–926. https://doi.org/10.1109/32.730542
van Lamsweerde A, Letier E (2000) Handling obstacles in goal-oriented requirements engineering. IEEE Trans Softw Eng 26(10):978–1005. https://doi.org/10.1109/32.879820
Wang J, Wong RK, Ding J, Guo Q, Wen L (2013) Efficient Selection of Process Mining Algorithms. IEEE Tran Services Comput 6(4):484–496. https://doi.org/10.1109/TSC.2012.20
Weijters AJMM, Ribeiro JJTS (2011) Flexible heuristics miner (FHM). In: 2011 IEEE symposium on computational intelligence and data mining (CIDM), IEEE CS, pp 310–317 https://doi.org/10.1109/cidm.2011.5949453
Xu X, Jin T, Wei Z, Lv C, Wang J (2016) TCPM: topic-based clinical pathway mining. In: Connected health: applications, systems and engineering technologies (CHASE), 2016 IEEE first international conference on, IEEE CS, pp 292–301 https://doi.org/10.1109/chase.2016.17
Xu X, Jin T, Wei Z, Wang J (2017) Incorporating topic assignment constraint and topic correlation limitation into clinical goal discovering for clinical pathway mining. J Healthcare Eng, 2017. https://doi.org/10.1155/2017/5208072
Yan J, Hu D, Liao SS, Wang H (2014) Mining agents’ goals in agent-oriented business processes. ACM Trans Manag Inf Syst 5(4):1–22. https://doi.org/10.1145/2629448
Yu E (1995) Modelling strategic relationships for process reengineering. Doctoral dissertation, University of Toronto, Canada
Zeni N, Kiyavitskaya N, Mich L, Cordy JR, Mylopoulos J (2015) GaiusT: supporting the extraction of rights and obligations for regulatory compliance. Requirements Eng 20(1):1–22. https://doi.org/10.1007/s00766-013-0181-8
Acknowledgements
This work is funded by the Discovery grant program of the National Science and Engineering Council of Canada (NSERC). M. Ghasemi is further sponsored by the Ontario Graduate Scholarship program and the NSERC Canada Graduate Scholarship program. The authors are indebted to the anonymous reviewers for their feedback and suggestions for improvement.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ghasemi, M., Amyot, D. From event logs to goals: a systematic literature review of goal-oriented process mining. Requirements Eng 25, 67–93 (2020). https://doi.org/10.1007/s00766-018-00308-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00766-018-00308-3